How to Securely Share Passwords With Your Team
Unsecured password sharing is one of the most common vectors for data breaches.
The challenge isn't stopping collaboration; it's enabling it through a secure, structured framework. This guide provides a professional playbook for implementing that framework.
Table of Contents
The Core Principles of Secure Password Sharing
To effectively manage team passwords, you must move from ad-hoc methods to a strategic, system-wide approach. These five principles are the pillars of a robust password security posture.
1. Implement a Business-Grade Password Manager: Your Central Vault
A reputable password manager designed for teams is the single most effective tool you can adopt. It serves as an encrypted, centralized vault for all team credentials.
-
Why It's a Non-Negotiable:
-
Zero-Knowledge Architecture: Leading password managers operate on a zero-knowledge model. This means the service provider cannot access your stored credentials, even if their own systems are compromised. All encryption and decryption happen locally on your device.
-
Robust Encryption: Your data is protected both in transit and at rest using industry-standard encryption algorithms like . This makes brute-force attacks computationally infeasible.
-
Audit Trails: They provide clear logs of who accessed which password and when. This accountability is crucial for security audits and investigating suspicious activity.
-
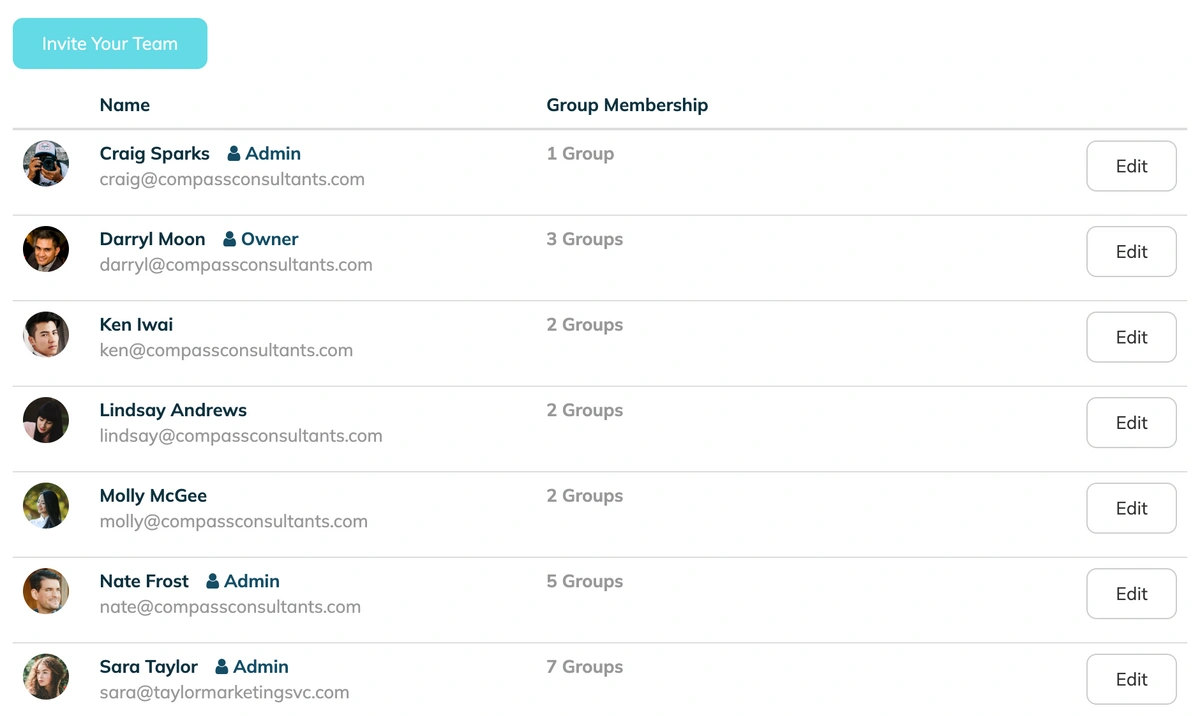
2. Enforce the Principle of Least Privilege (PoLP) with RBAC
The Principle of Least Privilege dictates that users should only have access to the specific information and resources they absolutely need to perform their duties. Role-Based Access Control (RBAC) is the practical application of this principle.
-
-
Why It's a Critical Layer:
-
Reduces Attack Surface: By limiting access, you minimize the potential damage if a single team member's account is compromised. An attacker can't access what the user can't.
-
Prevents "Privilege Creep": It stops employees from accumulating unnecessary access rights as they change roles within the company, which is a common and often overlooked vulnerability.
