What is a One-Time Secret?
Since One-Time Secret's launch in 2012, many similar apps and services have sprung up using the company's open-source code. Created by developer Delano, One-Time Secret is a link that can be viewed only one time, typically used to share sensitive information like passwords and private links via email or chat.
One of the biggest challenges (for companies and individuals) is sharing passwords securely. Many people use email, spreadsheets, or messaging apps to share passwords. The problem with these methods is that they're easily copied or shared—you have no control over who has access to your credentials!
One-Time Secret is an answer to this password-sharing challenge. But does One-Time Secret actually solve the issue? Or, is it a good alternative for a password manager?
We'll explore One-Time Secret in this article and look at the best way to share passwords using a secure password manager.
Table of Contents
What is a One-Time Secret and How Does it Work?
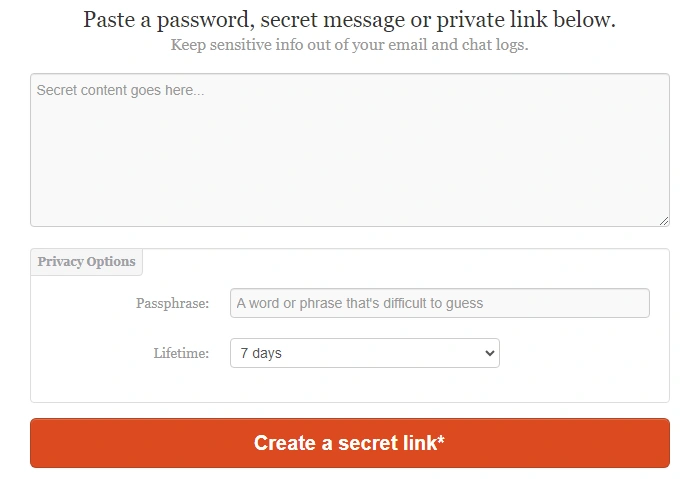
One-Time Secret is a tool to share passwords and sensitive notes. Instead of sending a password over email, text, or a messaging app, you use One-Time Secret and send a link and a password to open the message instead.
One-time Secret prompts you to enter a password, secret message, or private link, and create a secret link.
When the recipient visits the link address, they have to enter the password, and the information you shared appears on-screen for them to read. The link will only work one time before it disappears forever.
You can also set a time limit for the One-Time Secret to "self-destruct," even if the recipient doesn't read it. Times range from five minutes to several days.
Here is an example:
- Someone in accounts needs to share the company's bank account credentials. They don't want to send them over text or email.
- So, they create a One-Time Secret message with the bank account's credentials and a one-time password to open the message. Because this is highly sensitive information, the sender also sets the One-Time Secret to self-destruct in 1 hour.
- They send the One-Time Secret link to the recipient's company email address. They may share the one-time password over the phone or another medium to prevent someone from intercepting the One-Time Secret message.
- The recipient opens the link, enters the password, and the bank account credentials appear on the screen.
- The recipient copies the bank account credentials somewhere safe and closes the browser, simultaneously deleting the One-Time Secret message.
- If the recipient (or anyone else) clicks the link again, an error message appears saying: "Unknown secret. It either never existed or has already been viewed."
If the sender changes their mind, they can "burn the secret," but only before the recipient views it.
Where Do You Manage One-Time Secrets?
https://onetimesecret.com/ is the original One-Time Secret application. But, since the code is open-source, several similar websites are offering the same service.
Most One-Time Secret apps are free, while others limit the number of free One-Time Secrets before moving to a paid plan.
One-Time Secret apps feature a basic text field for entering your data, but some offer a WYSIWYG editor to create tables, lists, insert documents, and more.
What Kind of Information Do You Share in a One-Time Secret?
People use One-Time Secrets to send all sorts of data. Here is a list of common information sent via One-Time Secret:
- Sharing passwords
- Credit card details
- API keys
- Sensitive code or algorithms
- Sharing sensitive, untraceable notes
Some One-Time Secret apps allow you to share documents and images. The problem with these documents is that they're traceable through stored metadata, defeating the purpose of an anonymous One-Time Secret!
