Ultimate Guide to Password Security
Are you ready to take control of your password security? In this comprehensive guide, we'll explain what effective cyber hygiene looks like, how to do it, and why it works.
A passwordless future may materialize, but for the time being the vast majority of services rely on the uncomplicated functionality of username/password. Keep your identity, finances, and digital life safe with password best practices.
Here's a TLDR:
Secure passwords are:
-
Long, Random, and Unique
A password, by definition, should also be secret. The tools and practices in this article are pointless if they do not help you maintain the secrecy or privacy of your long, random, and unique passwords.
Table of Contents
Why is password security important?
Passwords are often the only thing stopping a cybercriminal from stealing your personal information.
Password security is yet more important in businesses; weak passwords can open up avenues for data breaches and compromise valuable corporate information, customer data, and trade secrets.
Using strong, unique passwords for each account and enabling multi-factor authentication significantly reduces the risk of unauthorized access and protects both individuals and organizations from identity theft and financial losses.
What is a Password Manager?
A password manager is an encrypted vault that securely stores your passwords and other credentials, such as addresses and credit card info. It is typically secured with a single master password and multi-factor authentication.
Password managers make your life easier and safer by only requiring you to remember one password, which removes the temptation to reuse passwords across all of your accounts.
How do passwords get hacked?
Threat actors use a variety of attacks to hack passwords. Three of the most common ways are:
- Brute-force attack: Hackers systematically guess passwords by trying different combinations until they find the correct one. This method is effective against weak and easily guessable passwords, such as common words, birthdates, or simple number sequences.
- Phishing: In phishing attacks, hackers create deceptive websites or send fraudulent emails that mimic legitimate platforms, tricking users into entering their passwords. Once users unknowingly disclose their credentials, hackers can gain access to their accounts and use the stolen passwords for unauthorized purposes.
- Malware: Malware often infects computers in conjunction with a phishing attack. For example, a victim is sent a job offer with an attached PDF which, when opened, downloads a keylogger onto their computer that steals the passwords they type.
Step 1: Organize Your Passwords
A good system for managing passwords informs you of what your passwords are, how many accounts with your personal information rely on password protection, and where your passwords live.
What:
-
password123 or #L?UT;+*\zNrwrj(qZ:cZN"a?
How many:
- Do you know which websites hold your name, number, physical address, and other personal info?
Where:
-
Are your passwords scattered somewhere a cybercriminal could steal them? Think email, text message thread, coworker’s sticky note, browser autofill.
It’s never a good situation when an account you forgot even existed gets breached, exposing your personal information to the dark web. However, you can prevent that forgotten password from being the key to more sensitive accounts by following the golden rule: use strong, unique passwords on each account, and never reuse passwords.
Let’s be honest—none of us can remember every account we’ve ever signed up for (I certainly can’t). But moving forward, your goal should be to minimize the damage this blind spot could cause and take steps to become a better steward of your personal data.
Gather your passwords
You’ll have to do some sleuthing to track down your passwords. A common place is your web browser.
Most of us have given in to Chrome’s unrelenting prompt: “Would you like to save this password?” While there are many different browsers, Chrome holds a whopping 65% of the market share.
Here’s how to check your passwords in Chrome:
-
Click your profile icon in the top right of Chrome
-
Click the key symbol for Google Password Manager
If you’ve set Chrome’s password manager to be password protected, you’ll need to enter that now. Otherwise, you’ll see a list of every password that Chrome has saved.
