How to protect company information when an employee leaves
Do you have an offboarding process ready to go?
Properly handing off company information when an employee leaves can be a significant challenge. What if the employee leaving has accounts created with their email address? What if they had access to sensitive data? What if they control the Starbucks rewards card?
Joking aside, a recent study in 2019 conducted by OneLogin found that 50% of ex-employees still had access to company databases. Of those surveyed, 20% of businesses had experienced data breaches by former employees.
Don’t stress! Your team can handle a smooth transition with the right plan. Here’s how!
Table of Contents
1. Develop Data Protection Policies
Protecting company data shouldn’t be a step you take after an employee submits their resignation letter. The first step in securing your data is to create a policy. Data protection policies should be in place for new hires and existing employees throughout their tenure.
Establish specific policies and procedures for employees who handle company data and clear penalties for those who do not abide by them. If you have a legal department, they should guide what the policy contains. If you don’t, there are examples online that you can use, but be sure to read through them and make sure that the policy fits your business. Having set policies is more transparent and will protect your organization from the risks of data theft or loss when employees move on.
When developing data protection policies, it’s essential to align them with broader government regulations such as GDPR, HIPAA, or CCPA, depending on your industry and location. These regulations often outline strict requirements for handling personal data and ensuring privacy, which can inform your internal procedures. For example, policies covering data access, storage, and disposal should reflect legal standards to avoid fines or legal repercussions. Clear documentation and employee training ensure that your company stays compliant with both internal policies and external laws, reducing the risk of breaches and enhancing security.
Have employees sign technology policies and keep them informed
Once you have a policy, it’s essential that all employees know the policy and, more importantly, abide by it. It may be worthwhile to create a "data security" training program for all employees at your company. Don’t have the time or the resources to develop a program? Some companies will do it for you.
Technology policies shouldn’t just be posted on the bulletin board; they should be read and signed. The act of signing gives the policy more importance and encourages employees to read through them more closely.
2. Limit Employee Access to Company Data