OneTimeSecret.com Alternative
If you need to share credentials with teammates, co-workers, and employees, consider a password manager like TeamPassword. Give access to credentials on a need-to-know basis; and since the user always has access to what they need in a secured vault, there's no motivation for them to write down, email, or text passwords and other secrets.
Rather than manually sending a secret each time, you can divide credentials into different groups and give permissions accordingly.
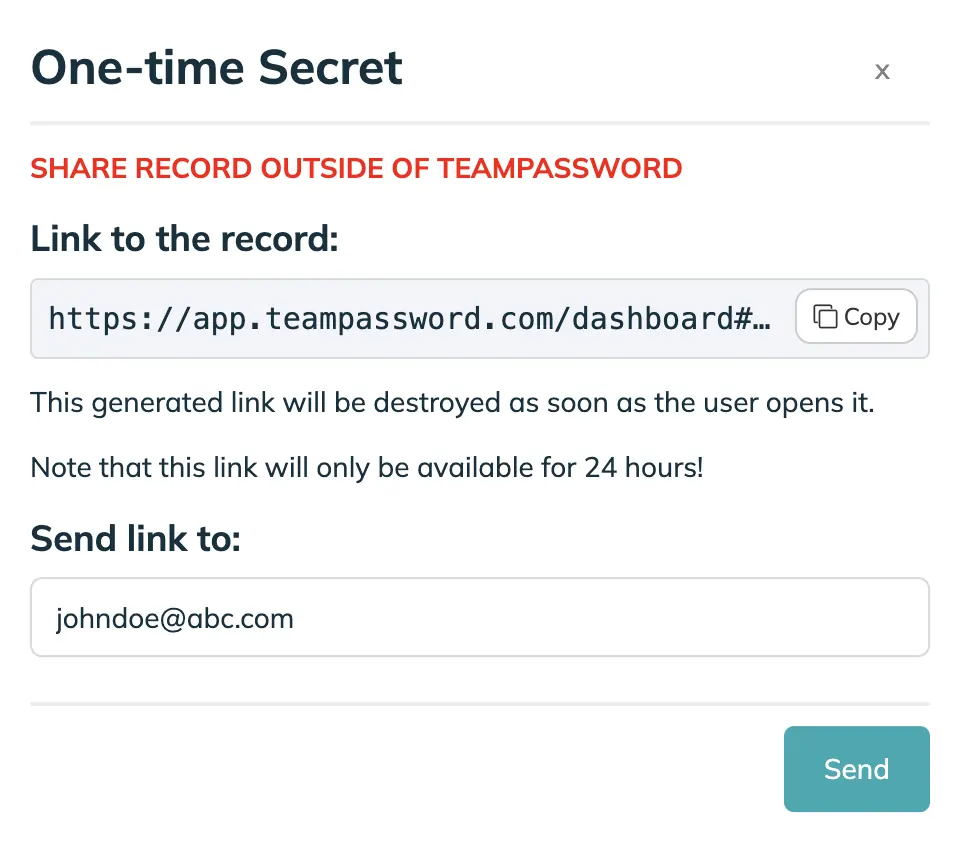
For the times you need to send a password to someone outside your organization, TeamPassword's Enterprise plan offers it's own One-Time Secret Feature!
It allows you to share a password from within your encrypted vault to an authorized person.
The link is destroyed when the user opens it, allowing them to use the password just once.
Is One-Time Secret Secure?
One-time secrets provide some security by limiting access to a single use, but experts generally advise against them for long-term password sharing.
Here's why:
- Limited Functionality: One-time secrets are designed for temporary access, not ongoing collaboration. They lack features like user roles and permission controls, making it difficult to manage access for multiple team members over time.
- Potential Insecurity: The security of one-time secrets depends entirely on the platform used. Some may offer strong encryption, while others might leave the data vulnerable.
Security experts recommend password managers as a more secure alternative. Password managers offer:
- Encryption: Passwords are stored in an encrypted format, making them unreadable even if someone hacks into the system.
