Passkey vs. Password: Which Is Right for You?
We all know the password drill. That flicker of panic when you can't remember the right combination of letters, numbers, and that one special character. You click "Forgot Password," annoyed you have to invent another new secret, knowing you'll probably forget this one, too.
For decades, passwords have been the frustrating, flawed key to our digital lives. But what if we could get rid of them completely? A new technology called "passkeys" is starting to appear on our phones and laptops, promising just that. But is it just a buzzword, or is it genuinely better? We're pitting passkeys vs. passwords to find out. We'll explore how they differ, which is truly more secure, and what the adoption of passkeys actually means for you.
Table of Contents
What Is a Passkey?
In technical terms, a passkey is a unique cryptographic key that is generated and used for authentication purposes. It is based on public-key cryptography, which involves a pair of keys: a public key and a private key.
When a user creates a passkey, the system generates a public-private key pair. The public key is shared with the service provider or server, while the private key is securely stored on the user's device. The passkey is usually protected by a user-generated PIN or biometric authentication.
When the user wants to authenticate themselves, the server sends a challenge to the user's device. The device then uses the private key to sign the challenge, creating a digital signature. The server verifies the signature using the user's public key, and if the signature is valid, the user is granted access.
What does a passkey mean for you?
- Because passkeys cannot be shared like passwords and only exist on your device, a bad actor can't trick you into sharing them.
- You don't have to remember passwords for accounts that support passkeys. Instead, you use a local PIN or the same biometric authentication method you use to unlock you device (like fingerprint or face).
Passkeys validate you when you prove that you own the authorized device, rather than when you know the correct password. The PIN or biometric authentication is your private key - it's not shared to a server.
In summary: passkeys are faster and safer. The internet is moving toward passkeys, but it will be years before they're universally supported.
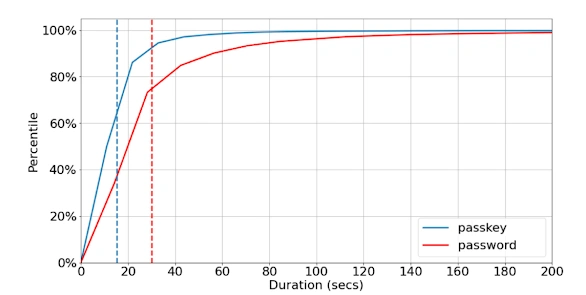
Time spent authenticating with passkey vs password (data from March-April 2023). Dashed, vertical lines indicate average duration for each authentication method (n≈100M)
Source: Google Blog
How Does a Passkey Work?
Passkeys offer a more secure alternative to passwords by utilizing asymmetric encryption, a cryptographic technique that employs a pair of mathematically linked keys: a public key and a private key.
Here's a simple breakdown of how it works and its advantages:
The Key Pair:
-
Private Key: This key is the crown jewel, kept securely on the user's device (phone, computer, etc.) It's like a super-secret recipe only the user possesses. Passwords managers or secure enclaves within the device can be used for secure storage and access control (often requiring biometrics or a PIN).
-
Public Key: This key, as the name suggests, can be shared with the service provider (website, app) during registration. Think of it as a publicly available lock. While anyone can see it, only the private key (the recipe) can unlock it.
The Authentication Dance:
-
Challenge Issued: During login, the service provider generates a random challenge, a piece of data unique to that login attempt.
-
Challenge Encryption: The service provider encrypts the challenge using the user's public key (the publicly available lock). This encryption ensures only the corresponding private key can decrypt it.
-
Private Key Decryption: The challenge is sent to the user's device. There, the private key decrypts the challenge, proving the user possesses the key that matches the public key shared with the service provider.
-
Verification and Access: The decrypted challenge is sent back to the service provider. If the decrypted challenge matches the original challenge, it confirms the user holds the private key and grants access.
For a more in-depth explanation of how passkeys work, read the linked section of the article How do passkeys work?
Benefits of Passkeys:
Passkeys offer enhanced security by eliminating vulnerabilities associated with traditional passwords. They are immune to common threats like phishing and password reuse, ensuring that there are no "weak" or "reused" passkeys to exploit. Even if a cybercriminal breaches a website and accesses your public key, it’s useless without the corresponding private key, which is securely stored on your device.