While employees need data and logins to accomplish their work, too much access poses data security risks. Not every employee needs unrestricted access to all of your business or client information. Instead, employees should only have access to the information necessary to do their jobs. This is called the Principle of Least Privilege (PoLP).
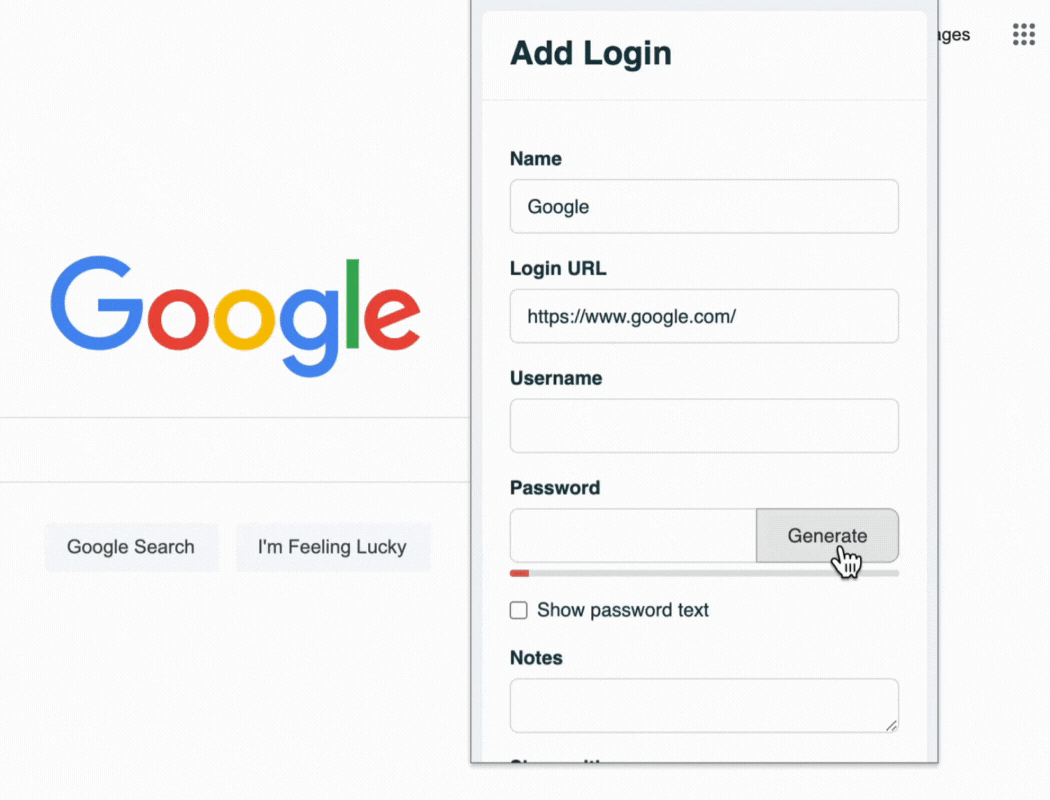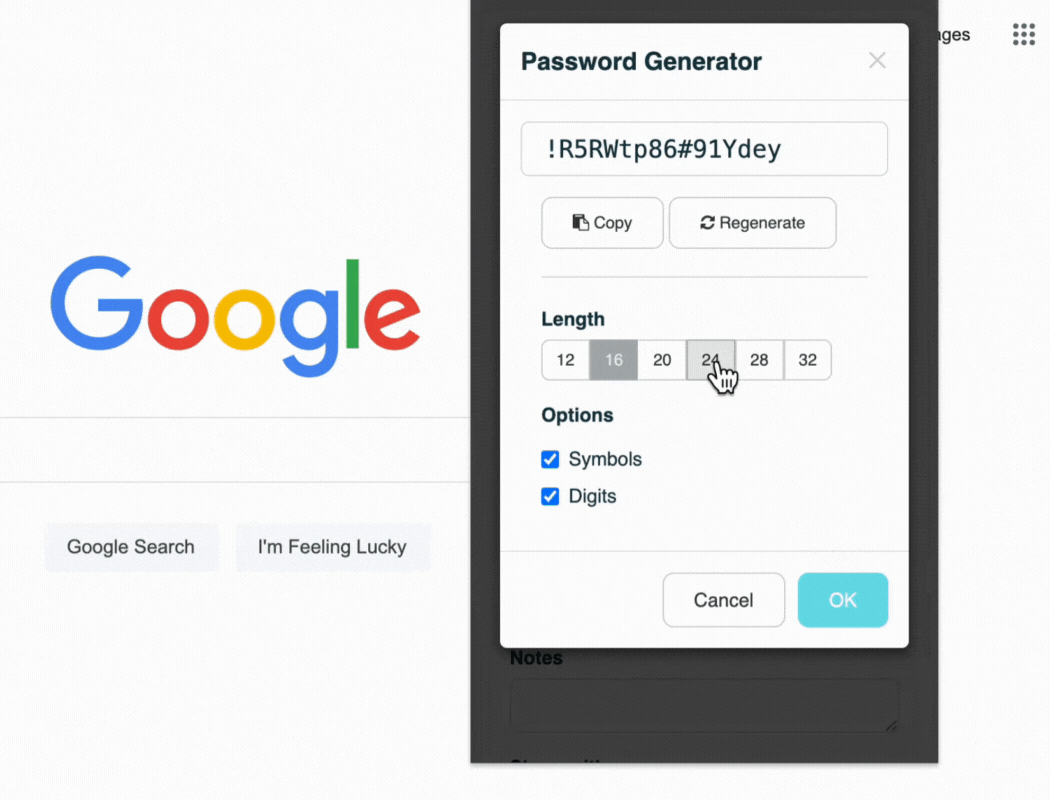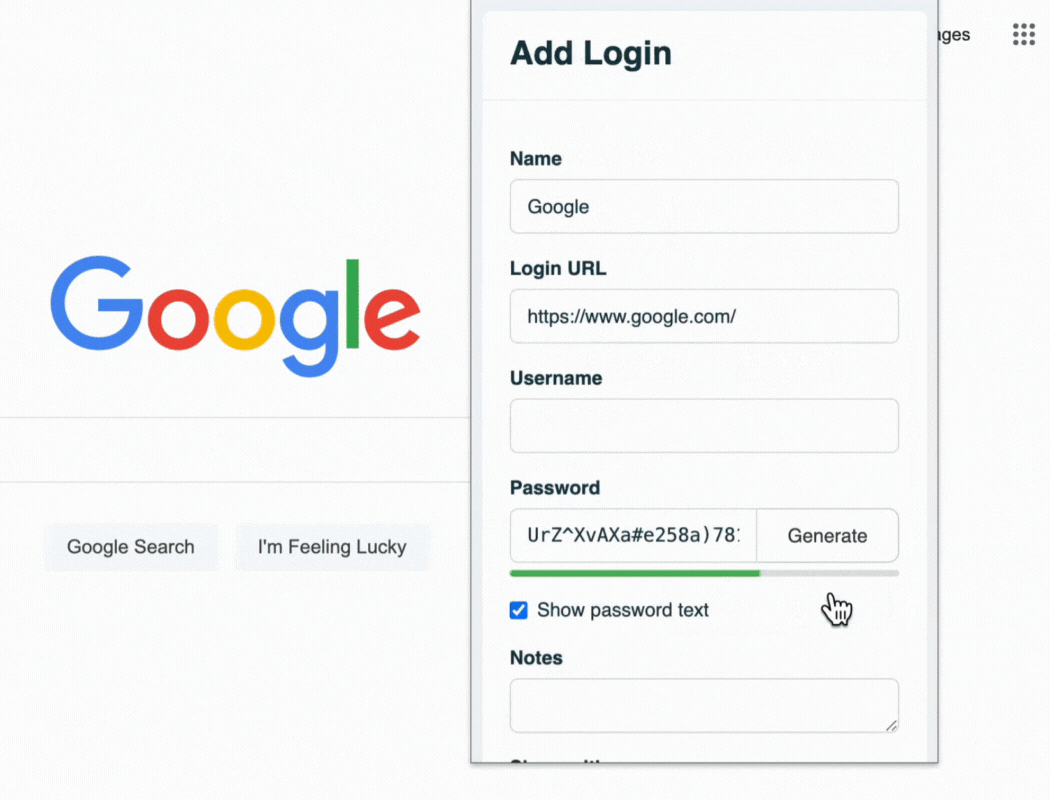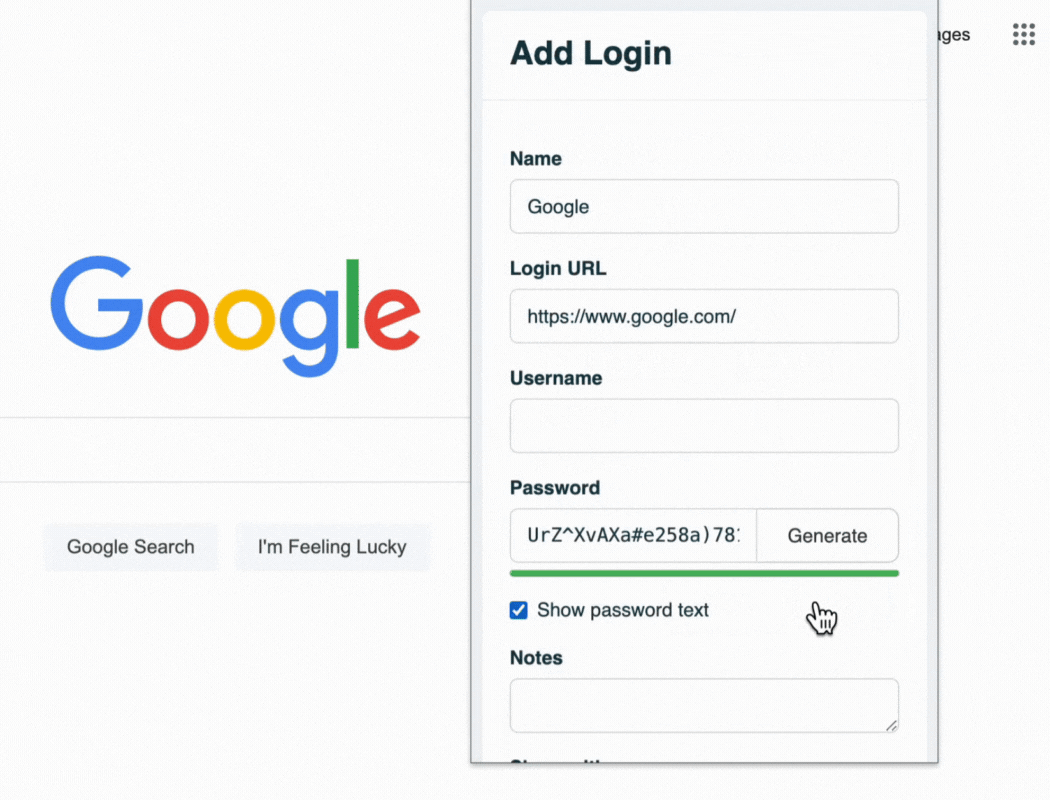
A common way to implement access levels is with a password manager. With a password manager, you can make groups such as marketing, accounting, and sales, and you can easily share and revoke access as needed.
Use a password manager to track activity and change logins
When an employee leaves, it will be essential to look out for significant download increases, strange access requests, and unusual file transfer loads. This is a common way to cause damage, and it can happen without you ever finding out if you aren’t tracking it.
So how can you be sure that no one is using logins after they’ve left or using data in strange amounts or weird times? You track it. One of the easiest ways is with a password manager. When you store all of your passwords with a password manager, an employee has to go through the password manager to log in, and when they do, it will show up on the activity log.