- Secure Storage: Passwords are typically stored on secure servers with robust security measures.
- Access Controls: You can set permissions for different users or groups, allowing granular control over who can access what.
- Additional Features: Many password managers offer additional features like password generation, secure password sharing, and two-factor authentication, further enhancing security.
For these reasons, security experts generally recommend password managers over one-time secrets for managing shared passwords.
How is a Password Manager Different from One-Time Secret?
One-Time Secret is a messaging service, not a password manager. It doesn't allow you to store or recall passwords, whereas a password manager does.
TeamPassword offers complete control over who accesses your passwords and lets you track their usage. With One-Time Secret, you lose track of credentials after sharing, not knowing where they go or who uses them.
One-Time Secret doesn't address weak passwords or credential reuse. In contrast, TeamPassword includes a secure password generator (which you can use for free), enabling you to create unique, strong passwords for each account.
Common Password Vulnerabilities for Companies
Even with the increase in cyberattacks, the multitude of password tools, and endless media warnings, many companies still allow poor password management practices.
We always encourage companies to try TeamPassword's 14-day free trial to experience how you can share credentials securely.
Mistake 1 - Weak Passwords
Weak passwords are a significant issue. P@$$w0rd123 might look complex, but it's no different from using password123. Hackers often run these obvious passwords first during brute-force attacks—where criminals try to guess your password.