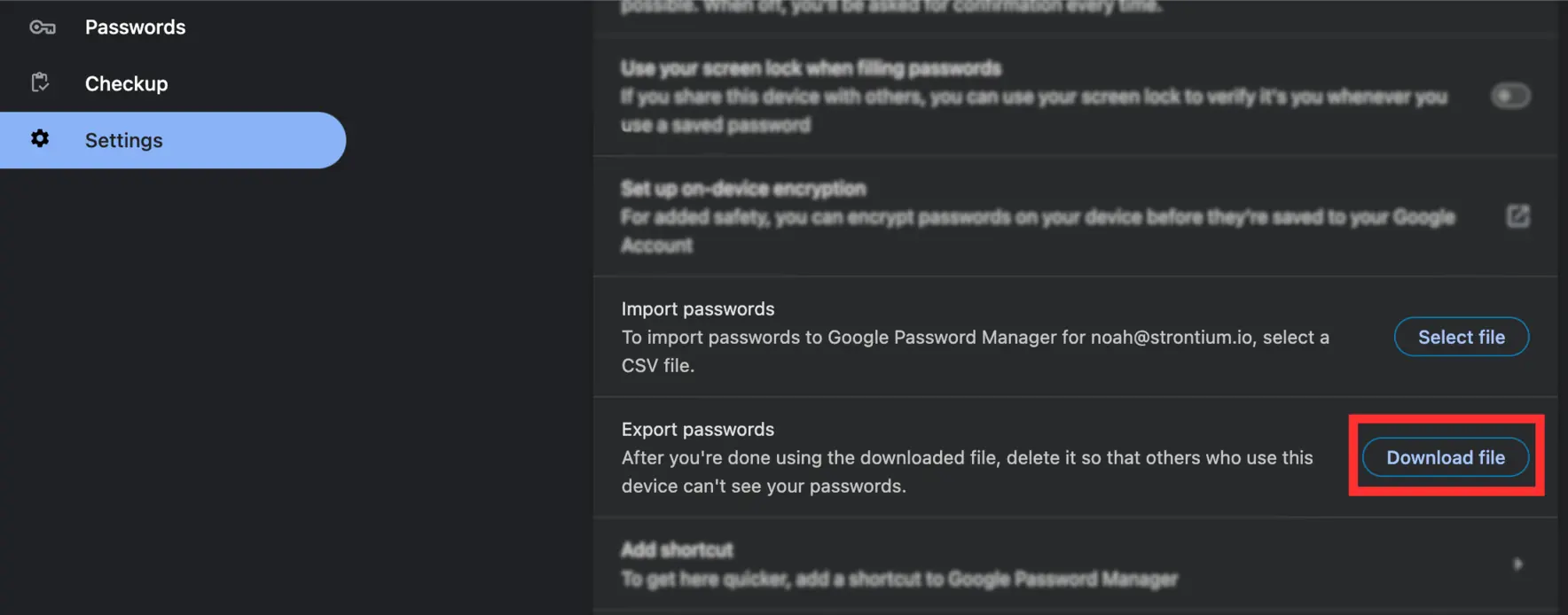
To export a CSV of your passwords, select the Settings tab on the left, and scroll down to Export passwords.
If you see passwords for a forgotten account, now is a good time to deactivate it or update its password. If it gets hacked, personal information found there can be used to piece together your dark web profile and potentially leveraged against you in the future on an account you do care about.
Clear or disable your browser's password manager altogether if you're uncomfortable with the information your browser has saved about you.
Instructions on locating saved passwords for:
Native options (i.e. whatever happens to come with your browser or device) are convenient. But they’re not so much password managers as they are password “savers”. And then there’s the issue of cross-platform compatibility. Your Chrome passwords don’t sync with Safari. Your Apple Keychain doesn’t work with Chrome on Mac, or Android.
Then there’s single sign-on (SSO), which most services now support. The most common is Google SSO, which allows you to use your Gmail address when creating an account with another company. This trades some security and privacy for convenience and isn’t available for every service. Even if you use SSO for every service that supports it, you’ll be left managing some passwords.
Password managers, on the other hand, can handle all your account credentials across every device and browser.
Move passwords to a password manager
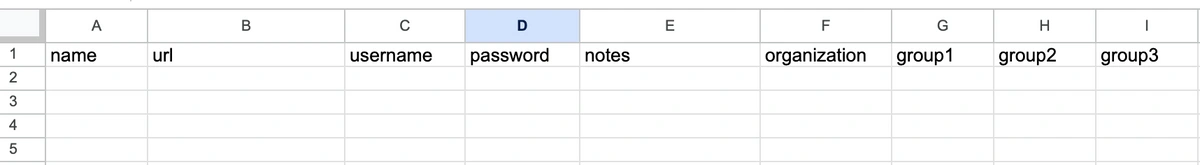
First, get that CSV we downloaded in step 1.a. Password managers can import the browser CSV as-is, but your data will probably be pretty messy. Password managers may also provide a Template, so you can prepare your data for upload in an Excel/Sheets doc. It might look something like this:
Now upload your CSV to your password manager.