To prevent data breaches from ex-employees, it is best practice to change company passwords. A password manager makes easy to update passwords with new solid unique passwords for each account they had access to.
Control user access in a central authenticated system
It is essential to ensure employees are removed from everything, not just the big stuff. Damage can still be done with social media accounts or with other services like Photoshop, or customer service accounts like Intercom. Regaining control of accounts created by employees that have already left can be difficult. In worse cases, an employee can hold company accounts hostage. There have even been extreme cases where employees that still had access to the company's social media used them to tarnish the company's reputation.
A single sign-on system is one of the easiest ways to control access. When logins are controlled through one account like Google Workplace, it is far easier to give and revoke access with the click of a few buttons. No more trying to think of every login the employee had access to. Instead, you can remove them from everything all at once through the single sign-on system.
Set up accounts in a central location like Google SSO or Active Directory, and ensure all cloud applications are SAML authenticated. This makes it easier to manage and de-provision employee accounts.
3. Create and Use an Offboarding Checklist
To ensure data protection during employee exit, you'll need a standardized list to cover your bases. These include simple things that may be obvious, but you don’t want to push them off until the last possible second. These can include but are not limited to:
- Prepare necessary paperwork
- Conduct an exit interview
- Disable network access
- Recover company assets such as company credit cards, security badges, or keys
Making sure every possible security breach is on this list ensures all possible loose ends are tied up. Need ideas? There are plenty of examples online.
Disable all access
Plug the holes. A 2021 survey by Beyond Identity found that 83% of employees admitted to maintaining continued access to accounts from a previous employer. What’s more terrifying is that 56% of these employees did so with the specific intent of harming their former employer.
Here are a few steps to follow to ensure that every access point gets removed.
- If your logins are stored in a centralized location like Google SSO or active directory, immediately disable access and, after 30 days, delete it entirely.
- Change passwords, especially on shared accounts, to ensure they can’t access them with remembered or written down passwords.
- Redirect that employee's communication to an appropriate individual.
- Disable all access to the company network.
Recover and wipe company assets
Any company phones or laptops that the employee used should be returned and wiped of employee information. If anyone is allowed to work on personal devices, consider establishing a data recovery policy. If a remote wipe isn’t possible, there should be a policy that requires the departing employee to provide their personal device for cleaning.
Along with devices any keys, ID badges, or security cards should be returned. You should also close out any corporate credit cards or expense accounts in that employee’s name and process any fees or reimbursements.
4. Conduct an Exit Interview
One of the most important things you can do when an employee leaves your company is to understand why they’ve chosen to go. Exit interviews can be an invaluable tool to gain insight into your organization The advantage of having these conversations is that departing employees are more likely to give honest feedback. The feedback will help you identify areas that can help improve staff retention and the work environment and highlight ways to improve as management. A final conversation also allows the employee to leave on a good note whether they are choosing to leave themselves or being let go by the company.
When an employee leaves your organization, it's essential to prioritize data security. To mitigate the risk of sensitive information being compromised, consider the following steps:
- Reinforce Data Security Policies: Reiterate the importance of data confidentiality and review the company's data security policies with the departing employee.
- Conduct a Thorough Inventory: Identify all projects, files, and devices that the employee had access to. Ensure that all company materials are returned.
- Secure Company Devices: Collect the employee's company-issued devices and securely wipe them of any sensitive data.
Even unintentional data breaches can have severe consequences. Departing employees may inadvertently take confidential information with them, leading to potential legal issues and reputational damage.
While these general guidelines provide a solid foundation, your specific industry and company may require additional measures. For instance, if you handle highly sensitive data, you might need to implement more stringent security protocols.
Protect Company Passwords with TeamPassword
Tired of stressing over who knows your company passwords? TeamPassword is your solution. Our intuitive platform streamlines password management, ensuring your company's sensitive data remains protected.
Key Benefits:
- Effortless Access Revocation: Easily revoke access to company passwords for departing employees, preventing unauthorized access.
- Strong Password Generation: Our built-in password generator creates complex, unique passwords, enhancing your security posture.
- Seamless Password Management: Our browser extension allows you to update and save passwords directly from your browser, saving time and effort.
- Enhanced Visibility: Our activity log provides a clear audit trail, showing who has access to which passwords and when.
- Unparalleled Security: TeamPassword employs industry-leading AES 256-bit encryption to safeguard your passwords and supports multi-factor authentication for added protection, which can be enforced for your organization.
Don't take our word for it! Try TeamPassword FREE for 14 days. Simplify your password management, strengthen your security, and empower your team.