5 Reasons Your Smartphone Is At Risk
The importance of mobile devices has grown significantly as the number of internet users increases. Not only are they supremely convenient for communication and entertainment on the go, but many of the programs and websites we use at the office now exist in mobile applications - meaning we never leave our work behind.
Uninterrupted connectivity means uninterrupted risk of our data being stolen. Mobile devices, like any device connected to the internet and capable of data transfer, have vulnerabilities. And though mobile operating systems are often tightly secured and able to stop users from accidentally installing a virus, we should be just as educated and deliberate when using them.
Read on to learn five ways you may be unwittingly exposing your data.
Table of Contents
1. Outdated Security Software
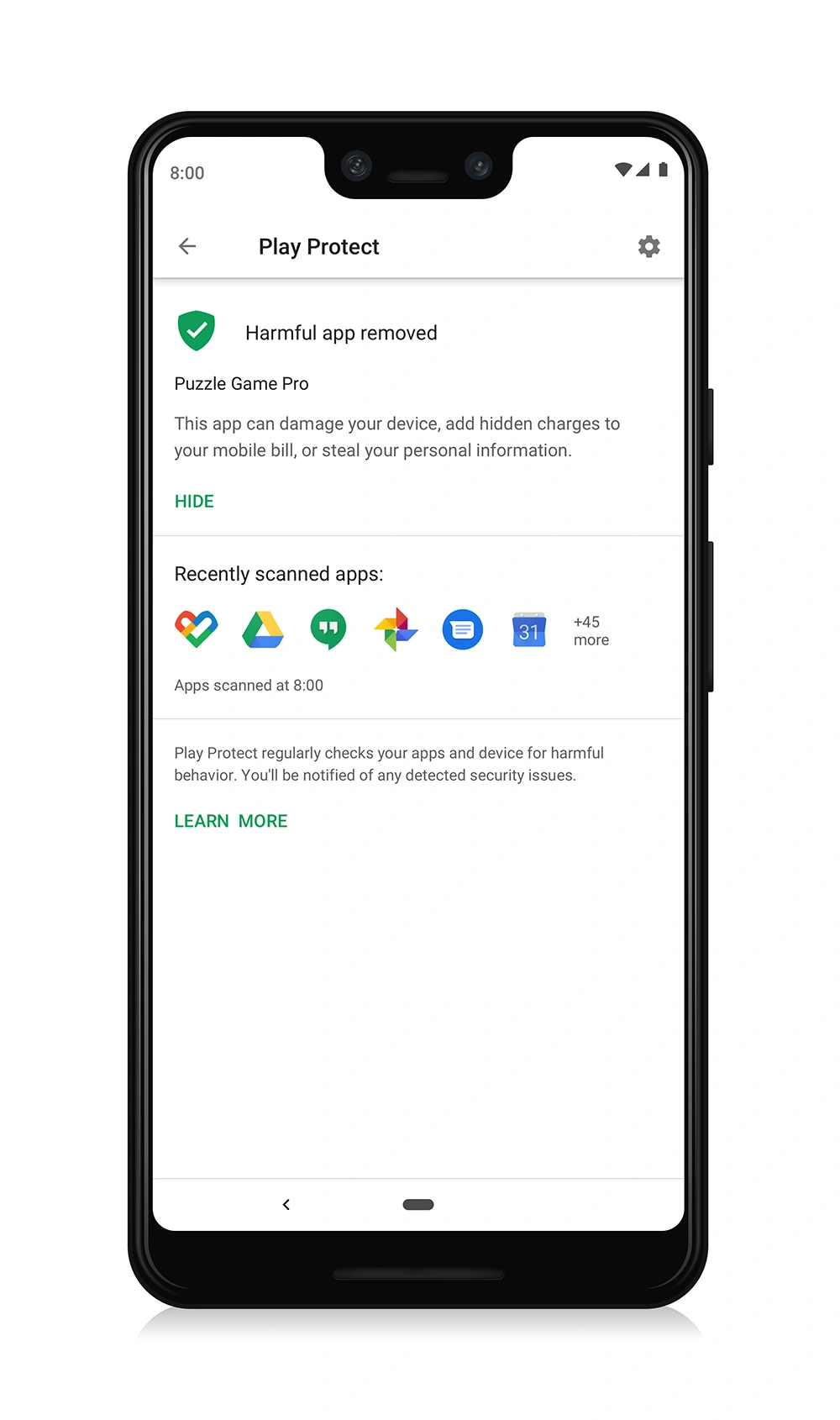
The two ubiquitous mobile operating systems, Android and iOS (and its cousin iPadOS), come with stringent security installed. On Android, Play Protect regularly scans your entire device for malicious apps, not just apps downloaded from the Play store.
iPhones employ a system whereby no app knows what any other app is doing, unless of course you give it that permission - such as allowing Instagram to look at your photos. Safari, the built-in browser on iPhones, typically does a good job of warning you when accessing a suspicious site. iPhones do not allow you to install third party security software unless they’ve been jailbroken (more on that below). The built-in security features on iPhones are typically enough, provided you keep your device up-to-date.
