What is a brute force attack and are you at risk?
A brute force attack is a hacking method that involves systematically guessing login credentials, encryption keys, or other hidden information through trial and error. Hackers attempt every possible combination of characters until they find the correct one.
The term "brute force" reflects the approach: rather than using sophisticated techniques, attackers rely on sheer persistence, making repeated attempts to break into an account.
Despite being one of the oldest hacking methods, brute force attacks remain common today. Depending on password strength and the computing power available, these attacks can take anywhere from a few seconds to an impossibly long time—potentially even longer than the age of the universe.
To prevent brute force and related attacks, you need to ensure your team is using long, complex, and random passwords. This is best accomplished using a password manager.
TeamPassword keeps your passwords safe, organized, and makes it easy to follow password best practices.
Sign up today for a free 14-day TeamPassword trial and protect your company's digital assets from cybercriminals.
Table of Contents
Types of brute force and related attacks
While a traditional brute force attack is straightforward—systematically cycling through all possible combinations of characters—the reality is that most modern attacks are more sophisticated. Although, in theory, a password like "password" is just as secure as "aT./$x6m" in a raw brute force scenario, attackers often combine brute force techniques with others, making commonly used or reused passwords significantly more vulnerable. Below are some of the most common types of brute force and related attacks used today:
1. Simple Brute Force Attacks
A simple brute force attack systematically tries every possible combination of characters until the correct one is found. Imagine your password is restricted to six lowercase letters. A simple brute force attack would begin with "aaaaaa," then "aaaaab," continuing sequentially until it tries "zzzzzz." While this method is unsophisticated, it is exhaustive and will eventually crack the password if given enough time and computing power. However, for longer, more complex passwords, this method quickly becomes impractical.
2. Dictionary Attacks
A dictionary attack improves on the basic brute force approach by focusing on likely passwords rather than trying every possible combination. Attackers use precompiled lists of common passwords—often sourced from previous data breaches—such as "password123," "qwerty," or "letmein." Since many users choose simple or common passwords, a dictionary attack can be far more efficient than a simple brute force attack.
3. Hybrid Brute Force Attacks
A hybrid brute force attack combines elements of both dictionary and brute force methods. It begins by using a dictionary of common words or phrases but then modifies those entries by adding numbers, special characters, or capitalization. For example, after trying "password," it might then try "Password1!" or "password1234." This approach takes advantage of the fact that many users create predictable variations of common passwords, making it a highly effective method of attack.
4. Reverse Brute Force Attacks
In a reverse brute force attack, the hacker starts with a known password or set of passwords, often obtained from previous breaches, and tries them across a wide range of possible usernames or accounts. This method can be devastating, especially when people reuse passwords across different platforms, as attackers may only need one correct match to compromise multiple accounts.
5. Credential Stuffing
Credential stuffing is a form of attack where hackers use lists of username and password pairs, often obtained from data breaches, to attempt to gain unauthorized access to accounts. Because many people reuse passwords across multiple websites and services, credential stuffing can be highly effective. The attacker doesn't need to guess the password—they already have a valid pair; they just need to find where it works.
Sign up for a 14-day free trial so TeamPassword can empower your team with strong passwords today!
Tools that Aid Brute Force Attempts
It goes without saying that this isn’t being discussed to encourage password cracking, but just to see exactly what you are up against when trying to secure a network. Hackers have created an entire ecosystem of tools to aid them in their nefarious actions, and you should be aware of them to appreciate just how hard it is to maintain a secure network.
Automated tools help with brute force attacks.
Instead of manually entering every possible password, it is unsurprising that hackers have created automated software to run their brute force attacks. These automated programs can run through dictionary attacks as well.
Many of these tools have workarounds to work against computer protocols (e.g., MySQL and Telnet), hack wireless routers, decrypt passwords in encrypted storage, translate words to different forms (e.g., password, p4ssw0rd, and Pa55WoRd), and identify weak passwords.
Some tools can scan pre-compute rainbow tables.
A rainbow table is a pre-computed table for caching the output of cryptographic hash functions, usually for cracking password hashes. Thus, scanning rainbow tables removes the hardest part of the brute force attack to speed up the rate of cracking.
GPU Speeds Brute Force Attempts
Brute force attacks require a huge amount of computation. GPUs can do this work much more easily than CPUs, so many brute-force software packages enable the use of GPUs.