Many people believe that just replacing letters with symbols is enough to create a strong password. While this does offer some security, it's still easy to guess!
Agencies that manage multiple client accounts should also avoid using the client's name in a password. For example, clientnameIn$t@gr@m for a client's Instagram account might look secure with symbols, but hackers know to expect these changes.
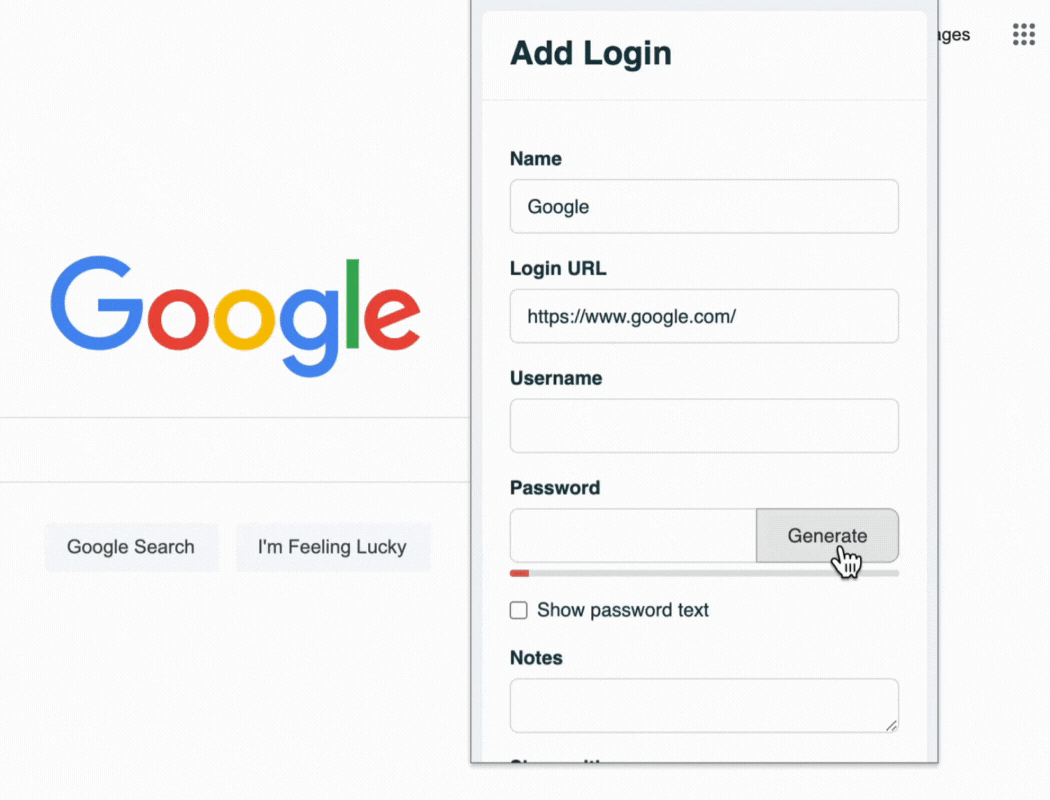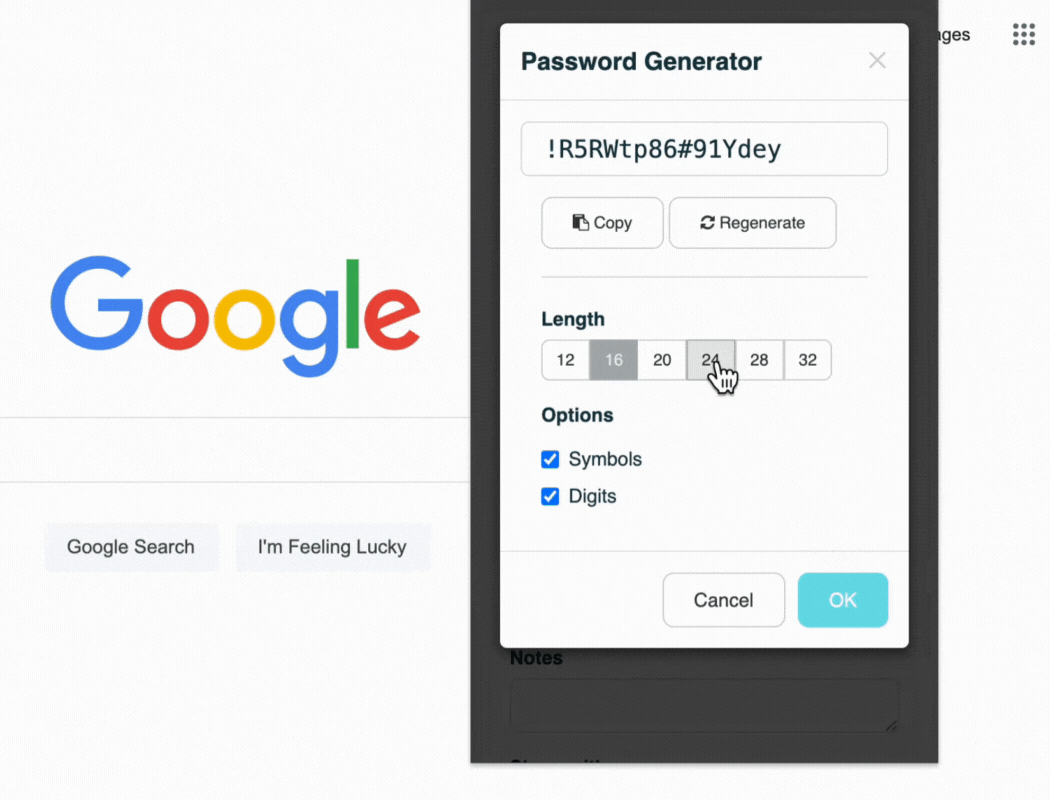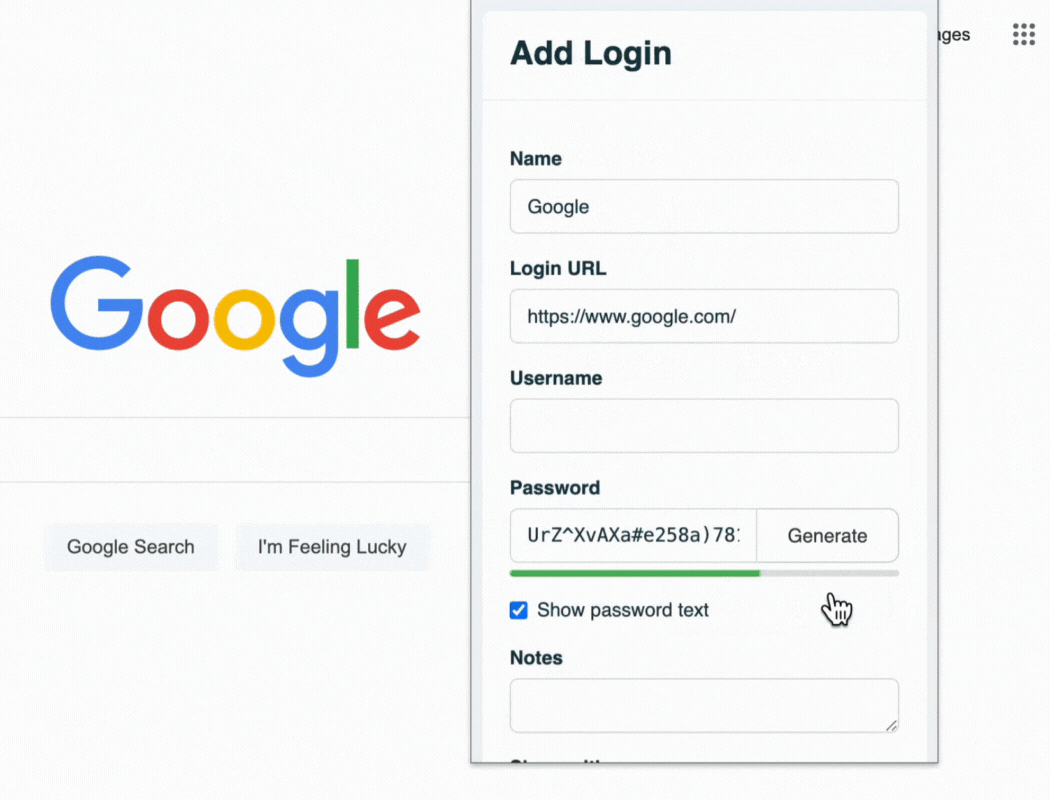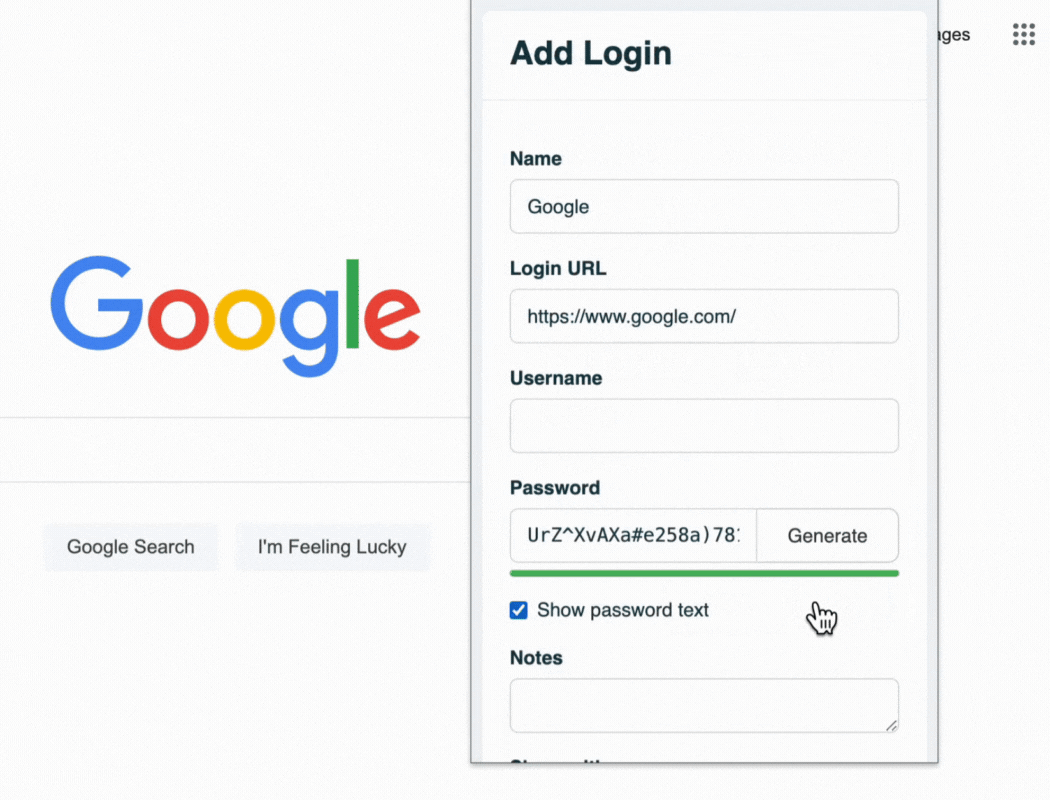
Companies should create robust (12 character minimum) passwords using a random set of characters (including uppercase, lowercase, numbers, and symbols).