In addition to being secure, passkeys are incredibly convenient and user-friendly. They eliminate the need to remember complex passwords, offering a seamless authentication experience that reduces frustration and increases efficiency.
Another advantage is their reduced reliance on servers. Since passkeys aren’t stored on centralized databases, they are less vulnerable to large-scale data breaches, giving users peace of mind about the safety of their information.
Drawbacks of Passkeys
While passkeys have many advantages, they aren’t without drawbacks. One limitation is the reliance on specific devices. Since private keys are stored on your device, losing access to that device can lock you out of your accounts unless you have a secure backup or recovery method in place.
Compatibility can also be an issue, as not all platforms or services currently support passkeys. Users may find themselves juggling multiple authentication methods, reducing the overall convenience.
Finally, transitioning to passkeys requires an upfront investment of time and resources, particularly for organizations. Training users and implementing the necessary infrastructure can pose challenges, especially for businesses with limited IT expertise or budgets.
By weighing these benefits and drawbacks, users can decide if passkeys are the right solution for their security and usability needs.
What Is a Password?
A password is a string of characters used to authenticate a user's identity. It is a secret piece of information known only to the user and the service provider. Passwords have been widely used as a security measure for online accounts, applications, and various digital services.
How Does a Password Work?
A Non-Technical Explanation: The Secure Shredder
Imagine you have a secret password, like "BlueOcean123". When you give this to a website, the website doesn't just write it down in a book. That would be very dangerous—if a thief stole the book, they'd have everyone's secrets.
Instead, the website immediately runs your password through a mathematical "shredder." This shredder turns "BlueOcean123" into a totally unique, scrambled line of code, like "a9f4...b2c1". This code is called a hash. The only thing the website stores is this final pile of "shredded paper," not your original password.
This shredder is a one-way street. You can't take the shredded confetti and tape it back together to figure out the original password. It's mathematically impossible.
When you come back to log in, you type "BlueOcean123" again. The website doesn't look at its stored hash. Instead, it takes your new entry, runs it through the exact same shredder, and gets a new pile of confetti. It then compares the new pile to the one it has on file. If the two piles are identical, the website knows you must have used the correct original password and lets you in.
To make this even safer, most websites add a "salt"—which is like adding a pinch of unique glitter to your password *before* shredding it. This ensures that even if two people have the same password (like "Password123"), their shredded confetti will look completely different, making it even harder for hackers.
A Technical Explanation: Hashing and Salting
Passwords are (or should be) never stored in plaintext. Instead, they are secured using cryptographic techniques. The goal is to verify a user's identity without ever storing their secret, making a data breach less catastrophic.
The Hashing and Salting Process
- Hashing Algorithms: When a user creates a password, the system doesn't store the password. It passes the password through a hashing algorithm (like
bcrypt,scrypt, orSHA-256). This algorithm is a complex mathematical function that converts the input (the password) into a fixed-length string of characters called a hash. - One-Way Function: A key property of a cryptographic hash function is that it is a one-way function. It is computationally easy to generate the hash from the password, but it is computationally infeasible (practically impossible) to reverse the process—to derive the original password from its hash.
- Salting: To protect against attacks like "rainbow tables" (pre-computed lists of hashes for common passwords), a unique, random string called a salt is generated for each user. This salt is added to the user's password *before* it is hashed. The salt itself is then stored in the database alongside the final hash.
- Verification: When the user attempts to log in, the system retrieves their unique salt from the database. It combines this salt with the password the user just entered and runs the combined string through the same hashing algorithm. The resulting hash is then compared to the hash stored in the database. If the two hashes match, the user is authenticated. If they don't, access is denied.
Because of this process, even if an attacker steals the entire database, they don't get the actual passwords. They only get a list of hashes and salts, which are non-reversible and, thanks to salting, are unique to each user, making them very difficult to crack in bulk.
Benefits of Passwords:
- Familiarity and compatibility: Passwords have been the de facto method of authentication for decades, making them widely supported across various systems and platforms.
- Ease of implementation: Implementing password-based authentication is relatively straightforward for service providers and doesn't require specialized infrastructure.