-
-
3. Mandate Multi-Factor Authentication (MFA)
MFA (often used interchangeably with 2FA) requires users to provide two or more verification factors to gain access. This is your strongest defense against compromised passwords.
Password managers like TeamPassword let you enforce 2FA for all users on your organization. Additionally, they offer an integrated TOTP authenticator so that shared accounts can be secured with 2FA.
-
-
Why It's Essential:
-
Stops Credential Stuffing: Even if a criminal has a team member's correct username and password (stolen from another data breach), they cannot log in without the second factor (e.g., a code from an authenticator app, a physical security key).
-
Layered Defense: It adds a crucial security layer directly at the point of entry for your most sensitive systems, including the password manager itself.
-
-
4. Establish a Formal Password Creation Policy
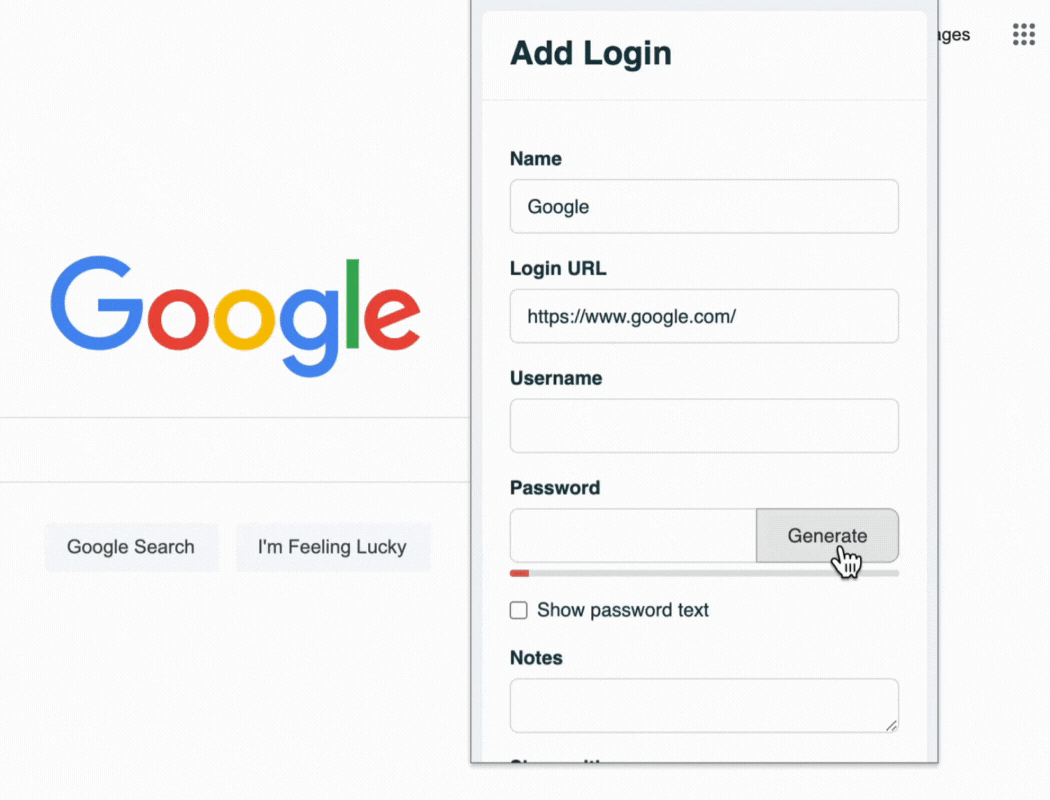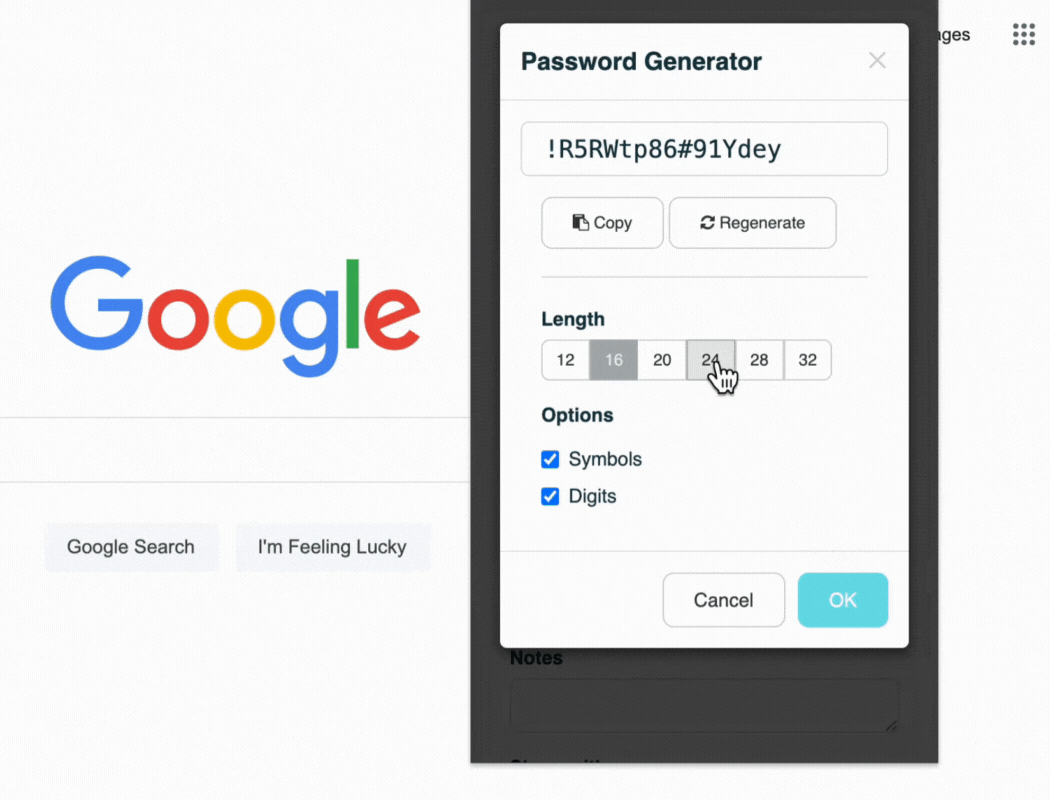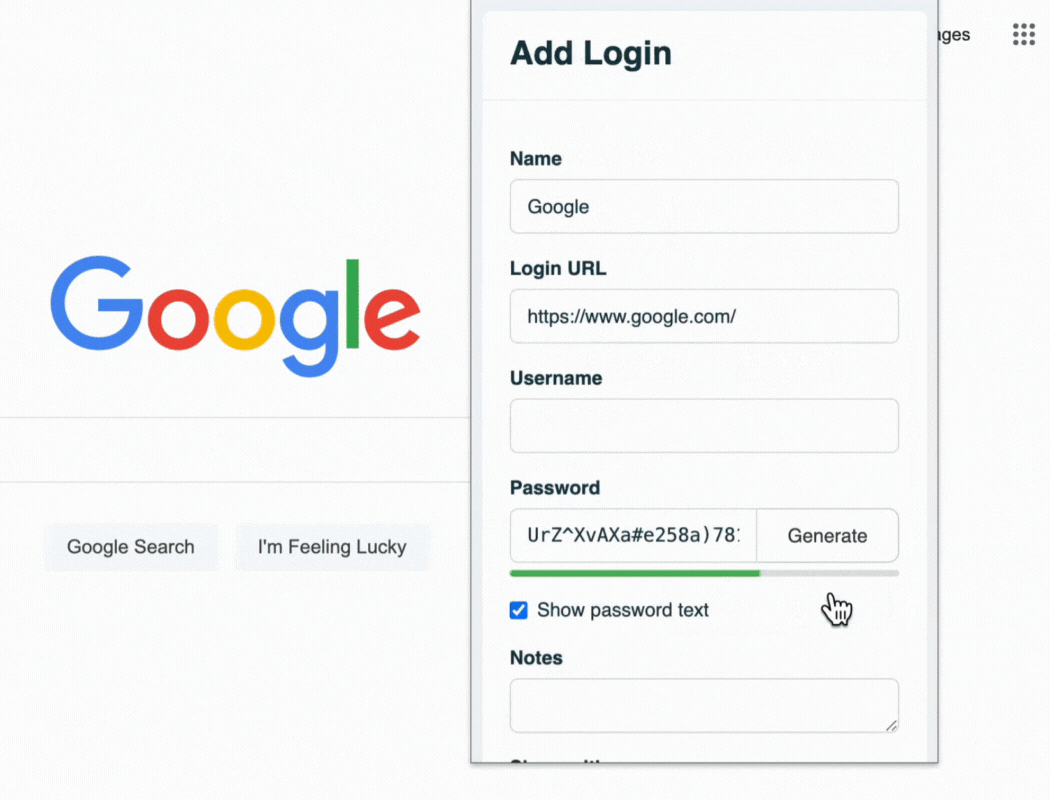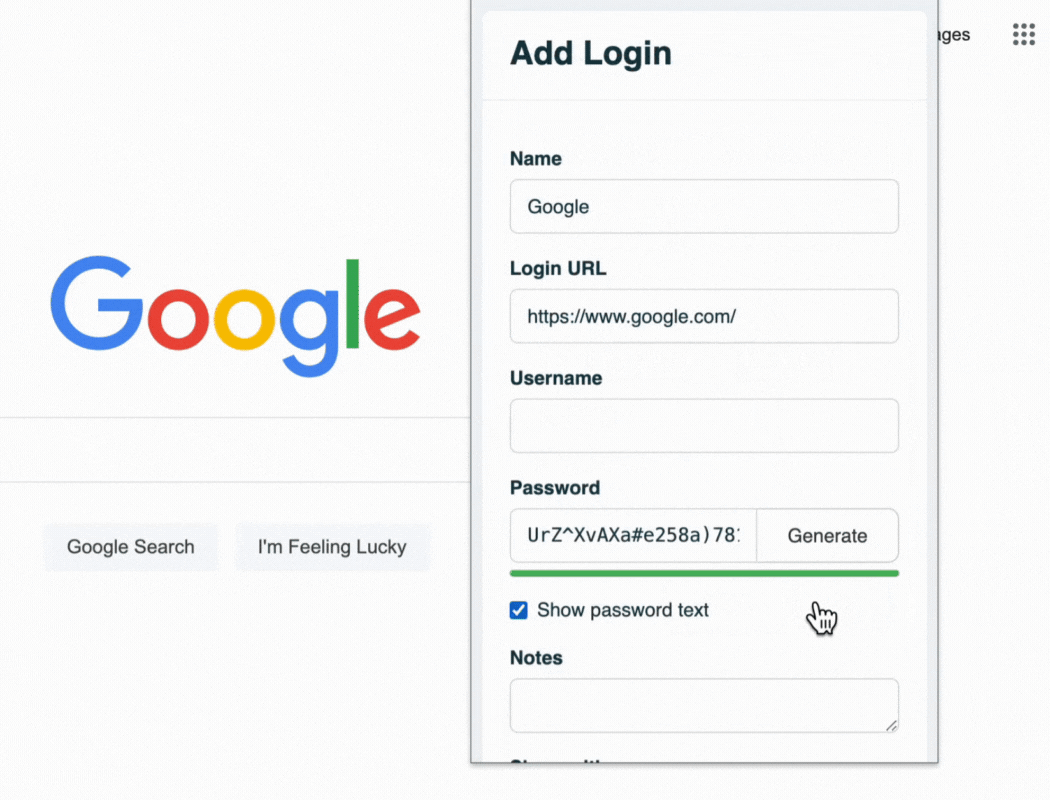
A strong vault is useless if the keys inside are weak. A password manager's generator should be used to create all new credentials.
-