Combining the CPU and GPU
Combining CPUs and GPUs accelerates computing power even further. GPUs can process parallelizable processes incredibly quickly. That is, any computing process that can be broken down into many smaller components to be run at the same time can be done across the thousands of computing cores in the GPU at a rapid pace. With this method. Hackers can crack passwords about 250 times faster than a CPU alone.
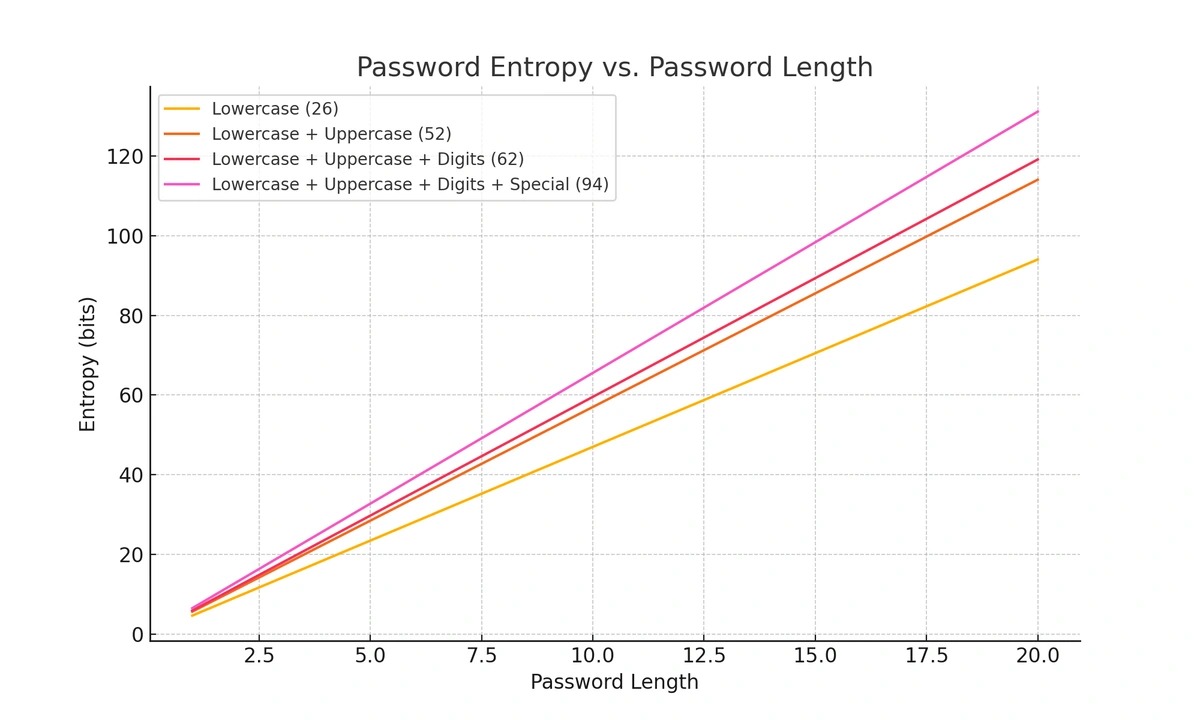
How effective is a complex password against a brute force attack?
Brute force attacks can be thwarted by long, complex passwords. However, that doesn’t mean you are entirely without vulnerability just because you force users on your network to pick complex passwords.
Let’s assume you make everyone on your network choose a password with a minimum length of 12 characters with at least one lowercase letter, uppercase letter, number, and special character. That is, it meets the following requirements:
Lowercase letter {abcdefghijklmnopqrstuvwxyz}
Uppercase letter {ABCDEFGHIJKLMNOPQRSTUVWXYZ}
Number {0123456789}
Character {!@#$%^&*()_+{}|:"<>?~`-=[]\;',./}
This is very effective against a brute force attack: to crack that password by trying 20,000,000,000 attempts per second, which can be accomplished using a cloud computing platform, would take an average of 3,300 years. But is that enough?
Although it would prevent a pure, simple brute force attack, if a hybrid brute force attack were used instead, then it would depend on how unique the password is as well. If your employee chooses the password “Password-123”, then chances are it will be found in the dictionary prelude to the brute force attack, and a hacker will be on your network in seconds.
What do hackers gain from Brute Force Attacks?
