7 Remote Working Security Risks | How to Safely Work Remotely
Working remotely has many benefits, such as flexibility, comfort, and productivity. However, it also exposes you to various security threats that can compromise your data and devices. In this blog post, we will explore the most common security challenges that remote workers encounter and how to overcome them. By applying these best practices, you can work remotely with security and confidence.
Here are 3 key points to remember:
- Remote workers face threats including phishing, malware, device theft, network breaches, and data leaks.
- To protect yourself and your work from these risks, you should use a password manager, install antivirus software, password protect your devices, use a VPN, secure your home wifi, create strong passwords for everything, and enable two-factor authentication.
- TeamPassword is a tool that can help you manage and share your passwords securely with your remote team.
Table of Contents
Remote Working Security Risks: Identifying the Culprits
Remote work exposes you to some security risks that you may not encounter in a traditional office environment, or at the very least are accentuated in a remote environment. Here are some of the most common security threats that remote workers face:
- Phishing: Threat actors send fraudulent emails or messages that look like they come from legitimate sources, such as your bank, your employer, or your colleagues. The goal is to trick you into clicking on malicious links or attachments, or providing sensitive information such as passwords or credit card details.
- Malware: This is any software that is designed to harm or disrupt your computer or device. Malware can infect your device through phishing emails, malicious websites, or unsecured downloads. Malware can steal your data, damage your files, spy on your activities, or take control of your device.
- Device theft: Someone physically steals your laptop, smartphone, tablet, or any other device that you use for remote work. Device theft can result in the loss of your data and access to your accounts. It can also compromise the security of your employer or clients if you have sensitive or confidential information on your device.