I had around 160 passwords the first time I imported them from Chrome into a real password manager. Most of the passwords were identical or slight variations of each other. Additionally, the names of the logins were convoluted URLs that made knowing what accounts I had and searching for those accounts a huge pain.
There are two laborious tasks when setting up your personal passwords:
- Make the records easily searchable; that is, rename and add relevant notes
- Manually update the password for every single account.
#2 is the big one. This may be a 2+ hour project. However, assuming the new passwords you create follow the golden rule - long, random, unique - you shouldn’t need to do it again for a long time.
Old security standards recommended changing your passwords every 90 days. However, security experts have recently changed their recommendations to align with the data - the NIST now states that users should not be required to change their secrets, barring evidence of a breach. Research shows that humans react very predictably to imposed composition requirements.
If you’ve ever had a portal that requires you to update your password every 90 days, you know the drill: Add a !, then switch it to @, then #, etc. You can tell people to change all their passwords every 90 days, but it’s impractical. No one does it.
Experts say that if you’re using a 24+ character computer-generated password, you probably don’t need to change it unless its website was involved in a breach. For high-security applications such as your bank, you may want to stick with that 90-day cadence.
Password generators are integrated into password managers, so achieving that 24+ character random password is easy.
Why would you change your password if it wasn’t involved in a breach? Passwords are often compromised months before they’re used for an attack. They might be sold on the darkweb, or simply sitting in a threat actor’s notepad for months while they plan an attack. Changing it could undo all their hard work.
However, this is impractical for all of your accounts, and if you follow the password practices advised, constant changing shouldn’t be necessary.
Step 2: Create Passwords that Do Their Job
Remember the golden rule? Long, random, unique.
Here’s what you need to do to create strong passwords:
-
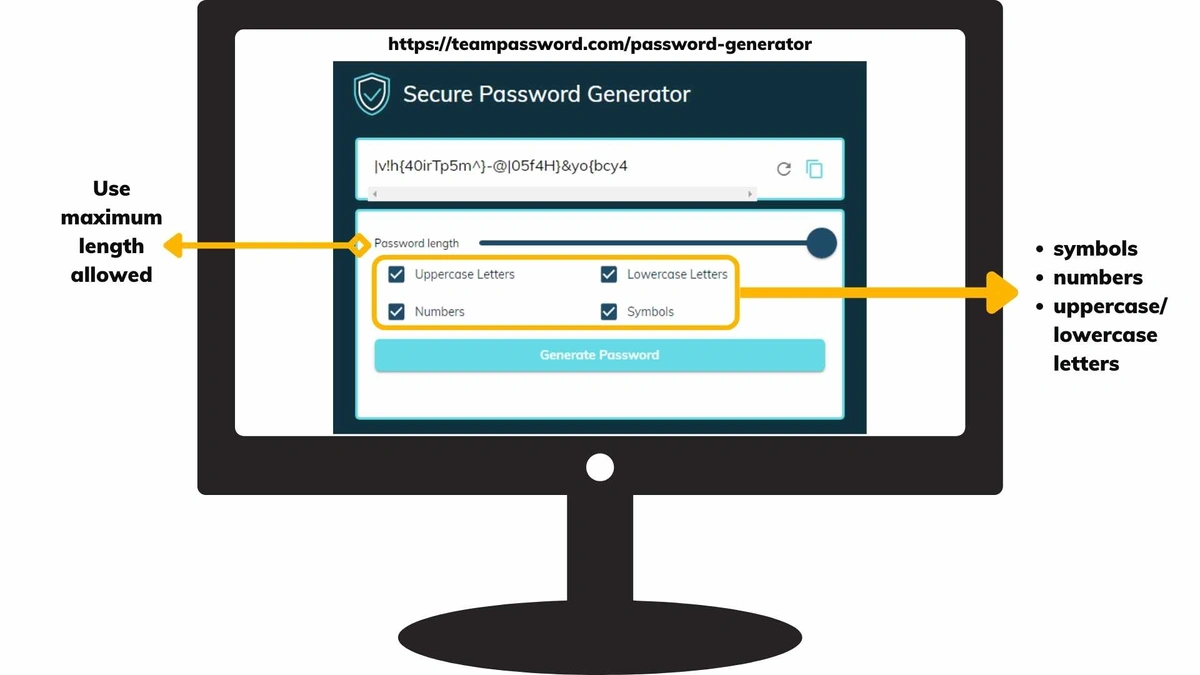
Use a password generator to create a fully random, 16+ character password that includes numbers and symbols.