Why It's Foundational:
-
Eliminates Password Reuse: The greatest risk of a third-party data breach is password reuse. If the same password is used for multiple services, a breach at one service exposes all of them. Unique passwords for every account contain the damage.
-
Enforces Complexity: Human-created passwords are often predictable. A generator creates long, random, and complex passwords that are resistant to guessing and brute-force attacks. For passwords that must be memorized, policy should mandate the use of secure passphrases.
-
5. Educate Team Members about Password Security
Provide ongoing education and training to your team about password security best practices. Emphasize the importance of using strong, unique passwords, avoiding password reuse, and never sharing passwords through insecure channels.
Why It's Secure:
- Well-informed team members are more likely to follow security protocols and maintain good password hygiene.
- Increased awareness helps prevent accidental security breaches and reduces the likelihood of falling victim to phishing attempts.
Approach cybersecurity training in a way that de-escalates feelings of overwhelm or incompetence. This video of an artist explaining basic cybersecurity is a great place to start.
In conclusion, securely sharing passwords with your team is crucial to maintaining the confidentiality of sensitive information. By using a reputable password manager with RBAC and 2FA features, implementing password rotation policies, and educating team members, you can significantly enhance the security of your team's password management practices. These measures will help safeguard your valuable data and protect your organization from potential cybersecurity threats.
Critical Risks: 11 Password Sharing Practices to Eliminate Immediately
1. Email Communication
- Email communication is not secure and can be easily intercepted or accessed by unauthorized individuals, leading to potential password leaks.
- Email is transmitted over the internet in plain text, making it vulnerable to interception at various points along the transmission path. Additionally, email accounts can be compromised through phishing attacks or weak passwords, giving attackers access to the password-sharing emails. Once intercepted or accessed by unauthorized parties, the passwords become exposed and can be used to gain unauthorized access to sensitive accounts and data.