- Network breaches: Threat actors gain unauthorized access to your network or Wi-Fi connection. Network breaches can happen when you use public or unsecured Wi-Fi networks, such as those in cafes, hotels, or airports. Hackers can intercept your online traffic, steal your data, or inject malware into your device.
- Data leaks: This is when your data is accidentally or intentionally exposed to unauthorized parties. Data leaks can happen when you use unencrypted or weak passwords, share passwords with others, store data on unsecured cloud services, or send data via unsecured channels. If you find yourself in this situation, you may find our in-depth guide on what to do if you've been hacked helpful.
How to Safely Work Remotely
Remote working security risks are real and serious, but you can avoid them. You just need to follow some simple and effective steps to secure your data and device. Here are some of the best practices for remote work security:
1. Use a Password Manager
A password manager helps you create, store, and manage your passwords securely. It makes strong and unique passwords for each of your accounts and saves them in a secure vault. It also fills in your passwords automatically when you log in to websites or apps. This way, you don't have to remember or type your passwords.
For remote distributed teams, a secure password manager designed for sharing is crucial.
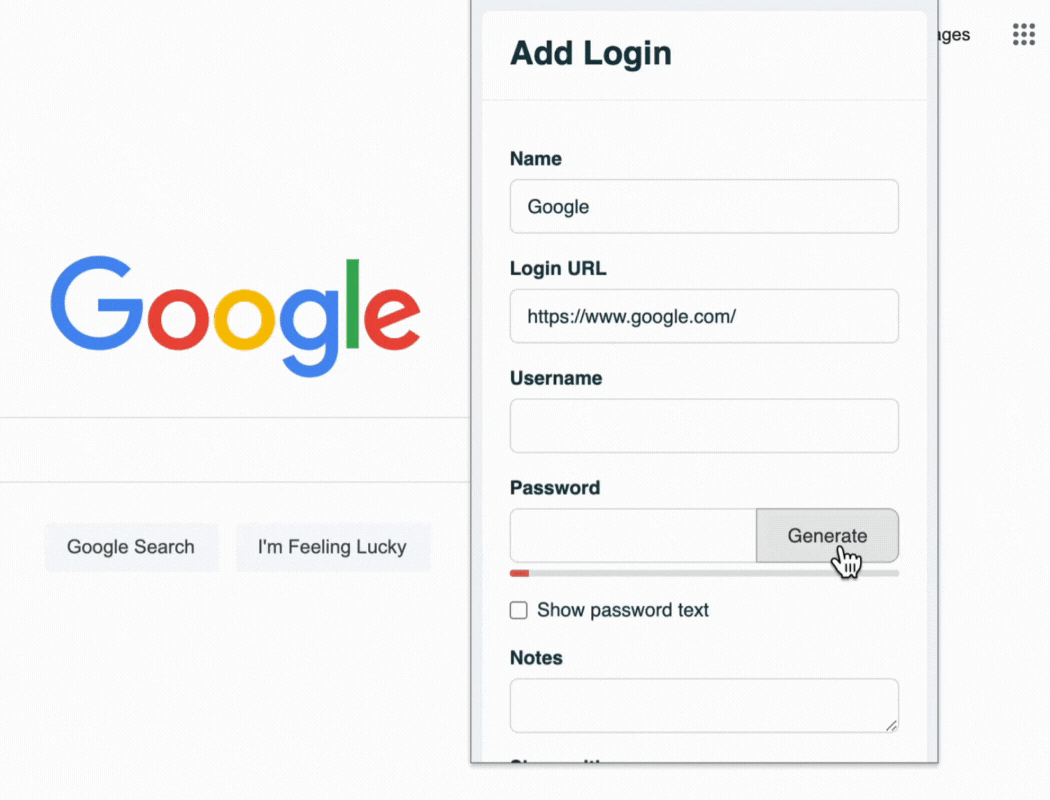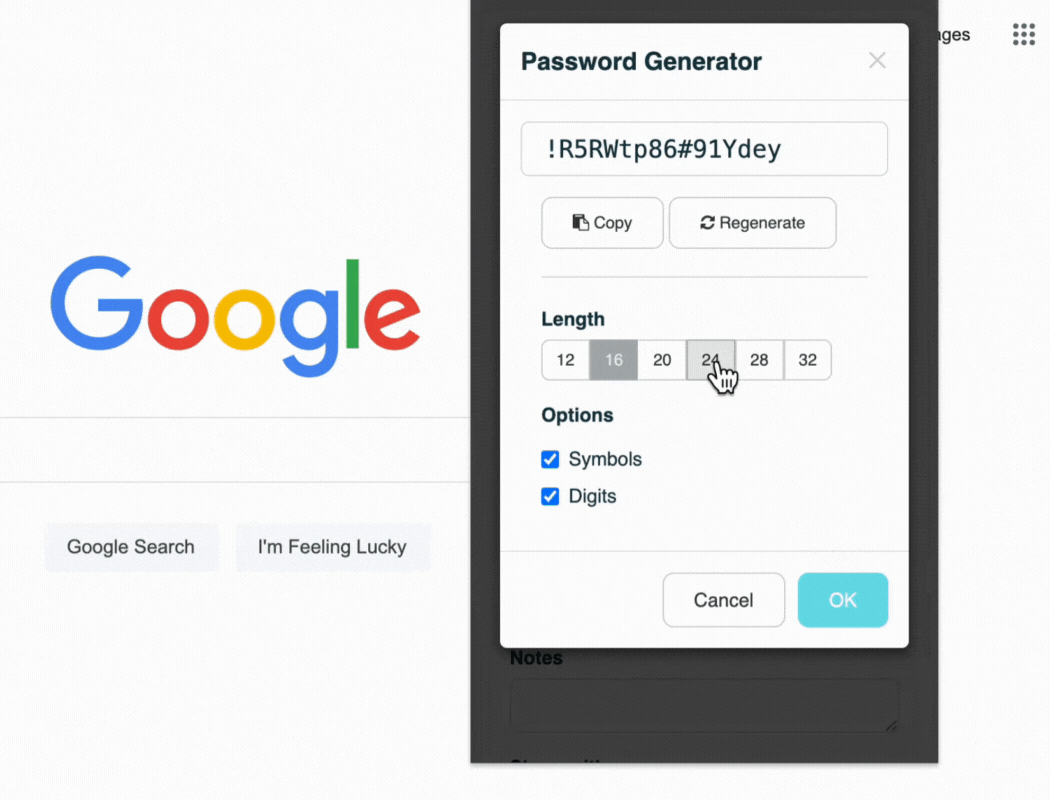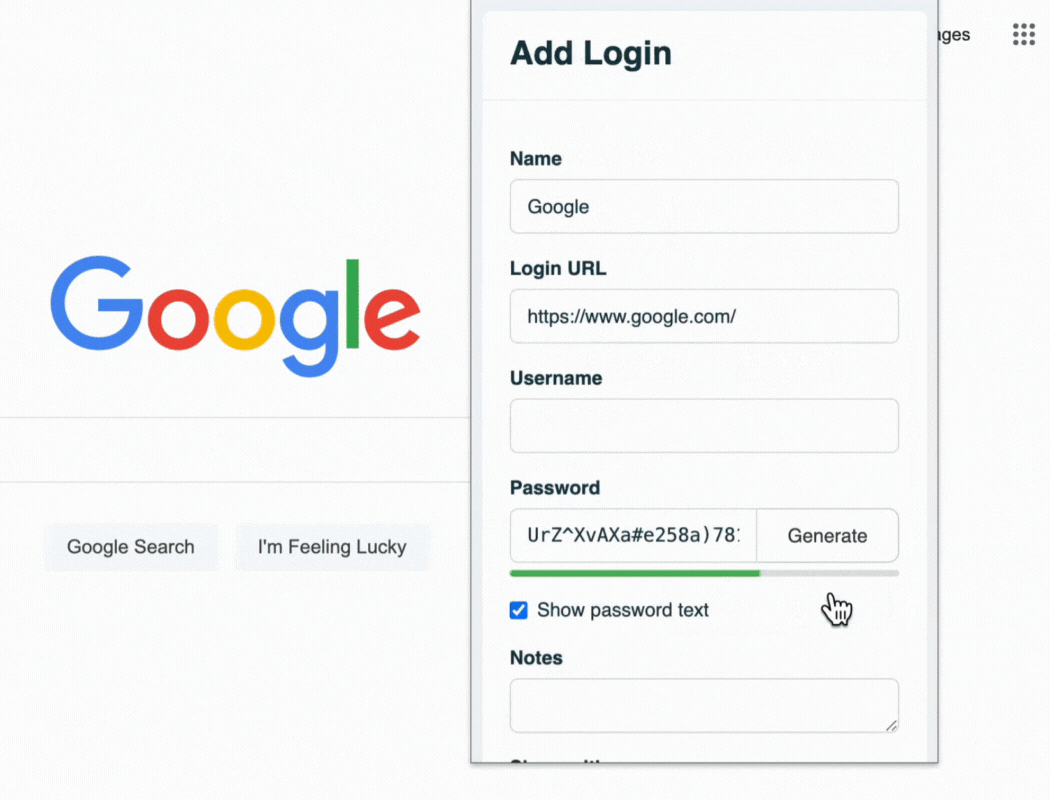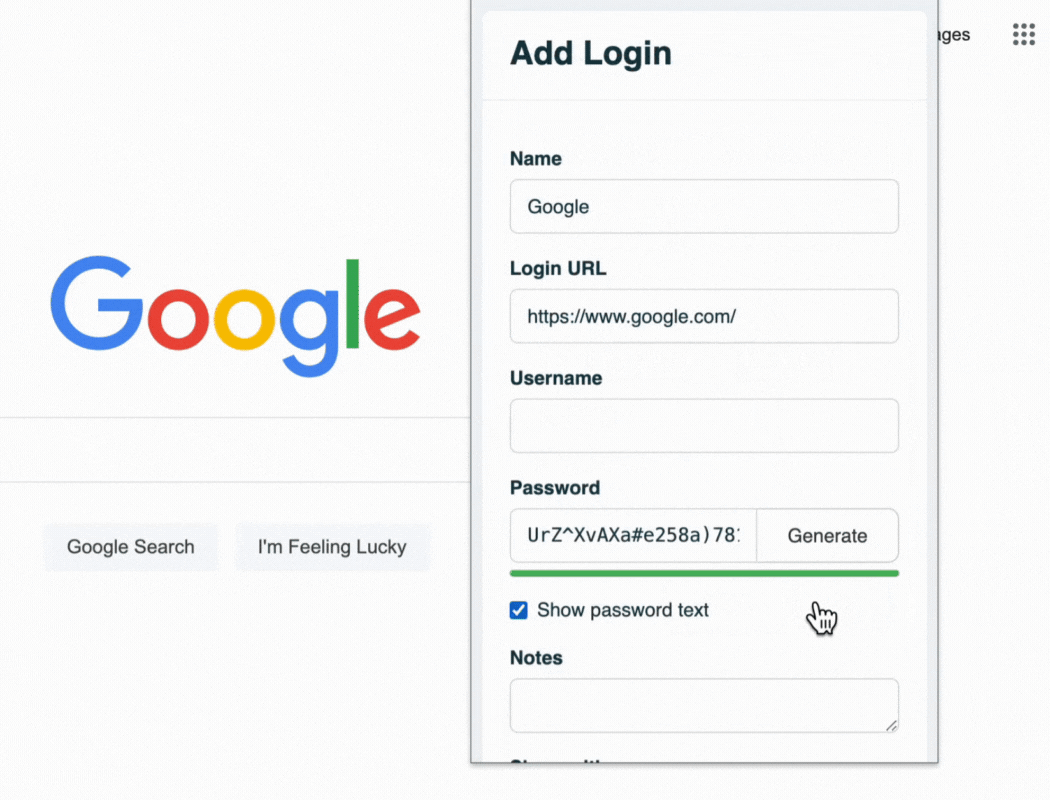