- Accessibility: Passwords can be easily shared or communicated, enabling account access for multiple users or in emergency situations.
- Incremental security measures: Additional security measures like two-factor authentication (2FA) can be easily integrated with passwords for added protection.
Passkey vs. Password: Key Similarities
Here are the key similarities between passkeys and passwords:
- Both serve as methods of authentication and identity verification.
- They protect access to digital assets, online accounts, and services.
- Both can be combined with other security measures, such as multi-factor authentication, for enhanced security.
- Both passkeys and passwords require proper management and consideration of security best practices. With passwords, users must keep them private. With passkeys, users must not let their device fall into the wrong hands.
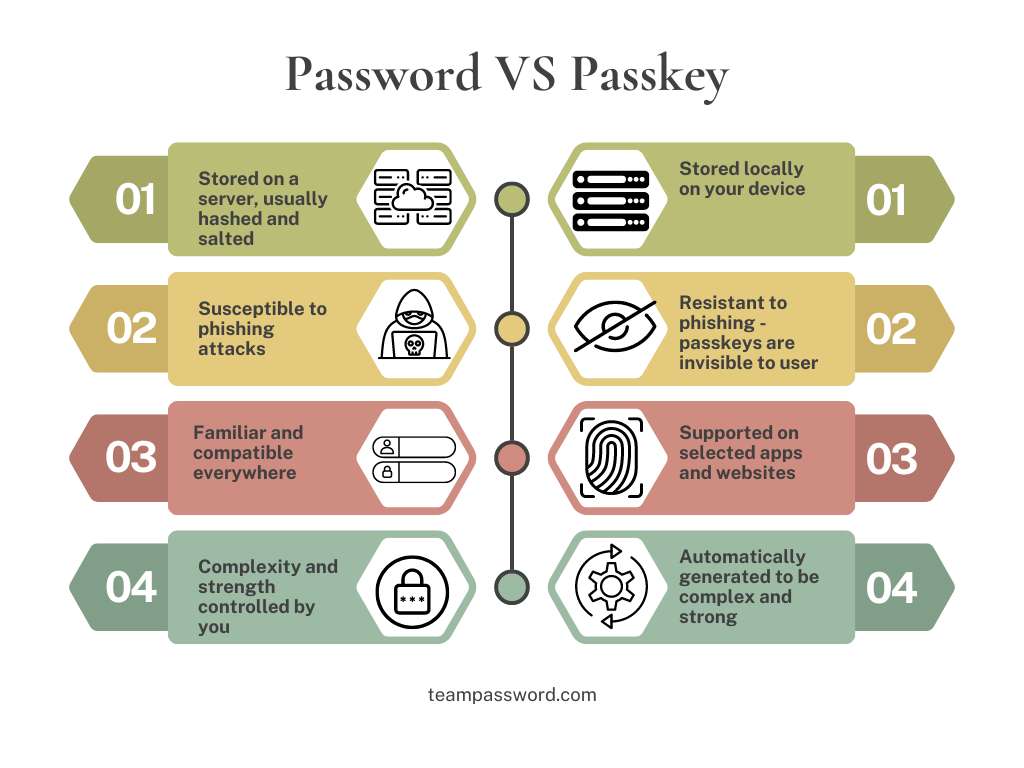
Passkey vs. Password: Key Differences
Here are the key differences between passkeys and passwords:
- Passkeys are generated using cryptographic techniques, while passwords are user-generated.
- Passkeys are typically not transmitted or stored on servers, whereas passwords are usually stored on servers in some form - albeit in a hashed and salted form.
- Passkeys are more resistant to phishing attacks, while passwords are vulnerable to phishing and other social engineering techniques.
- Passkeys are not as widely supported as passwords across all platforms and services.
- The complexity and security of passkeys are typically higher than those of passwords.
Current Passkey Challenges and Limitations
While passkeys offer strong security and are easy to use, they face several real-world challenges. Here are the main limitations slowing their adoption.