Go 24+ characters if you can. I’ve run into a couple of online portals with 12 and 15-character limits on account passwords. This is not good. Beyond sending annoyed emails or taking your business elsewhere, there’s not much you can do to protest it. Use the longest password possible, and make sure you’re using upper and lower-case letters, numbers, and symbols.
How to create strong and memorable passwords with Passphrases
If you need to create a strong and memorable password (such as the master password for your password vault), try a passphrase.
A good place to start is combining five words in a humorous way. Example:
- socks-monkey-pescatarian-pithy-orb.
You’d have to remember how to spell “pescatarian”, but you get the idea. You can also use passphrase generators to make sure it’s random.
- Example of a bad passphrase: to-be-or-not-to-be.
A tired Shakespeare reference might make you feel sophisticated, but using famous quotes, song lyrics, or poem stanzas is highly unsophisticated when it comes to keeping yourself safe from cybercriminals.
Passphrases may not work if the website in question has a 15-character limit - I’m looking at you, utility company. This would limit you to three medium-ish length words. A fully random jumble of symbols, letters, and numbers will serve you better in this case.
Read Tips and Tricks to Create a Strong Password for more ideas.
Why are long and random passwords strong?
For a fun, easily understood primer on password security, check out this video:
The history of cryptography fills several tomes, but I’ll try to cover the cliff notes as they relate to password security here.
When you sign into your Amazon account, Amazon does not match the password you entered with a plaintext, character-for-character version of the one you used to create your account. It matches the password you entered to a hashed and salted version of the password you used to create your account.
When you save a new password, a hash function creates a hash version and saves that on the server.
When you log in using your password, the hash function recreates the hash to see if it matches what's stored. If the hashes match, the algorithm passes the authentication and logs you in.
For example:
- Original password: Pa$$w0rd123
- Hashed password: 6AF1CE202340FE71BDB914AD5357E33A6982A63B
While this might seem secure, simple hashed passwords aren't hack-proof.
The hash function only creates a unique hash for each password, not for each user. So, if multiple users have the password, Pa$$w0rd123, the hash will be exactly the same.
This vulnerability is exploited in rainbow table attacks, where cybercriminals use precomputed tables of known hashes.
To overcome this encryption vulnerability, engineers salt passwords so each hash is unique, even if the passwords are identical.
A salt appends a unique value of 8 bytes (16 characters) to the password before the hash function creates a hash. This way, even identical passwords are unique before the hash function.
For example:
- Two identical passwords: Pa$$w0rd123
- Salt value one: E1F53135E559C253
- Salt value two: 84B03D034B409D4E
- Password one before hash: Pa$$w0rd123E1F53135E559C253
- Password two before hash: Pa$$w0rd12384B03D034B409D4E
- Password one hashed value (SHA256): 72AE25495A7981C40622D49F9A52E4F1565C90F048F59027BD9C8C8900D5C3D8
- Password two hashed value (SHA256): B4B6603ABC670967E99C7E7F1389E40CD16E78AD38EB1468EC2AA1E62B8BED3A
Step 3: Multi-factor Authentication (MFA or 2FA)
Two-factor authentication or multi-factor authentication is your second line of defense. If your super-strong password gets leaked and used, the threat-actor will still need a one-time password (OTP) - typically a code - to authenticate sign-in. 2FA exists in a number of forms:
- Hard tokens: fob or USB stick from companies such as Yubikey
- Authenticator apps: Authy, Authenticator (Google, Microsoft, and Apple have their own versions) just to name a few
- Magic Links/Codes: when you sign in, you’ll be prompted to check your email for a one-time link or code
- Push notifications to your device
- SMS code: code texted to your phone number
While SMS is better than no 2FA, it’s recommended to avoid it where possible. The danger of SMS is mostly due to the possibility of SIM-swapping, where a criminal convinces a carrier to transfer a customer’s number to the criminal’s own device, thus gaining control of any OTPs.
