What are Extortion Emails?
Criminals use extortion emails to blackmail people. These criminals usually claim to have sensitive information or content that they threaten to forward to friends and family unless you pay.
The email will tell you that the sender has tracking software on your device and will make a vague statement about knowing you've visited porn sites. They also claim to have used your device's camera to capture you pleasuring yourself.
Extortion emails typically contain some personal data, like a password, stolen from a data breach. Even if the password is an old one, it can be shocking to learn that a stranger knows something private. Perhaps, what they are telling you is true!
From corporate data breaches to ransomware attacks and even personal extortion email scams—cybercriminals continuously find ways to steal data and money.
The 2021 T-Mobile data breach affected over 40 million users, less than a quarter of which were actual T-Mobile customers!
The most damaging case in recent memory is the LastPass breach, which seems to get worse every day. Even if it's not a password manager that gets attacked, most of these breaches lead to attackers stealing customers' personal data. The data stolen from breaches can be used to craft convincing extortion emails.
In this article, we will take a closer look at extortion emails and what you can do if they ever find your inbox!
What is Sextortion?
Sextortion is a type of extortion where criminals claim to have explicit content of you—usually nude, masturbating, or other sexually explicit content.
Sometimes users don't have explicit content, but information linking the victim to adult content like a cam site or dating website for married individuals—as was the case with Ashley Madison.
In the infamous Ashley Madison data breach, criminals only had account information linking the user to the website. This information could potentially ruin the victim's relationships or even bring public shame.
More than five years after the Ashley Madison data breach, criminals still contact users with sextortion demands.
With sextortion, the criminals usually have actual evidence of your actions—which they're happy to share with you via a short clip or screenshot.
In contrast, extortion emails typically use minor details (like an old password) to bluff you into believing that the sender has more incriminating content or information about you.
Table of Contents
What Are Some Examples of Extortion Emails?
The emails are usually somewhat lengthy with lots of threats, and the sender tries to portray themselves as authoritative. In the olden days, English extortion emails were usually poorly written with many spelling and grammar errors. With the help of artificial intelligence, modern extortion emails will probably be quite coherent and free from obvious grammar errors.
The email usually reveals something vague you're "guilty" of but could apply to many people, almost like a star sign.
It's important to note that if someone has incriminating evidence against you, they'll expose it because it'll ultimately increase the chances you'll pay!
Here is an extortion email example Malwarebytes Labs received from a victim:
"Hey, you don't know me. Yet I know just about everything about you...Well, the previous time you went to the adult porn sites, my malware was triggered in your computer, which ended up logging a eye-catching footage of your self-pleasure play by activating your webcam. (you got an unquestionably weird preference btw lmao)."
If you reply asking for proof, the sender threatens to send the video to 10 random people in your contacts list. The email shares a Bitcoin address where you should send $2,000 in Bitcoin.
In this particular email, the sender gives the recipient 24 hours to act. For anxious individuals, this sort of pressure could easily elicit a response.
Why Do Extortion Emails Work?
Priya Sopori, a partner at law firm Greenberg Gluster, says,
"They play on our basest levels of psychology. You will read personalization into any generic statement. And if you believe that there are hackers out there that know every aspect of your life, and maybe they even know your life better than you do, you might actually pay even if you've done nothing at all."
By the email's mocking tone, cybercriminals know precisely what buttons to push and how to make you feel ashamed, even for something you haven't done.
The humiliation that your friends and family might see you in the same light puts immense pressure on the victim to take action—paying the ransom to avoid embarrassment!
Who Uses Extortion Emails?
Hackers usually sell databases from data breaches on underground forums to the highest bidder, so it's difficult to say where your details end up.
Most of these databases end up with low-level cybercriminals who run similar rackets—like the IRS scams where fraudsters threaten to arrest you if you don't pay unpaid taxes immediately.
What to do With Extortion Emails
Let's talk about some practical steps you can take if you end up with one of these nasty emails in your inbox.
What should I do if I receive an extortion email?
If you receive an extortion email, follow these steps:
- Don’t respond or engage with the sender. Any reply could give the attacker more information about you or your habits.
- Do not click on any links or open attachments in the email, as these may contain malware.
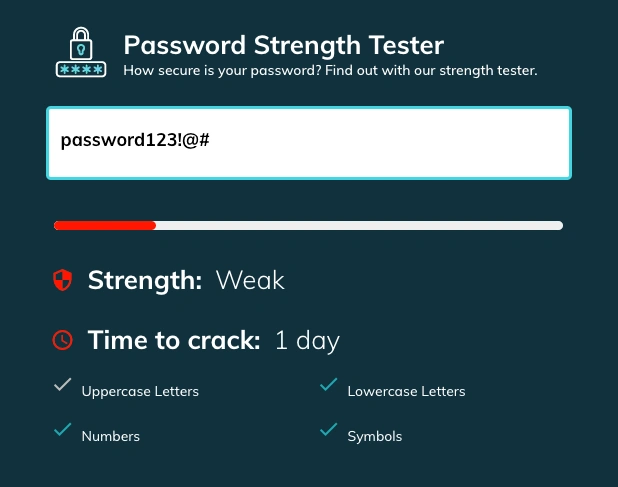
- Change your passwords immediately, especially if the email includes any password you still use. Use a password manager to create strong, unique passwords for each account.
- Report the email to your local authorities or cybercrime division. In the U.S., you can forward the email to the FBI’s Internet Crime Complaint Center (IC3).