2. Messaging Apps
- Messaging apps may lack end-to-end encryption, making passwords vulnerable to interception during transit or storage.
- While some messaging apps offer encryption, not all of them provide end-to-end encryption. Without end-to-end encryption, the passwords shared through these apps could be intercepted by hackers, service providers, or other parties with access to the communication channels or servers. Moreover, messages containing passwords might be saved on the devices used for communication, leaving them susceptible to unauthorized access if the device is lost or stolen.
3. Written/Physical Notes
- Sharing passwords through written or physical notes increases the risk of loss, theft, or accidental exposure, compromising security.
- Physical notes can easily be misplaced, lost, or stolen, providing a direct route to the sensitive information they contain. Additionally, leaving passwords written on sticky notes or notepads in plain sight can lead to accidental exposure if unauthorized individuals have access to the physical workspace.
4. Shared Spreadsheets or Documents
- Shared spreadsheets or documents can be accessed by multiple individuals, increasing the potential for unauthorized access to passwords.
- Storing passwords in shared spreadsheets or documents without proper access controls means that anyone with access to the file can view the passwords. It becomes challenging to track who has accessed or modified the passwords, making it difficult to identify potential security breaches or insider threats.
5. Verbal Communication
- Sharing passwords verbally is prone to human error and can be easily overheard, leading to unauthorized access.
- Verbal communication of passwords introduces the risk of mistakes, such as mishearing or forgetting the password. Additionally, sharing passwords verbally in open or public spaces can expose them to eavesdroppers, compromising security.
6. Using Personal Accounts
- Sharing passwords through personal accounts (e.g., personal email) lacks proper access controls and jeopardizes sensitive data.
- Using personal accounts for sharing passwords does not offer the same level of security as business or team-oriented platforms. Personal accounts might not have multi-factor authentication or proper audit trails, making it difficult to monitor and control access to shared passwords.
7. Plain Text Messages
- Sending passwords in plain text over any platform exposes them to interception or unauthorized access.
- Plain text messages do not provide any encryption, meaning the passwords are transmitted in clear, readable text. This exposes them to potential interception by hackers or malicious software, especially when transmitted over unsecured networks.
8. Generic or Weak Passwords
- Sharing generic or weak passwords among team members increases the risk of unauthorized access and compromises overall security.
- Generic or weak passwords are easy targets for brute-force attacks and social engineering attempts. If shared among team members, attackers who gain access to one password could potentially compromise multiple accounts.
9. No Access Revocation Mechanism
- Failing to revoke access to shared passwords when no longer needed leaves credentials exposed and vulnerable to misuse.
- As team members change roles or leave the organization, it's essential to revoke their access to shared passwords. Without proper access management, former employees or individuals who no longer require access might retain it, increasing the risk of unauthorized access.
10. No Password Rotation Policy
- Neglecting to change shared passwords regularly allows potential intruders more time to exploit any discovered credentials.
- Regular password rotation is essential for reducing the window of opportunity for attackers. If passwords are rarely changed, the risk of unauthorized access increases over time, especially if an insider or external threat manages to gain access to the shared passwords.
11. Shared Web Browsers
- Using shared web browsers with saved passwords exposes sensitive information to all users of that browser profile.
- When multiple individuals share a web browser with saved passwords, anyone using the browser can access the stored credentials. This lack of access controls can lead to unauthorized use of the passwords and compromise the security of the accounts they protect.
To maintain a robust security posture, it is crucial for teams to avoid these risky password-sharing methods. Instead, adopt secure password management tools, enforce strict access controls, and educate team members about the importance of password security.
Implementing Your Secure Sharing Strategy
Transitioning to a secure system is a straightforward process. The first and most critical step is choosing a platform built to solve this exact problem.
A business password manager like TeamPassword is designed to be the core of your security strategy. It provides the necessary infrastructure to implement the principles outlined above: a salted, hashed, and encrypted vault for your credentials, tools for RBAC, and streamlined sharing that integrates with your team's workflow without compromising security.
By adopting a dedicated solution, you can:
-
Securely transmit passwords where only the intended recipient has access.
-
Enable two-step verification for an added layer of protection.
-
Monitor activity logs to maintain accountability.
-
Generate unique, strong passwords for every account.
To see how these principles are applied in a real-world tool, explore a product tour or sign up for a free trial. Investing in the right system is an investment in your company's security, reputation, and operational integrity.