1. Fragmented Platform Support
One of the biggest barriers is limited support. Although major companies like Apple, Google, and Microsoft are pushing for passkeys, many websites and apps have not yet adopted the technology. This fragmented rollout creates an inconsistent experience for users, forcing them to juggle new passkeys with old passwords. Until support is universal, users will have to manage multiple login systems.
2. Device Dependency and Lock-Out Risk
Passkeys are tied directly to your physical device (like your phone or laptop), where the secure keys are stored. While this is excellent for security, it also creates a new problem: what happens if you lose your device? If a device is lost, stolen, or broken, you could be locked out of your accounts. Transferring passkeys to a new device can also be a hassle, as not all platforms have a seamless process.
3. Complex Recovery and Backup
Recovering a lost passkey is more complicated than resetting a password. With passwords, you can just click a "Forgot Password" link and get a reset email. Passkeys require a more robust recovery plan, such as syncing them across devices with a trusted cloud service. If a user fails to set up a backup, losing their device could mean being permanently locked out of critical accounts.
4. Difficulty with Shared Accounts
Passkeys are designed for individuals, which makes sharing accounts difficult. Families sharing a streaming service or teams sharing a work tool will find passkeys impractical. While sharing passwords (even if insecure) is simple, passkey technology isn't built for it. Solutions are being explored, but they raise new security concerns—for example, you probably don't want your personal fingerprint linked to a shared family account.
Passkey vs. Password: Which Is Best for You?
Passkeys are the inevitable future of authentication. We recommend adopting them where possible, but for now, the possibilities are limited.
Passkeys are undoubtedly more secure than passwords due to their resistance to common attack vectors. However, given the current limitations and challenges surrounding passkey adoption, passwords still play a crucial role in digital security. Implement strong password management practices, such as using unique passwords, enabling two-factor authentication, and regularly updating passwords.
While we wait for passkeys to become more mainstream, teams can boost their security by utilizing password management solutions like TeamPassword. TeamPassword offers features like secure password sharing, centralized management, and strong encryption, enabling teams to maintain robust security practices.
In the ongoing battle between passkeys and passwords, there is no definitive winner. Passkeys offer increased security but are limited in adoption and sharing capabilities, while passwords continue to be widely supported but have their vulnerabilities. As technology evolves, passkeys will become more prevalent, but until then, it's crucial to manage passwords effectively and leverage tools like TeamPassword to ensure optimal security for your team's digital assets.
Get a 14-day Free Trial of TeamPassword now!
Frequently Asked Questions (FAQ)
Q: What is the main difference between a passkey and a password?
A password is a secret you must remember (like BlueOcean123). A passkey is a secure digital key that your device (like your phone or computer) stores. You don't have to remember it. You just use your device's PIN, fingerprint, or face scan to prove it's you, and the device handles the login.
Q: Are passkeys more secure than passwords?
Yes, passkeys are significantly more secure. Passwords can be stolen, guessed, or "phished" from you. A passkey's most important part (the private key) never leaves your device, so it cannot be stolen in a data breach or phished by a fake website.
Q: What happens if I lose my phone or device with my passkeys?
This is a primary drawback of passkeys. Since the passkey is tied to your device, losing it could lock you out. To prevent this, major providers like Apple and Google offer recovery options, such as syncing your passkeys to a secure cloud account. You must set up a recovery or backup method to avoid being permanently locked out.
Q: Can I share a passkey for a shared account?
Not easily. Passkeys are designed to be personal and tied to an individual's device. This makes them impractical for sharing accounts, like a family streaming service or a work tool. While companies are exploring solutions, this remains a key challenge.
Q: Do all websites use passkeys now?
No, and this is one of their biggest limitations. While major companies are adopting them, most websites and apps do not support passkeys yet. This "fragmented support" means you will need to continue using passwords (and a password manager) for the majority of your accounts for the foreseeable future.
Q: How does a password "shredder" (hashing) work?
When you create a password, a secure website doesn't store the password itself. It uses a one-way "shredder" (a hashing algorithm) to turn your password into a long, scrambled code. When you log in, it does the same thing to the password you type and compares the two scrambled codes. If they match, you're in. This way, even if hackers steal the database, they only get the "shredded" codes, not your actual password.
Enhance your password security
The best software to generate and have your passwords managed correctly.