With yet another huge T-Mobile breach behind us, it’s best not to put your trust in a phone number whose connection to your device can be severed by an underpaid, undertrained employee.
The 2022 Uber incident involved a contractor, either by accident or to make it stop, accepting a push notification request to authenticate a sign-in attempt. Uber believes their devices had previously been infected by malware that stole their password and leaked it on the dark web.
If you get spammed with requests to authenticate a login attempt, or someone asks you for your code, remain calm and do not give in to the sense of urgency created by the spam. Get in contact with one or multiple members of your IT or security team, preferably by phone. They may be able to lock down your accounts until the attack subsides. Your first step should be to update your password.
Step 4: Share Passwords Securely
Ditch the spreadsheet. The vulnerabilities and workarounds are not worth it. Google Sheets and Excel were not built to secure sensitive data.
You may have heard of one-time-secrets. Problematically, the very feature that’s supposed to keep your data safe - a note that self-destructs - motivates people to write down the password in a Google doc or a sticky note.
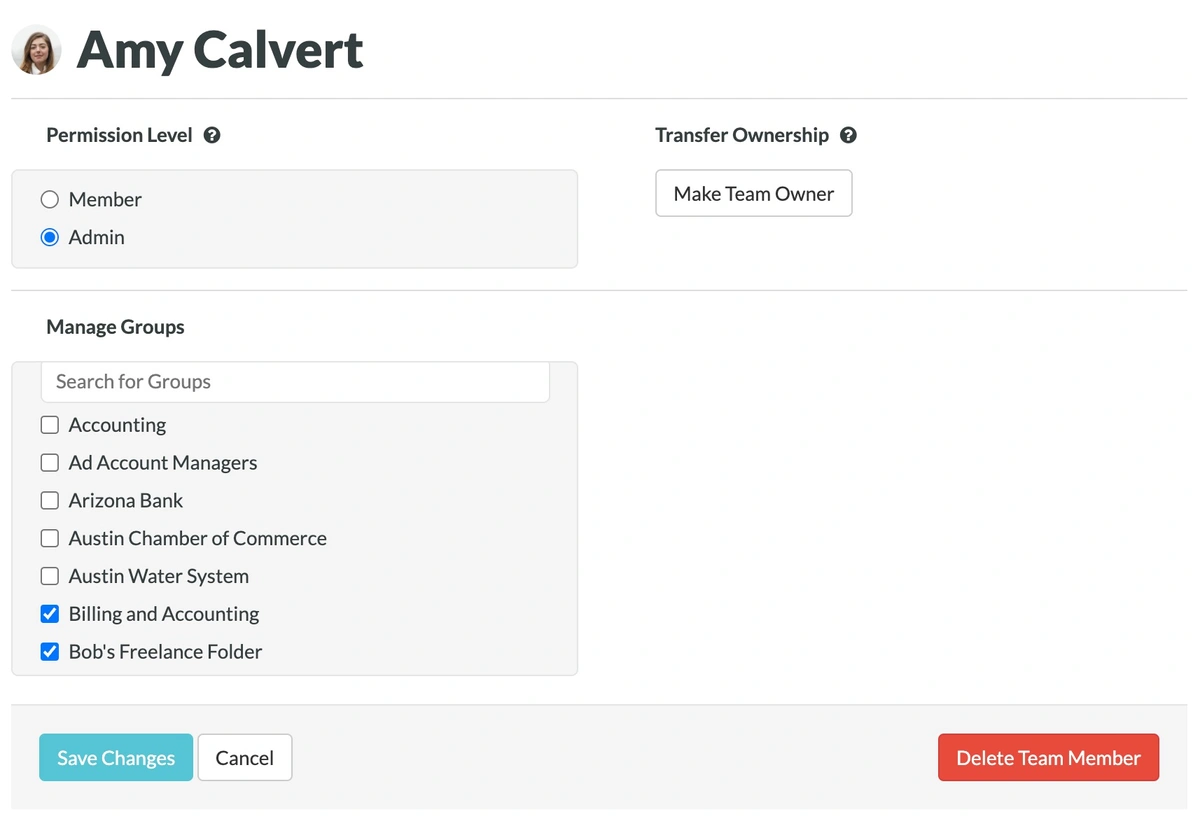
Businesses or families that share accounts will want a password manager with seats for each user, so that passwords never leave an encrypted environment.
