Passkey vs. WebAuthn: What's the Difference?
You've probably heard the term 'WebAuthn' used in conjunction with passkeys. And while you've probably set up a passkey here and there and enjoyed the convenience of using your fingerprint to sign in to an application, you may be wondering how WebAuthn and passkeys are connected.
We'll clear up the difference between passkeys and WebAuthn in this article.
Here is the key difference between Passkeys and WebAuthn:
- Passkey is a credential - it is one method for passwordless login
- WebAuthn is a specification that helps developers implement passkeys on web applications
Put another way, Passkeys and WebAuthn are distinct but interconnected. Passkeys are essentially digital keys that replace traditional passwords, allowing you to log in using biometrics or a device lock. WebAuthn, on the other hand, is the technical standard that makes passkeys possible. It provides the framework for websites and apps to securely verify your identity using passkeys. Think of WebAuthn as the blueprint for building a house, while passkeys are the actual keys that unlock the door.
Table of Contents
What Is a Passkey?
A passkey is a type of authentication method that allows users to access online services without using passwords. Passkeys use asymmetric public key cryptography.
'Passkey' is a marketing term popularized by vendors like Google and Apple, and refers to Multi-Device FIDO Credentials implemented with the WebAuthn specification. After reading that mouthful, it's understandable that everyone calls them passkeys!
More specifically, Passkey refers to a credential that uses public-private key cryptography and, rather than locking the private key to a single device, syncs it across devices. When passkeys were first rolled out, vendors would only sync within their ecosystem. If you created a passkey on an Apple device, it would only automatically sync to other Apple devices. If you needed to access that account on an Android device, you had to create a separate passkey. We've written about this process thoroughly in our article on passkey technology.
In the second half of 2023, third-party password managers started supporting passkey syncing. This is great news for the consumer - your passkeys don't have to be vendor or browser locked (e.g. Google Password Manager with Chromium-based browsers, and iCloud Keychain with Safari).
How Does a Passkey Work?
The public key is registered with the online service, while the private key never leaves the device (unless it is synced to other devices, as is commonly the case now). When the user wants to log in, the online service sends a challenge to the device, which uses the private key to sign it and send it back. The online service verifies the signature using the public key and grants access to the user.
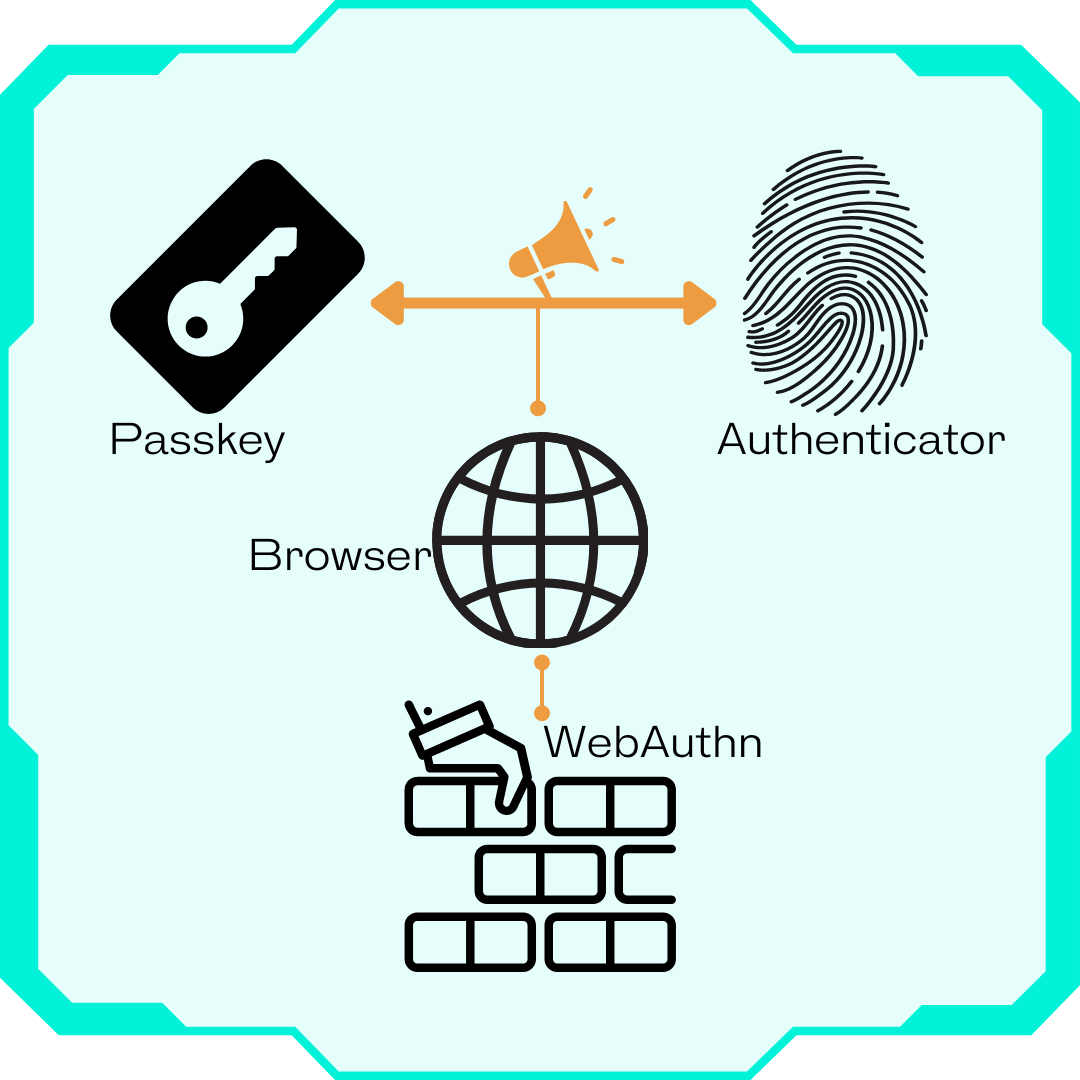
