What is password encryption and how does it work?
Password encryption is essential to store user credentials stored in a database securely. Without password encryption, anyone accessing a user database on a company's servers (including hackers) could easily view any stored passwords.
Even a strong 32-character password created using a secure password generator is useless without password-encryption! If someone can read your password on a server, they can use it simply by copy/pasting it—no matter how long or complicated the password might be!
Encryption scrambles your password before saving it on the server. So, if someone hacks the server, instead of finding password123, they find a random series of letters and numbers.
In this article, we're going to explore the world of password encryption, why strong passwords matter, and how you can practice better password management!
TeamPassword is the password management solution for small businesses! Create, store, and share login credentials safely with employees, contractors, and clients. Sign up for a 14-day free trial today!
Table of Contents
Understanding Password Encryption
To explain password encryption effectively, we must first grasp the language. Several terms might be unfamiliar, so here is a quick intro to password encryption terminology.
- Key: Used to lock and unlock passwords using a random string of bits. You get private and public keys that crypt and decrypt data differently, but we won't get too deep in the weeds with keys!
- Bits: A logical state with one of two possible values, including 1/0, true/false, yes/no, or on/off as typical examples.
- Block (block cipher): A deterministic algorithm operating on fixed-length groups of bits, called blocks.
- Hash function: The algorithm that uses the key to create password encryption and decryption. A hash function is essentially a piece of code that runs every time someone saves a password or logs into an application.
- Hash: A random series of numbers and letters representing your password. The hash function uses your hash instead of the raw password for authentication.
- Salt: Additional letters and numbers appended to the hash
How Does Password Encryption Work?
When you create a new account, your chosen password undergoes a transformation process to protect its integrity. A hash function, a mathematical algorithm, converts your password into a seemingly random string of characters called a hash. This hash is stored on the server, never the original password itself. For example:
- Original password: Pa$$w0rd123
- Hashed password: 6AF1CE202340FE71BDB914AD5357E33A6982A63B
To authenticate your identity, the system recreates the hash of your entered password upon login. If this newly generated hash matches the stored hash, the system grants access. This one-way encryption process ensures that even if a hacker steals the hash, they cannot reverse it to obtain your original password.
How Salt Works
While hashing provides a foundational layer of security, it's not infallible.
The hash function only creates a unique hash for each password, not each user. So, if multiple users have the password, Pa$$w0rd123, the hash will be exactly the same.
To overcome this encryption vulnerability, engineers salt passwords so each hash is unique, even if the passwords are identical.
A salt appends a unique value of 8 bytes (16 characters) to the password before the hash function creates a hash. This way, even identical passwords are unique before the hash function.
For example:
- Two identical passwords: Pa$$w0rd123
- Salt value one: E1F53135E559C253
- Salt value two: 84B03D034B409D4E
- Password one before hash: Pa$$w0rd123E1F53135E559C253
- Password two before hash: Pa$$w0rd12384B03D034B409D4E
- Password one hashed value (SHA256): 72AE25495A7981C40622D49F9A52E4F1565C90F048F59027BD9C8C8900D5C3D8
- Password two hashed value (SHA256): B4B6603ABC670967E99C7E7F1389E40CD16E78AD38EB1468EC2AA1E62B8BED3A
Remember: Even with strong encryption, creating complex and unique passwords remains fundamental for personal online security.
Beyond Salting: Advanced Password Protection
Salting is an essential step, but modern security protocols employ more sophisticated techniques to fortify password protection.
- Key Stretching: This method increases the computational effort required to calculate a hash by iterating the hashing process multiple times. Algorithms like bcrypt and Argon2 are commonly used for key stretching, making brute-force attacks exponentially more difficult.
- Password Storage Formats: Secure password storage formats, such as those defined by the Password Hashing Competition (PHC), provide standardized and robust methods for storing hashed passwords. These formats often incorporate key stretching, salting, and other countermeasures.
- Multi-Factor Authentication (MFA): While not directly related to password encryption, MFA adds an extra layer of security by requiring additional forms of verification, such as a code sent to your phone or biometric data.
- Password Managers: These tools generate strong, unique passwords for each account and store them securely, reducing the risk of password reuse and breaches.
By combining these elements, organizations can create a robust password defense strategy that protects user accounts from unauthorized access. It's crucial to stay updated on the latest security best practices to safeguard sensitive information in an ever-evolving threat landscape.
5 Common Password Encryption Methods
1. Data Encryption Standard (DES)
While applications no longer use Data Encryption Standard (DES), it's important to mention this password encryption method because of its history and influence on more secure modern standards.