TeamPassword features a built-in password generator, so you never have to worry about weak passwords again!
Mistake 2 - Storing Passwords in Plaintext
Storing passwords in plaintext (and yes, this includes storing passwords in your browser and sending credentials over One-Time Secret) means anyone can view, use, or share your company's credentials.
Agencies often manage hundreds of accounts for clients—using spreadsheets to store and share credentials. Anyone can copy a spreadsheet and share it without your knowledge.
Plaintext password storage is extremely negligent, and in some states or countries, could violate regulations, leading to prosecution or fines.
Mistake 3 - Reusing Passwords
Like weak passwords, reusing credentials creates another significant cybersecurity vulnerability.
Attackers often use passwords stolen from one data breach to try accessing other accounts and applications in a process called credential stuffing.
If your company reuses the same password for multiple accounts, attackers only have to steal one set of credentials, and they have access to all the other accounts!
TeamPassword's built-in password manager ensures your team creates unique passwords for every account! You can choose between 12-32 characters using uppercase, lowercase, symbols, and numbers.
Mistake 4 - Using the "Remember Me" Feature
Many websites and applications have a "Remember me" feature with a checkbox. Sometimes there's a period "Keep me logged in for 14 days."
The problem with this remember me feature is that if someone steals an employee's device, the criminal can use their browser history to find your company's accounts and log in.
The same issue applies to saving passwords in the browser. If someone steals an employee's browser credentials, they have access to all the saved passwords too!
With TeamPassword, all of your credentials are encrypted and stored securely. Employees use a browser extension (Safari, Chrome, Firefox) to sign in, so your passwords never leave TeamPassword. Two-factor authentication (2FA) creates a second authentication step, preventing a full breach, even if someone steals an employee's TeamPassword credentials.
Mistake 5 - Changing Passwords
Companies often try to change passwords frequently as a security measure. The problem is that employees often end up reusing passwords over time or swap passwords across accounts.
If you're not using a password manager, it can be challenging to keep track of changes, with employees constantly sharing credentials—exposing many cybersecurity vulnerabilities!
With TeamPassword, you can update passwords regularly and not even have to tell employees. The password manager updates the credentials for all users, so work continues as usual.
Stop the Password Sharing Struggle: Streamline Teamwork with TeamPassword
Tired of the never-ending cycle of password resets, confusing spreadsheets, and risky email exchanges? TeamPassword is your key to secure, stress-free collaboration.
Built for Teams, Built for Security:
- Share Smart, Not Scary: Grant access to specific accounts for different teams, ensuring everyone has what they need without compromising security.
- Goodbye Paper Trail Chaos: Forget sticky notes and insecure emails. TeamPassword keeps passwords safe and centrally managed.
- Always in the Loop: Monitor important activity with email alerts and detailed logs, keeping you on top of everything.
One Password List, Everywhere You Work:
- Effortless Access: TeamPassword works seamlessly across all your devices with browser extensions and mobile apps.
- Say Goodbye to Duplicates: No more managing multiple password lists. One secure vault for all your team's needs.
Don't Take Our Word for It:
Experience the TeamPassword difference risk-free with a 14-day free trial. See how secure and easy collaboration can be.
Enhance your password security
The best software to generate and have your passwords managed correctly.