There are several protocols running in the background to help make this possible: CTAP (client to authenticator protocol) which helps your browser talk to the authenticator, and WebAuthn which tells the browser how to talk to the web application for authentication.
Benefits of Passkeys
- Enhanced Security: Passkeys offer a higher level of security than traditional passwords, as they rely on unique and immutable biometric data that is difficult to forge or steal.
- Convenience: Passkeys use an auhentication mechanism that the user already uses every day - the biometrics or PIN that unlocks their device. No more resetting passwords.
- Protection Against Phishing Attacks: Passkeys are not susceptible to phishing attacks, as the private key is never seen by the user, unlike text-based passwords.
- Reduced Credential Fatigue: Passkeys eliminate the temptation to reuse passwords across accounts - a bad habit that's all too easy when juggling hundreds of passwords.
- Multi-Factor Authentication (MFA) Enhancement: Passkeys can be integrated into multi-factor authentication strategies, further fortifying account security.
What Is WebAuthn?
WebAuthn is a web standard that defines an API for accessing public key credentials by web applications. It's goal is secure user authentication without passwords. The specification was published by the World Wide Web Consortium (W3C) and the FIDO Alliance, and is a core component of the FIDO2 Project.
How Does WebAuthn Work?
WebAuthn works by allowing web applications to communicate with authenticators, which are devices or software that can generate and store cryptographic keys and perform operations with them. Authenticators can be built-in to the platform (such as a Trusted Platform Module or a biometric sensor), or external (such as a USB security key or a smartphone). Web applications can request the creation of new credentials, or the assertion of existing ones, by calling the WebAuthn API methods in the browser. The browser then mediates the interaction with the authenticator, and returns the result to the web application.
In simpler terms, WebAuthn enables web applications to verify your identity using something you have (your device with its unique private key) in conjunction with the biometric data or PIN you use to unlock your device, instead of requiring you to create and remember/store a unique password for every website you use.
This way, you can have stronger and more convenient security for your online accounts, without having to rely on passwords that can be forgotten, stolen, or compromised.
Benefits of WebAuthn
Some of the benefits of WebAuthn are:
- Resistant to phishing, man-in-the-middle, and replay attacks, since the authenticator only responds to legitimate requests from the origin that created the credential, and signs a challenge that is unique for each authentication session.
- Privacy-preserving, since the authenticator does not reveal any personal or identifiable information to the web application, and does not link credentials across different origins.