IBM developed DES as a 56-bit encryption technology in the early 1970s. The NSA adopted and improved DES before it was approved worldwide as the encryption standard.
However, since the late 70s, hackers have been able to break DES encrypted passwords. In 1999, ethical hackers managed to break a DES key in under 24 hours.
To make DES more secure, engineers created Triple DES and later Advanced Encryption Standard (AES), which we still use today.
2. Triple DES
Triple DES uses three 56-bit keys (blocks) to create 168-bit encryption (some security experts argue that Triple DES is only 112 bits strong). Although Triple-DES is slowly being phased out, many financial institutions still use it to encrypt ATM PINs.
3. Advanced Encryption Standard (AES)
AES is the new encryption standard—trusted by the United States Government and many other prominent organizations globally. At 128 bits, AES is sufficiently secure, but most organizations prefer heavy-duty 256-bit encryption.
At TeamPassword, we use 256-bit encryption to store passwords, ensuring the highest levels of security for our clients. We're also a secure hosting provider holding multiple security accreditations.
Hackers can only break an AES encrypted password through a brute-force attack—trying password combinations to find the right one.
To counter brute-force attacks, applications will lock an account after a certain number of attempts or use tools like Google's reCAPTURE.
4. Blowfish
American cryptographer, Bruce Schneier, designed Blowfish in 1993 as an antidote to the weak DES encryption. Blowfish uses a 64-bit block and variable key length of 32 to 448 bits.
Although Blowfish is more robust than its DES predecessor, the 64-bit block is still vulnerable to attacks, most commonly birthday attacks—a cryptographic attack that exploits the mathematics behind the algorithm.
To solve Blowfish vulnerabilities, engineers created Twofish in 1998 (128-bit blocks with 256-bit keys) and Threefish in 2008 (256, 516, 1024-bit blocks with 256, 516, 1024-bit keys).
5. Rivest-Shamir-Adleman (RSA)
RSA is one of the oldest and widely used to transfer data securely. The encryption works with two keys, two large prime numbers, and an additional auxiliary value.
Due to the complicated encrypting and decrypting process, there is no known method for breaking RSA encryption.
Although widely used for transferring data, RSA is slow and not suitable for password encryption.
Why Strong Passwords Matter
Password encryption can only prevent criminals from viewing saved credentials stored on a server—but cannot prevent hackers from guessing weak/commonly used passwords. If you reuse the same password for multiple accounts, this also puts you at risk!
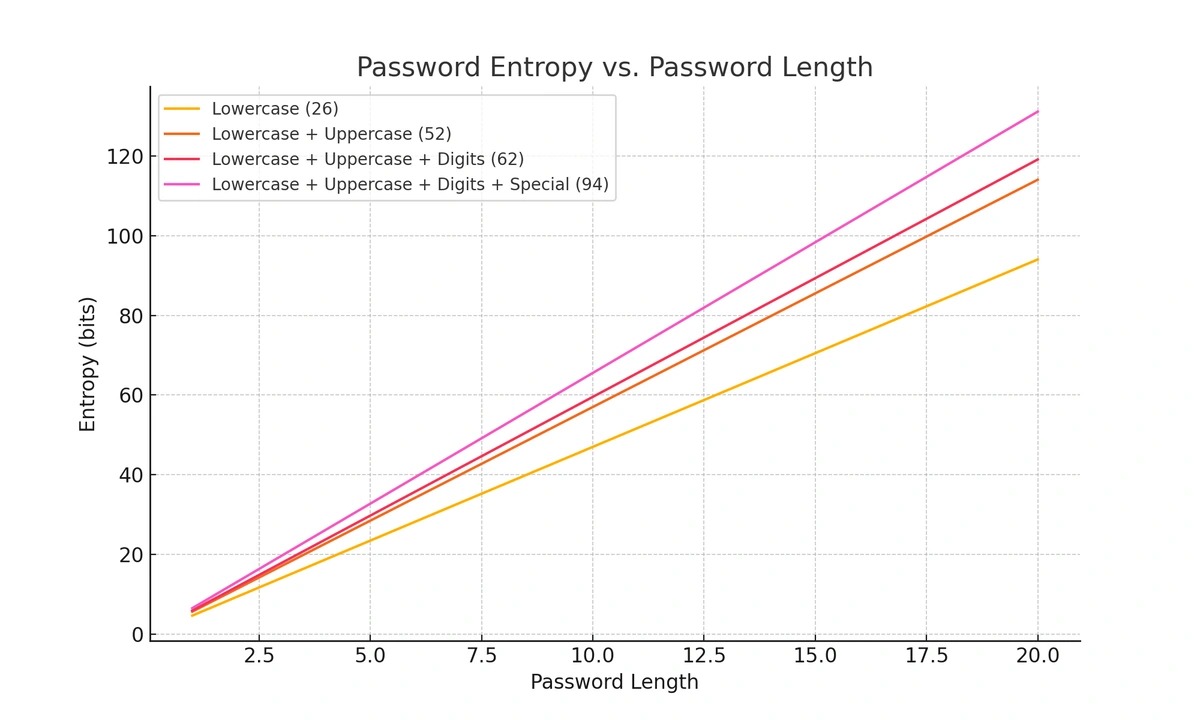
Encryption is most effective when users create robust, unique passwords for every account. For example, a random 32-character password with letters, numbers, and special characters hashed and salted is near impossible to guess or decode, even using a computer!