Use your password manager to divide records into separate groups, and give access to those groups on a need-to-know basis. Add and remove access with a couple of clicks.
Your system needs to be so frictionless that managing passwords securely is easier than managing them carelessly. We revert to what's easiest for things we do every day. And most of us need our passwords every day.
Set yourself up to share passwords securely.
Step 5: Maintenance
Check haveibeenpwned. Change your passwords. If you knew someone was trying to break into your house, you’d change the locks, right? Unfortunately, people are trying to break into your online accounts all the time.
Monitor access
If you’re sharing passwords with your team, check your organization settings to make sure that only the people who should have access do.
If you think maybe you shared a password for an account once but you don’t remember for sure, be safe and go change it.
Setting up an email alias
Are you receiving a lot of junk mail? Your email may be on the dark web, and cybercriminals may have enough information about you to decide you’re ripe for a social engineering attack.
One trick to better track this (though not necessarily prevent it) is to use a different email alias for each service you sign up for.
If your email is [email protected], and you’re signing up for the company Untrustworthy Phone Carrier, then your email alias when signing up for that service is [email protected]. Then, you’ll create a filter in your email provider, telling it that if anyone sends an email to [email protected], it gets labeled “untrustworthyphonecarrier” or put in a specific folder. If you suddenly start getting phishing emails and spam under the label “untrustworthyphonecarrier”, you’ll know who leaked your email.
Here’s how to create a filter for your alias in a Gmail account:
-
Open search options to the right of the search bar in Gmail.
-
Put your alias in the “To” field. Click “Create filter”. You don’t need to touch anything else on this page. This filter should gather any email that is sent to this alias, regardless of who the email is sent from. If your labels are set up correctly, you’ll know who leaked it.
-
Click the “Choose label” dropdown, and create a new label. You’ll want to name this whatever the alias is named; in this case, examplecompany.
-
Click “Create filter”.
Now, don’t use this alias for anything else. If you receive spam addressed to [email protected], you’ll know exactly which company leaked it.
FAQs
Will passwords be replaced by Passkeys?
Passkeys are a long way from being universally supported. Passkey technology creates a faster, easier, and more secure sign-in experience for most users in most situations.
Many third-party password managers can store your passkeys, which attenuates the problem of platform vendors (Apple, Google, Microsoft) monopolizing you by only syncing passkeys across their own operating systems and browsers.
In short, passkeys will become more and more popular, but especially in the enterprise sector, passwords will remain in wide use.
Does a password manager make my password more secure?
No. Storing “123456” as your bank account password in a super secure password manager does not help you. Password managers assist you in good security habits; namely, using unique, long, randomized passwords. They do not nullify the dangers of weak passwords and poor cybersecurity hygiene.
What happens if the password manager gets hacked?
Great question. Yes, password managers do get breached. You may have heard of “Zero-knowledge architecture” which supposedly keeps your data safe even if the password manager is breached. Does it really? The short answer is: yes, but…
Zero-knowledge architecture refers to a system in which one party (the prover) can prove to another party (the verifier) that a certain statement is true, without revealing any additional information beyond the fact that the statement is true. Read the Ali Baba cave story for a conceptual understanding of zero-knowledge proofs.