- Interoperable, since it is based on widely supported web standards and cryptographic algorithms, and allows for various types of authenticators and user verification methods.
- User-friendly, since it reduces the need for passwords and offers a consistent and simple user experience across different platforms and devices.
Some of the criticisms of WebAuthn are:
- It is not widely adopted yet, since it requires support from both web applications and browsers, and not all users have access to compatible authenticators.
- It is not backward compatible with legacy systems that rely on passwords, which may limit its usability and acceptance by some users and organizations.
- It is not foolproof, since it still depends on the security and integrity of the authenticator, the browser, the platform, and the user. For example, authenticators can be lost, stolen, or damaged; browsers can be compromised by malware or vulnerabilities; and platforms can be infected by rootkits or keyloggers.
Passkey vs. WebAuthn: Key Similarities and Differences
Passkeys and WebAuthn aren’t competing technologies—they’re two parts of a system working together to enable a seamless, passwordless login experience. Think of WebAuthn as the underlying framework and passkeys as the digital credentials that users rely on.
How Passkeys and WebAuthn Work Together
- Passkeys: These are digital credentials that replace traditional passwords. They typically use public-private key pairs to authenticate users securely. A passkey is stored on your device and used to prove your identity during login.
- WebAuthn: Short for Web Authentication API, WebAuthn is a standard that enables communication between your browser, device, and the website or app (known as the relying party). It ensures that passkey-based authentication works smoothly across different platforms and devices.
Key Similarity:
Both Passkeys and WebAuthn are essential for a passwordless login process. Together, they eliminate the need for traditional passwords, providing a faster and more secure way to log in.
Key Difference:
- Passkeys: The user-facing element—a secure, digital credential stored on your device (like your phone, laptop, or a hardware authenticator).
- WebAuthn: The technical specification that makes passkey authentication possible by guiding the browser and website on how to communicate during the login process.
How the Process Works:
-
WebAuthn Facilitates Communication:
WebAuthn acts as the bridge between the browser and the website. It defines how the two interact to handle authentication requests. -
CTAP Bridges the Gap to the Authenticator:
Your browser uses the Client to Authenticator Protocol (CTAP) to communicate with your authenticator, which can be your smartphone, laptop, or a hardware security key like YubiKey. This step ensures the device holding the passkey is ready to authenticate you. -
Authentication with the Relying Party:
After the authenticator validates your identity using the passkey, WebAuthn takes over again. It instructs the browser on how to securely send the authentication data to the relying party (the website or app where you’re logging in).
Are Passwords On Their Way Out?
Passwords are a hassle, and often a weak point in online security. There's no denying that. However, they are still essential for many websites and applications that do not support passwordless authentication methods. Until these technologies become more widely available and compatible, passwords remain a critical layer of protection for our personal and professional data. It's important to improve our password hygiene and use strong, unique, and hard-to-guess passwords for each account.
The easiest and most secure way to do this is to use a password manager, which can generate and store complex passwords for us, and autofill them when we need to log in. This way, we can avoid using the same password for multiple accounts, or writing them down on paper or digital notes. Password managers can also alert us if our passwords have been compromised or leaked, and help us change them quickly. By using a password manager, we can enhance our online security and prepare for the transition to passwordless authentication in the future.
Keep Your Passwords Safe & Secure With TeamPassword
Passkeys are being rolled out with a focus on individual users and individual accounts.
Many businesses need to share account access with multiple users, granting and removing access as needed. Until passkeys can handle this use-case securely and with ease, and until enterprise applications support them, passwords are a fact of life for business.
TeamPassword was designed for businesses that share passwords. It's the easiest password manager to use and provides industry-standard AES 256-bit vault encryption (see the TeamPassword security page) and enforceable two-factor authentication.
TeamPassword features:
- Centralized Password Management: Securely store and manage all team passwords in one place.
- Ironclad Security: Protect your passwords with cutting-edge encryption and robust security protocols.
- Flexible Access Control: Determine who can see and use specific passwords with granular permissions.
- Effortless Collaboration: Improve efficiency by eliminating the need for insecure password sharing.
- Comprehensive Auditing: Track password activity with detailed logs for accountability and threat detection.
Try TeamPassword for free with your business!
Enhance your password security
The best software to generate and have your passwords managed correctly.