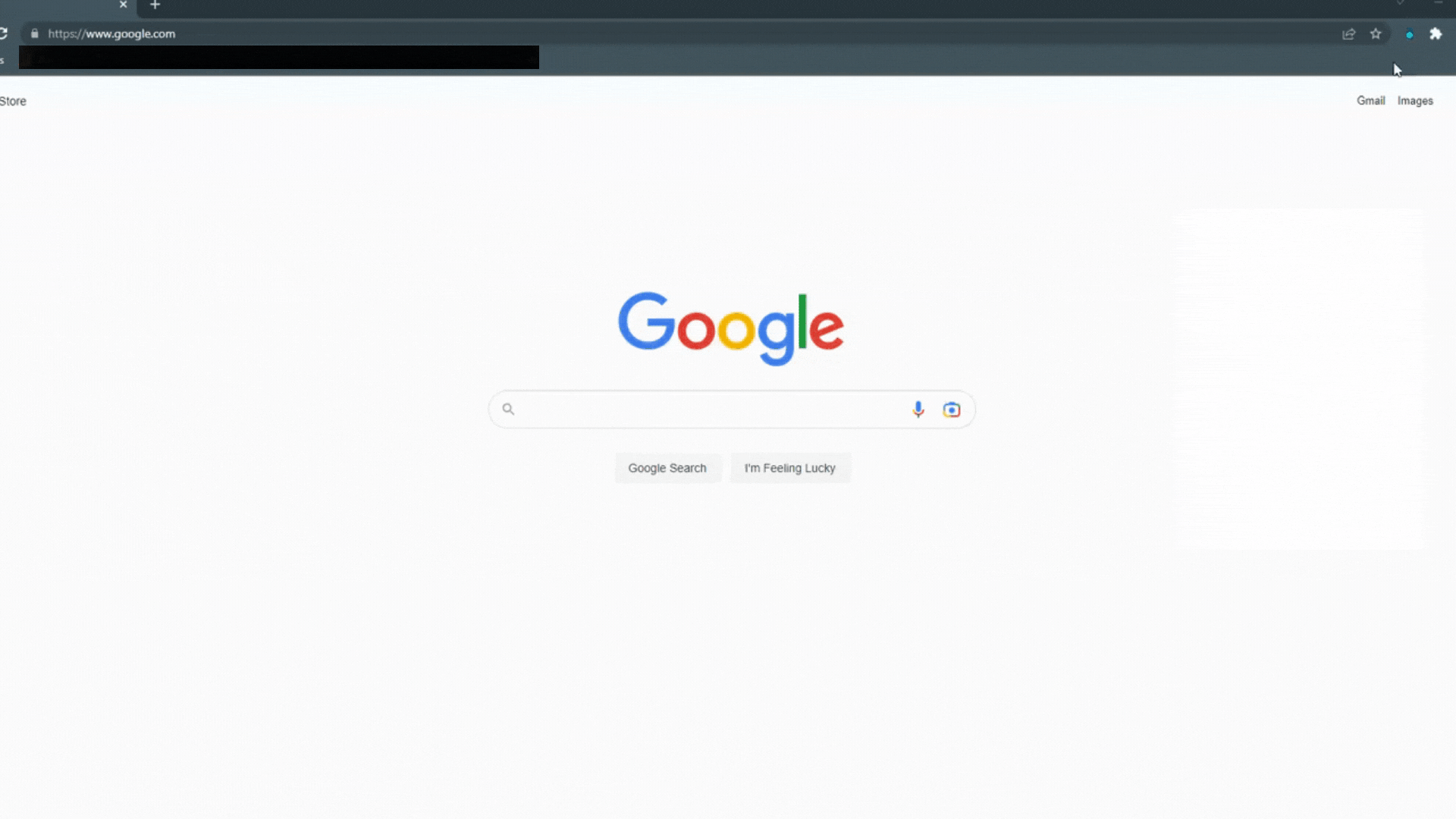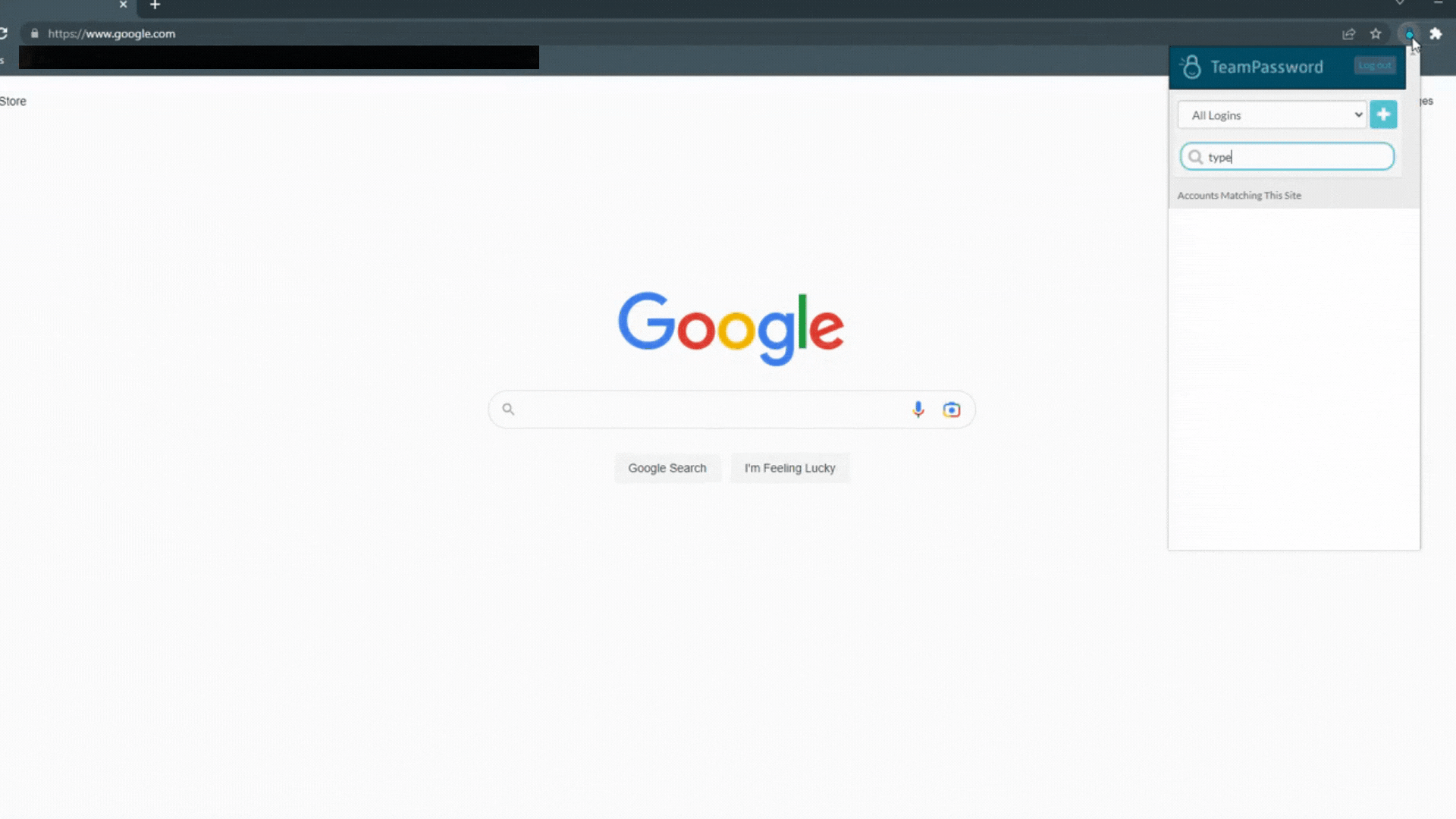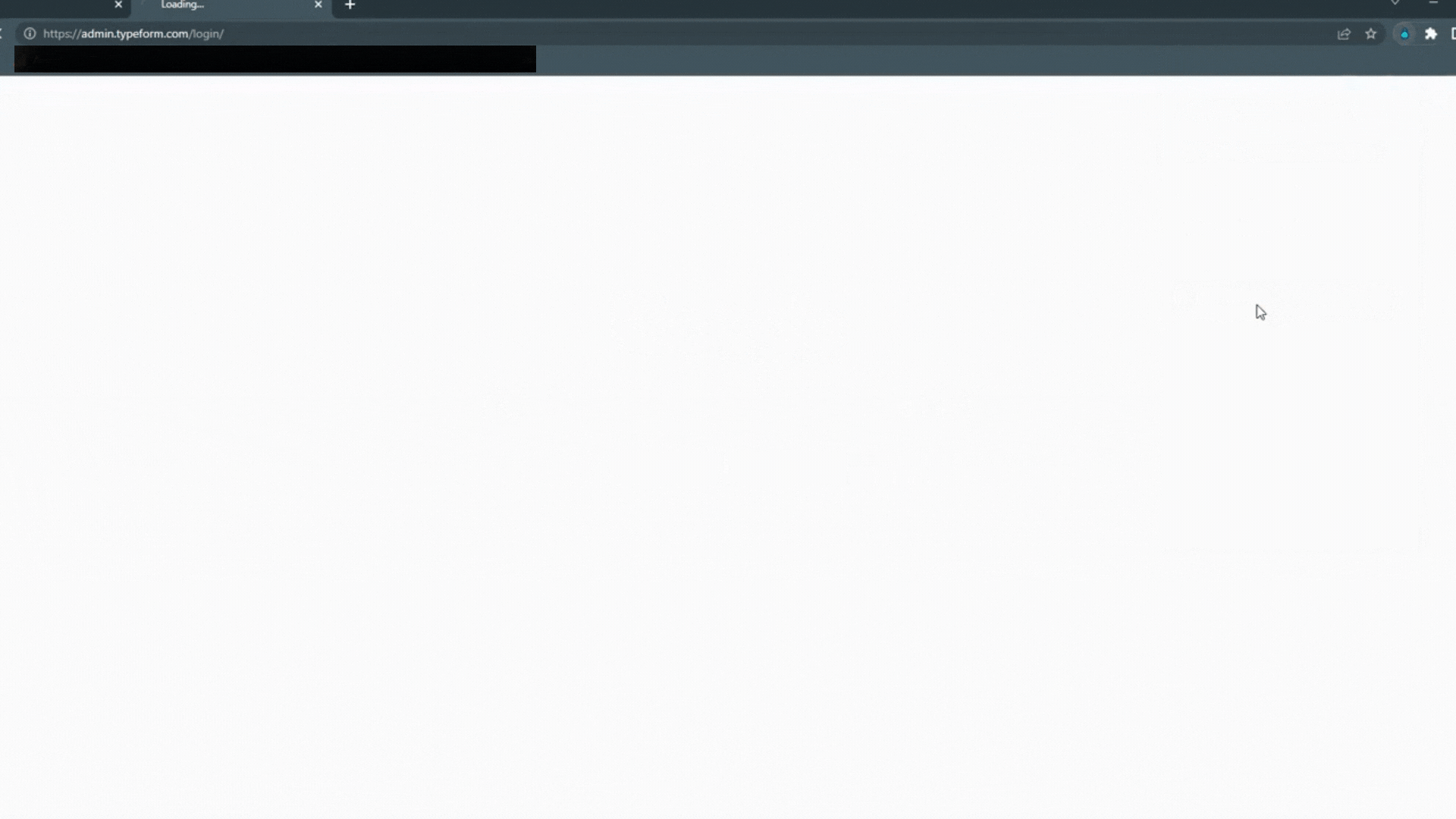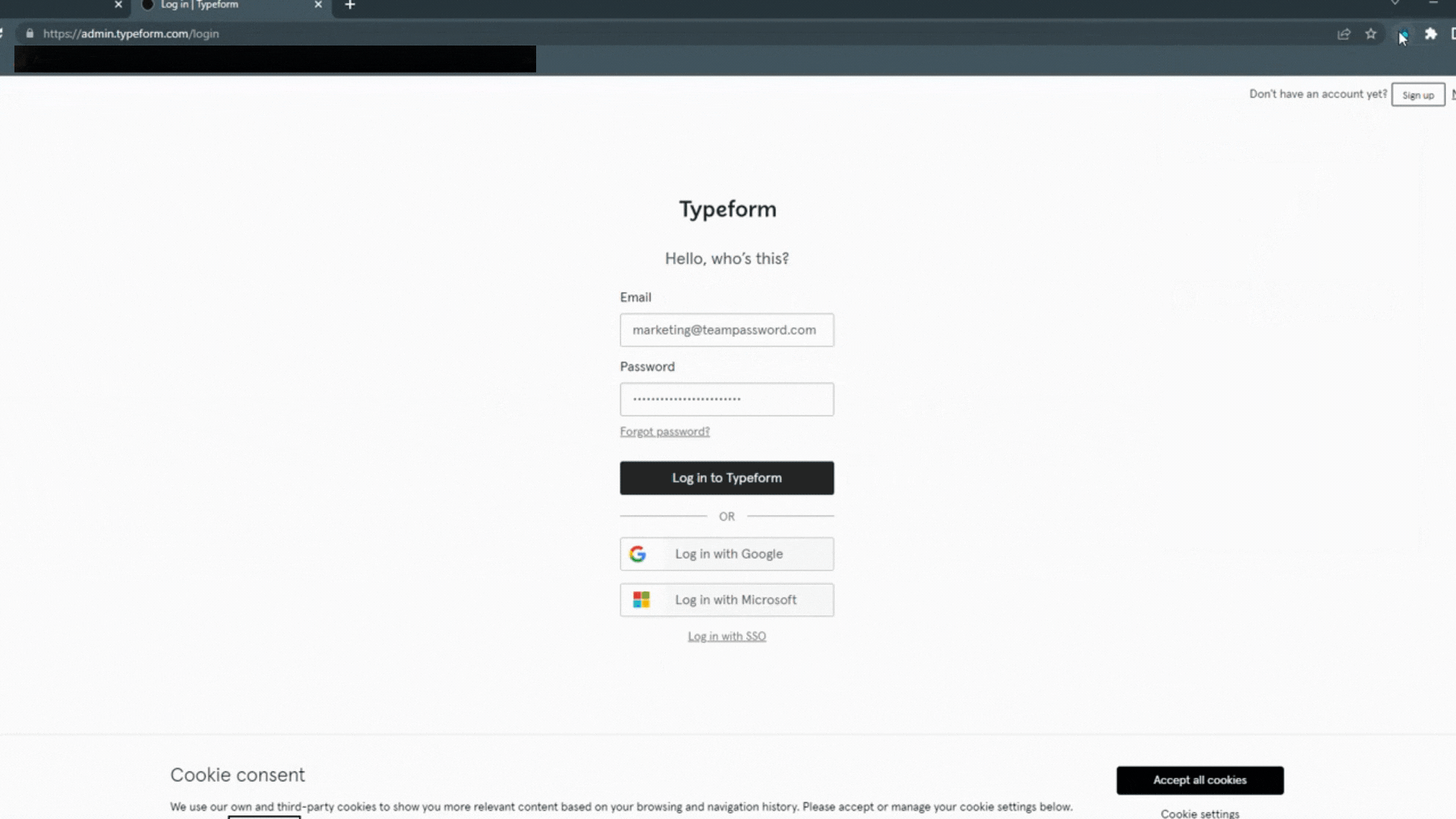
TeamPassword's built-in password generator
Password managers improve your remote work security in many ways. It stops you from using weak or repeated passwords that hackers can easily guess or crack. It also protects you from phishing attacks by only filling in passwords on real websites. And it lets you access your passwords from any device or location.
2. Install Comprehensive Security Software
Modern security software does far more than traditional antivirus functions. It provides multi-layered protection against various threats through real-time scanning of files, programs, and websites for malware detection. These solutions offer proactive defense against ransomware and zero-day exploits while monitoring your network to identify suspicious connection attempts. Additionally, they help detect phishing websites, filter fraudulent communication, and scan email attachments before they can cause harm.
High-quality security software is essential for remote work because it serves as your first line of defense against evolving cyber threats. When selecting a solution, prioritize options with automatic, frequent updates to protect against emerging threats. Look for software that uses minimal system resources to maintain productivity, offers cross-device protection for all work endpoints, and includes advanced features like secure browsing and password management.