How does this apply to password managers? Password managers should never have access to the encryption keys required to read your data. The master password you make when creating an account with them is encrypted (and later decrypted) locally on your device. This encryption involves salting and hashing, which I’ll briefly explain below in Part 2.
Here’s where it can go wrong.
Your password vault, though encrypted, is online. Login portals typically have something called Rate-Limiting, which just means that after a certain number of failed login attempts, the user is temporarily banned from further attempts. This counteracts brute-force or dictionary attacks. Hopefully, you’ve also set up MFA (multi-factor authentication) on your account.
Password managers keep backup vaults so that they can restore your vault to an earlier version in the event of a catastrophe. It's true, they do not have the key to this vault. It's completely encrypted and theoretically safe.
If a threat actor accesses the development environment, they may be able to take this backup vault offline, free of Rate Limiting, and brute-force the master password. Updating your master password won’t help in this scenario - you’ll need to update all the passwords in your vault so that even if the stolen backup vault gets cracked, the revealed passwords will be useless. Additionally, the multi-factor authentication on your password vault won’t help because the vault is offline (MFA will help if active for the accounts whose credentials are in the vault).
This is why it is essential that you create a super-strong master password for your password manager vault.
With enough computing power (i.e. money and time) your vault could still get cracked. Password generators tell you the strength of your password; some even estimate how long it would take a computer to crack your password. Anything from “centuries” to “millions of years” is considered secure, but please understand that these are estimates and not indicative of a motivated, funded threat actor, nor does it account for future technologies. We've seen repeatedly that the majority of breaches result from human culpability rather than ingenious hacking on the part of cybercriminals.
Can’t I side-step this issue by sticking to my notebook of passwords?
Length and complexity are the determining factors in password security, and most people don't like typing long, complex passwords again and again.
Even if you've got pro transcription skills, there remains the problem of lugging this notebook around with you for use on your phone, laptop, on vacation, at work, and so on,
If you don’t have length, you need a variety of symbols and characters to increase entropy. You could exclusively use four to five-word passphrases to make your passwords easier to type and more memorable while still being secure. But if the website in question has a 12-character limit for its password (yes, these exist, and it’s awful), you’ll be stuck typing a much messier or less secure password - your choice.
Ultimately, the notebook is impractical and makes good password hygiene so difficult that you’ll default to what many of us have done for years: reuse simple passwords.
If password hygiene is too difficult, you won’t do it.
What about my trusty spreadsheet?
Spreadsheets present a plethora of security hazards. Data within the spreadsheet is not encrypted, known vulnerabilities and workarounds for “encrypted” spreadsheets (MS Office password recovery attacks), no fine-tuned access/sharing controls, and the possibility of accidentally sharing all your passwords in plaintext are just a few reasons why spreadsheets are not secure.
Recap: Your Action Item Checklist
1. Locate and gather all of your passwords and accounts
-
-
Check Chrome’s password manager, Apple Keychain, notebooks, emails etc.
- Export your passwords
-
2. Create unique passwords for each account.
-
- Import passwords into a password manager.
- Use your password manager’s built-in generator to update all your passwords. Put on some good music; this is a long project.
3. Enable 2FA on all accounts
-
-
Do this while updating your passwords on your accounts.
-
4. Are you sharing passwords? Get something like TeamPassword. Get rid of the spreadsheet.
5. Maintain your defenses.
-
-
Pay attention to automatic scanning or periodically check haveibeenpwned.
-
Keep an eye out for news about password breaches that affect you. In severe breaches where sensitive personal details are leaked, you need to take action to protect your identity.
- Set reminders in your Google calendar to change passwords - 30-90 days for highly sensitive accounts
-
Have questions about password management and cybersecurity? Reach out to [email protected]. We're happy to share our knowledge and insights; we believe that if we each do a little bit more to ensure our individual safety online, collectively, we can make the internet a safer space for all of us.
If you're in the market for a password manager, you can try TeamPassword FREE for 14 days - no strings attached.