- Delete the email after reporting it. Blocking the sender’s email address can prevent future threats from the same attacker.
How can I protect myself from extortion email scams?
You can protect yourself from extortion email scams with the following practices:
- Use strong, unique passwords for every account. A password manager can help you generate and store these securely.
- Enable two-factor authentication (2FA) on all your accounts. Even if your password is stolen, 2FA provides an extra layer of protection.
- Keep your software and devices updated, ensuring that security patches are installed regularly to prevent malware infections.
- Be cautious with your personal information online. Avoid sharing sensitive details on social media or public forums that attackers can use to target you.
- Be skeptical of unsolicited emails. If an email seems suspicious, verify the sender and the claims through legitimate channels before taking any action.
Change Your Passwords
Next, change the password for the account(s) where you use that password. Use a secure password generator and use a different password for every account!
You must never reuse the same password for multiple accounts. If attackers steal your password from a data breach, they can easily access the other accounts you use through what's called credential stuffing.
Should I Pay the Ransom from an Extortion Email?
No, you should never pay the ransom demanded in an extortion email. Paying the ransom only encourages the attacker and makes you a continued target for future scams. Here's why paying will likely worsen the situation:
-
Criminals Rarely Stop at One Payment: Once you've paid, attackers know you're willing to give in to their demands. It's highly likely that they will return with more threats, demanding additional payments. For example, in a real-life case, Hollywood Presbyterian Medical Center was hit with a ransomware attack in 2016. The hospital initially paid a $17,000 ransom to regain access to its systems. While this temporarily resolved their issue, other hospitals became targets soon after, sparking a wave of similar attacks across the healthcare industry.
-
Your Details Could Be Sold or Exposed to Other Criminals: Paying a ransom also marks you as an "easy target" in the criminal world. Once you've been labeled as someone willing to pay, your information could be sold on the dark web to other scammers or cybercriminals. In the infamous WannaCry ransomware attack of 2017, while some victims paid the ransom, their data was later found for sale online, making them vulnerable to future attacks.
-
No Guarantee the Attacker Will Honor Their Word: There's no reason to believe that paying the ransom will actually stop the attacker from leaking the alleged information or content. In many cases, cybercriminals have no actual evidence—they're bluffing. Even if they do have incriminating data, there's no guarantee they'll delete it or refrain from using it in the future.
-
Legal and Financial Risks: Paying ransoms may also be illegal in certain regions, depending on the cybercriminal’s affiliation with sanctioned entities or countries. Some governments have strict regulations around making ransom payments, and you could inadvertently violate the law by paying. For instance, U.S. authorities have issued warnings against paying ransoms to cybercriminals linked to foreign terrorist organizations, which could lead to significant legal consequences.
If you know the attackers have incriminating details or content against you, consult your local authorities on how to proceed with the matter. Do not attempt to reply or negotiate on your own!
How to Deal With Extortion Emails at Your Company
Although less common, extortion emails also target businesses. The sender might run a similar scam, exposing a company password as "proof" that the criminals have more incriminating information.
Most companies have pretty robust spam filtering, so these emails never reach the intended inbox. But companies must react appropriately.
As with extortion emails targeting individuals, companies must never engage with the sender! Report the email to authorities and delete it immediately. Add that email address to your blocked senders.
Change Passwords Immediately
Even if the password the sender revealed is old, change your passwords immediately, especially if you have used that password for multiple accounts—poor habit companies should stop immediately.
Using a password manager like TeamPassword will prevent companies from using the same credentials more than once. TeamPassword's built-in password generator allows you to create strong passwords from 12-32 characters using uppercase, lowercase, symbols, and numbers.
Secure Company Passwords with TeamPassword
Protecting your company's digital assets starts with secure password management. Companies need to share passwords with coworkers while maintaining high levels of security.
Here's how TeamPassword can help!
One Password Manager for Every Account!
Instead of sharing raw login credentials, each team member (including clients, freelancers, and contractors) gets a TeamPassword account.
Team members then use one of TeamPassword's browser extensions (Chrome, Firefox, and Safari) to log into social media accounts, productivity apps, marketing tools, and other web applications. Similar to how Google Chrome remembers your passwords.
So why not just use Google Chrome?
Passwords saved in your browser can be helpful for individual use but pose many security vulnerabilities and don't work well for sharing passwords securely.
Groups and Sharing
TeamPassword is built for sharing. You create groups for your various accounts, clients, or however you wish to distribute access.
Instead of sharing raw credentials, you add relevant coworkers to a group. This feature allows you to limit access to those who need it and prevents team members from sharing passwords, preventing unauthorized logins.
When a team member no longer needs access, simply remove them with one click. No need to change passwords every time someone leaves a project!
Two-Factor Authentication (2FA)
2FA is your second line of defense for secure password management. Even if attackers steal a team member's credentials, 2FA prevents them from accessing your TeamPassword account.
TeamPassword lets you enforce 2FA for your entire organization.
Activity & Notifications
TeamPassword's activity log monitors team activity so you can see who accessed what credentials and when, if the credential was edited etc.
You can also get instant email notifications for all TeamPassword actions, allowing you to track sensitive accounts or data.
Protect your team from extortion email scams with TeamPassword’s secure password sharing solution
Don't let your company fall victim to extortion emails, credential stuffing, and other password vulnerabilities. Let TeamPassword take care of security while you focus on growing a successful business!
Sign up for a 14-day free trial to test TeamPassword with your team members today.