3. Implement Strong Device Authentication
Modern device authentication creates robust security barriers that go well beyond simple passwords. At minimum, use strong passcodes or passwords with at least 12 characters incorporating complexity. Whenever possible, enable biometric security such as fingerprint, facial recognition, or iris scanning for an additional layer of protection. For critical systems and accounts, implement two-factor authentication that requires a second verification method beyond your password.
Configure your devices to auto-lock after brief periods of inactivity and limit the number of failed login attempts to prevent brute force attacks. This comprehensive authentication approach is crucial because it prevents unauthorized access to sensitive company information if your device is lost or stolen. It also enables remote device management capabilities, including location tracking and remote wiping. Strong authentication serves as your final defense layer when other security measures fail and helps you comply with organizational and regulatory security requirements.
4. Deploy a Business-Grade VPN
A Virtual Private Network creates an encrypted tunnel between your device and the internet, offering critical security protection during remote work. This encryption prevents interception and man-in-the-middle attacks while masking your IP address to protect your actual location and identity. VPNs provide secure access to company resources and internal networks even when working from home or while traveling.
For professional remote work, consider a business-grade VPN rather than consumer options. Business VPNs typically offer dedicated servers with guaranteed bandwidth for improved performance and support split tunneling to route only sensitive traffic through the VPN. They employ advanced encryption protocols like WireGuard, OpenVPN, or IKEv2 while providing centralized management and security policy enforcement. Unlike many consumer options, business VPNs typically don't log user activities or connection data, providing greater privacy and security.
5. Secure Your Home Network Infrastructure
A comprehensively secured home network begins with proper router configuration. Set up strong WPA3 or WPA2-PSK AES encryption (avoiding outdated WEP and TKIP protocols) and create unique, complex admin credentials different from your Wi-Fi password. Maintain regular firmware updates to patch security vulnerabilities and disable potentially exploitable features like remote management and WPS.
Your network configuration should include a hidden SSID to prevent broadcasting to nearby devices and MAC address filtering to allow only trusted devices to connect. Consider creating a separate guest network for non-work devices and visitors to isolate them from your work environment. Always ensure your firewall is activated with appropriate port management for the applications you use.
For additional security, consider changing default DNS servers to enhance privacy, implementing network monitoring to detect unauthorized devices, and performing regular security audits to identify potential vulnerabilities. These combined measures create a secure foundation for your remote work environment that significantly reduces the risk of network-based attacks.
6. Create Strong Passwords for Everything
Another security measure for remote work is to use strong passwords for all your accounts and services. A strong password has at least 12 characters and contains a combination of uppercase and lowercase letters, numbers, and symbols. It does not include any personal or common information, such as names, dates, words, or phrases.
Strong passwords prevent hackers from cracking or guessing them and reduce the chance of data breaches or identity theft. If you're beholden to security compliance standards like SOC 2, it's essential for you to follow password best practices.
A password manager can help you create and manage strong passwords. Easy-to-use browser extensions, such as the one demonstrated below, enable your team to use strong passwords without sacrificing convenience.
7. Enable Two-Factor Authorization
You should also enable two-factor authentication on all your accounts and services. This adds an extra layer of security when you log in. You have to enter not only your password but also a code that you receive on your phone, email, or app, or a device that you plug in or scan. This way, hackers can't access your account even if they know your password. Two-factor authorization also helps you recover your account if you forget your password or lose your device.
Using TeamPassword to Enhance Remote Work Security
TeamPassword is a password manager that is designed specifically for teams and businesses that work remotely.
Here are some of the key features and benefits of TeamPassword:
- Security: TeamPassword uses industry-standard encryption to protect your passwords and data. It also offers enforceable 2FA, SSO, activity logs, admin and member permission levels, and more.
- Simplicity: TeamPassword is easy to use and set up. You can create groups for different teams or projects and add users with a few clicks. You can also import or export passwords from other sources or formats.
- Integration: Use browser extensions and mobile apps to access your passwords from anywhere.
- Support: TeamPassword offers live support - you can contact us anytime via email or chat if you have any questions or issues.
Using TeamPassword has many benefits for remote work security. It helps you avoid the hassle of creating and remembering passwords for each of your team accounts and services. It also helps you prevent password sharing via email, chat, or text, which can expose your passwords to hackers or third parties. And it helps you monitor and manage who has access to what passwords and revoke access when needed.
Prevent Remote Security Risks with TeamPassword
TeamPassword is the best password manager for remote, collaborative teams. Don’t believe us? Sign up for a 14-day free trial today and try for yourself!