Brute force attacks are not cheap. Either the hackers need to own a huge computing service or pay for that server time. Alternatively, they might spend years developing a botnet to carry out the attack. So, where is the payoff? Well, hackers can profit in many different ways:
- Profiting from ads or collecting activity data
- Stealing personal data and valuables
- Spreading malware to cause disruptions
- Hijacking your system for malicious activity
- Ruining a website’s reputation
How can you reduce your risk of brute force attacks?
Protecting yourself against brute force attacks is critical, especially as these methods continue to evolve. Fortunately, making yourself a more challenging target is often enough to deter attackers, who tend to prioritize easy targets like users with passwords such as "12345678." By implementing the following strategies, you can significantly reduce your risk.
1. Create Longer Passwords with Varied Characters
The length and complexity of your password are key factors in defending against brute force attacks. Always use passwords that are at least 12 characters long, and incorporate a mix of:
- Lowercase and uppercase letters
- Numbers
- Special characters (e.g., @, $, %, *)
For example, instead of using something simple like "Password123," opt for something much harder to guess, such as "X7mZ#91f$WplQ8". The added complexity makes it significantly more difficult for hackers to crack via brute force, especially if they are restricted by rate-limiting mechanisms.
2. Use Elaborate Passphrases
For even greater security, consider using passphrases—long strings of random or semi-random words combined with special characters and numbers. Passphrases are generally easier to remember but still offer strong protection because of their length. For instance, instead of a short, simple password like "H3ll0#," try something like:
- Example passphrase: "hello.MY-nAmE/15_what"
This passphrase is not only lengthy, but the inclusion of special characters and varied capitalization makes it significantly harder for brute force or dictionary attacks to crack.
3. Avoid Commonly Used Passwords
One of the simplest ways to protect yourself is to stay away from commonly used passwords, such as "password," "123456," or "qwerty." Hackers rely heavily on these in dictionary attacks, knowing that many users default to simplicity. Instead, create passwords that are both complex and unique—hackers can crack either a common or simple password in seconds.
4. Use Unique Passwords for Every Account
Using the same password across multiple sites greatly increases your vulnerability. If one account is compromised in a data breach, attackers can use that password in credential stuffing attacks to gain access to your other accounts. To prevent this, never reuse passwords—especially for critical accounts like email, banking, or any service that stores sensitive data.
- Scenario: Imagine your password is compromised on a gaming site like Fortnite. If that same password is used for your online banking, attackers could use it to drain your bank account, turning a minor annoyance into a major security breach.
5. Regularly Remove Unused Accounts
Unused or old accounts pose a significant security risk. Former employees, accounts with elevated privileges, or simply abandoned profiles can be exploited by attackers. Regularly audit your accounts and remove any that are no longer in use—especially those with administrative or high-level access. This reduces the number of potential entry points for attackers.
6. Use a Password Manager
One of the most effective ways to improve password security is by using a password manager. These tools help you generate, store, and manage complex, unique passwords for all your accounts, ensuring you don’t have to remember dozens of long strings.
A password manager can:
- Automatically generate strong, unique passwords for each account
- Store them securely so you don’t need to memorize them
- Ensure that even if one password is compromised, your other accounts remain safe
For example, TeamPassword helps your team collaborate securely by generating and sharing strong passwords without the risk of reuse or weak passwords. This fosters a culture of proactive cybersecurity within your organization, drastically reducing the risk of brute force attacks.
- Enforceable Two-Factor Authentication (2FA): Add an extra layer of protection by requiring 2FA for all users, ensuring that even if passwords are compromised, unauthorized access is prevented.
- AES 256-bit Vault Encryption: All passwords are stored with industry-leading AES 256-bit encryption, keeping your sensitive information secure from any potential breach.
- Activity Logs: Monitor and track who is accessing which passwords with detailed activity logs, helping you maintain oversight and accountability across your team.
- User-Friendly Interface: Simplified password management that doesn’t compromise on security, making it easy for your team to adopt and use every day.
- Competitive pricing: TeamPassword is easy to use and easy to afford - pick a plan that works for your team.
By implementing these strategies, you can not only protect yourself against brute force attacks but also enhance your overall cybersecurity hygiene, making your accounts and data far less vulnerable to hacking attempts.
Sign up for a 14-day free trial to test TeamPassword with your team members today.
Enhance your password security
The best software to generate and have your passwords managed correctly.