In another scenario, let's assume you have a strong 32-character password, but you use it for every account. If hackers manage to steal that password, they have access to every account using the same credentials! Your strong password is effectively useless.
Improving Your Password Management
Now that you understand password encryption and the associated vulnerabilities, you can see why strong passwords are essential.
Effective password management is crucial to protect yourself against cyberattacks or in the highly likely event of a data breach where hackers steal your credentials.
Criminals are after the low-hanging fruit—people who use weak passwords!
5 tips for creating stronger passwords:
- Create strong passwords for every account. The easiest way to do this is using a password generator. TeamPassword has a free password generator anyone can use to create passwords from 12-32 characters using uppercase, lowercase, numbers, and special characters. We recommend creating passwords as long as the application will allow.
- Never create passwords shorter than eight characters, with 12 being our recommended minimum.
- Never reuse the same password for multiple accounts.
- Never create passwords with your name, family member's names, or pet's names. With social media, this information is freely available. Criminals can add those names to algorithms for brute-force attacks.
- Don't store passwords in digital notepads or spreadsheets. We recommend using a password manager like TeamPassword to create and store your credentials.
Why You Need a Password Manager like TeamPassword
We have so many accounts these days; it's almost impossible to create unique, memorable, secure passwords for each one. A password manager solves this problem.
Instead of remembering the credentials for every account, you only need to memorize the one to log into your password manager.
TeamPassword keeps all of your credentials safely stored and encrypted, so you never have to memorize a password again. Instead of entering your credentials, you use one of TeamPassword's browser extensions (Chrome, Firefox, and Safari) to log into accounts.
Built for Teams
TeamPassword's best feature is its ability to share credentials with team members securely. Instead of sharing passwords, you provide access through TeamPassword.
Employees use TeamPassword to log in, meaning you never share raw passwords—no more worrying about unauthorized access or sharing.
You can create groups in TeamPassword to share access with employees, clients, contractors, and freelancers. When someone no longer needs access, remove them from the group with a single click. No need to change passwords every time someone leaves a project!
Built-In Password Generator
TeamPassword features a built-in secure password manager so you can create robust passwords for every account. TeamPassword also ensures you never reuse the same credentials so that you won't fall victim to credential stuffing attacks!
With a built-in password generator, you can change passwords regularly, and TeamPassword will update the new credentials for all users!
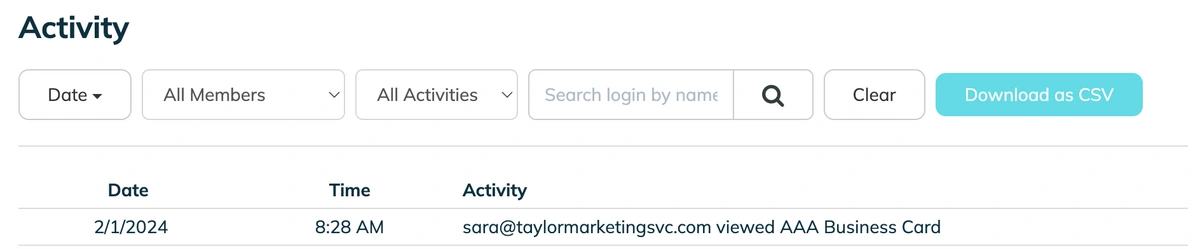
Monitor Login Activity
TeamPassword's activity log keeps track of every action across all of your accounts—logins, password changes, new team members, sharing access, and more.
You can also set up email notifications for all TeamPassword actions so that you can react fast to any suspicious activity.
Get Your Free TeamPassword Trial
Password encryption is not enough to protect your business from password vulnerabilities! You need a robust password manager like TeamPassword to create, store, and share credentials securely.
Sign up for a 14-day free trial and let TeamPassword secure your company's digital assets.
Enhance your password security
The best software to generate and have your passwords managed correctly.