On that note: do stay on top of your software updates. Operating systems are regularly patched as new vulnerabilities are found - which is often.
For iOS devices, go to Settings > General > Software Update.
If you have an Android, your first step should be to ensure that Play Protect is working and scanning your device regularly.
Open the Play Store app > tap your profile icon > tap Play Protect. It will tell you the last time your device was scanned and if any threats were found.
And of course, check for software patches. Settings > System > System update (path may be different depending on the device).
If you use your Android device for banking, work, and research rabbit holes, you may want to invest in additional security.
When downloading any app it’s a good idea to check reviews first. Android apps have gotten better in recent years but bad ones still slip through. With so many different Android devices, it's not always easy to know how an app will perform. Reviews can help you pick the right app without trying a bunch of duds.
The next time you're looking for a new app, check the reviews to get a better idea of what you're getting yourself into. If you're concerned about your mobile device being hacked, install security software and keep it up to date. You should also choose strong passwords and avoid using the same password on multiple devices or websites.
2. Weak Passwords
A weak password is like a skeleton key that cybercriminals can easily guess. If your passwords are simple and reused across accounts you’re opening yourself to a comprehensive breach.
A good starting point for your passwords is to make them 12+ characters with a mix of letters, numbers, and symbols. How do you remember unique, complex passwords for all your accounts? You don’t. Let a password manager do that for you. Password managers have mobile apps, so there’s no excuse not to use one.
A password manager also removes the frustration of mistyping your passwords on touch keyboards.
Don’t just rely on your passwords. We strongly recommend enabling MFA (multi-factor authentication) on all applications that allow it. This means that in addition to your password you'll need a second factor, such as a security code from an Authenticator app, to access your account.
3. Sharing passwords via text, email, Slack etc
Text, emails, Slack messages, and other messaging apps are not appropriately encrypted for password sharing. Not only are the apps themselves comparatively easy to hack (or social engineer your way) into and intercept data from, but it’s simply too easy to misplace your phone. Once someone gets past your lock screen, how hard is it for them to get into your email, text messages, or workspace?
Passwords should live in a password manager with industry-standard encryption. If you need to share passwords with teammates or family, use a vault that allows easy sharing without the passwords needing to leave an encrypted environment.
4. Unverified Links
You may unwittingly compromise your passwords or install viruses when opening links on your mobile device. These can come from malicious websites, email attachments, or an unverified text message claiming your credit card has been compromised and that you need to “Click Here!” to freeze it (always call your bank directly).
Some websites may not be properly secured with HTTPS. Modern browsers should warn you when entering an unsecured HTTP environment. If you enter sensitive information on such websites, it may be visible to cybercriminals.
Please handle any suspicious content on a computer with good antivirus installed. If you must examine a link while using a mobile email app, long-press on the link or button to reveal the URL. If it’s not completely showing, copy the URL and paste it into your notes app.
For attachments and the like, only download them if you know you can trust the source.
5. Jailbreaking or Rooting Your Phone
Jailbreaking or rooting - technically two different processes - are typically done in order to install software or otherwise customize your phone in a way that the manufacturer does not allow by default. Jailbreaking is the term used when done to an iPhone, and is viewed by Apple as a violation of its end-user license agreement. Rooting - the process of becoming a superuser on Android - is allowed by a number of Android phone manufacturers.
In either scenario you are gaining power over your device that the manufacturer did not originally intend. With this increased control comes a proportional increase in risk. It becomes much easier to download malware, and if a criminal gets ahold of your privilege-escalated device, they can find ways to bypass your passwords to scour your storage for whatever information is held there. They can also control camera and mic permissions, enabling all sorts of nefarious activities.
The change in security of a rooted device typically renders it unusable for work. If you wish to root your phone, research the inherent dangers and proceed with a healthy dose of caution.
In Conclusion
As mobile devices become more capable, our trust in and reliance on them increases. Your smartphone may store credit card and bank info, addresses, pictures of ID, your physical location…do you even know what's on there? And it’s all on a device that can too easily be snatched from a coffee table or slip from your pocket.
I hope these five tips have helped supplement your knowledge and motivated you to take action to strengthen your mobile device security.
Enhance your password security
The best software to generate and have your passwords managed correctly.