Biometric Identification: What Is It?
Biometric ID is the process of using unique physical (e.g., fingerprint or vein pattern) or behavioral (e.g., gait or handwriting) traits to identify an individual. Biometric technologies use these unique and measurable qualities to perform security actions in lieu of traditional security measures, specifically passwords.
First, a user is expected to provide documentation of their identity. This documentation can be specific to the trait or tied to the individual.
For example, the registration of your fingerprint on your phone allows you to access your phone with your fingerprint in the future, but it does not tie your fingerprint to your personal identity.
Conversely, in some high-security situations, for example immigration documentation, the biometric identification can be made simultaneously to both the documentation and to your identification. For example, you may have a fingerprint and facial recognition image attached to your passport so that an airport official can confirm both that you are the owner of the passport and that the passport is valid to the personal identification on file.
For this reason, even the best biometric identification system is only as effective as its ability to discern your biometrics and the veracity of the information stored in the system.
Note that while we will briefly differentiate between biometric identification and biometric authentication, they can be used interchangeably for much of the discussion.
Table of Contents
What does biometric identification mean?
Throughout this article, we are going to explain exactly what biometrics means in different contexts. However, the simple answer is that biometric identification is the use of personal traits - physical or behavioral - for security purposes.
You probably use biometrics to open your smartphone. Depending on how old your smartphone is, that might be using your thumbprint to open the screen or the phone performing facial recognition.
Biometric identification is found across many different industries. You’ve probably experienced some forms of biometric identification at airports and hospitals.
Biometric authentication vs. biometric identification
As mentioned above, biometric identification is really only half of what biometrics can accomplish. The other main task is called biometric authentication.
Biometric authentication
Biometric authentication is when a computer is tasked with determining the resemblance of a person to their template by measuring some trait. In essence, the computer is tasked with answering the question: “Are you person X?” This is accomplished according to the steps below:
- Before the authentication actions, the template must be stored. That is, the template is registered to the system.
- Then, when the person seeks authentication, their scanned information is compared to the stored data.
Biometric identification
Biometrics identification is slightly more complicated. In this case, the computer is tasked with determining the identity of an individual. Here, the question to be answered is: “Who are you?” This is accomplished by the following steps:
- Sensors record one or more traits of an individual whose identity is to be determined. These can be physical traits such as fingerprints or behavioral traits such as gait.
- The collected information is then compared to the stored biometric data of different people in a database.
Biometrics performance
This part is quite technical and so I recommend interested people spend some time on Wikipedia as we are really only going to gloss over the basics. You can find more information here (biometrics) and here (entropy). Be warned though, as the rabbit hole on entropy is deep!
Essentially the ability of a biometric technology to discriminate among different individuals is based on the amount of entropy they can encode and use when matching.
The entropy of a random variable in information theory (which is different from the entropy used in physics) is the average level of uncertainty inherent in the variable’s possible outcomes.
The following are used as performance metrics for biometric systems (their definitions can all be found on the Wikipedia pages linked above):
- False match rate (FMR, also called FAR (false accept rate))
- False non-match rate (FNMR, also called FRR (false reject rate))
- Receiver operating characteristic or relative operating characteristic (ROC)
- Equal error rate or crossover error rate (EER or CER)
- Failure to enroll rate (FTE or FER)
- Failure to capture rate (FTC)
- Template capacity
What are examples of biometrics?
As alluded to above, there are two types of biometrics: physical measurements and behavioral measurements. Let’s take a look at both below and then consider a list of specific types of biometrics used for identification and authentication.
Physiological measurements
Physiological measurements can be separated into morphological and biological types:
- Morphological identifiers: The main morphological identifiers are fingerprints, hand shape, vein pattern, face shape, and the eye (iris and retina).
- Biological identifiers: These are mainly used in medicine or by the police and include DNA, blood, saliva, or urine.
Behavioral measurements
There are many behavioral measurements used for biometric identification. They include voice recognition, signature dynamics (the speed, acceleration, inclination, and pressure of pen strokes), keystroke dynamics (similar to signature dynamics but relating to how you type), the way we use objects, gait, the sound of steps, and gestures.
Specific types of biometrics
The following are some specific biometric identification examples.
- DNA matching: This is as straightforward as it is scary.
- Ear: Surprisingly, ear shapes are unique and can be used for identification.
- Eyes (iris recognition): Iris features have been the focus of biometric identification research for a long time.
- Eyes (retina recognition): The retina is also being used.
- Face recognition: Facial features including the overall shape and pattern are currently being used for identification.
- Fingerprint recognition: The fingerprint has been used to identify people for a couple thousand years!
- Finger geometry recognition: The next step in fingerprint identification is actually using the 3D geometry of the finger.
- Gait: Made famous in a Mission Impossible movie, people have unique gaits and they can be measured using cameras.
- Hand geometry recognition: Similar to recognizing the geometry of a finger, the whole hand can be measured.
- Odor: Every individual produces unique odors from their mouth, etc., and it is totally not disgusting to identify people using this.
- Typing recognition: The force and speed, not to mention finger choice, when typing can be used to identify a person.
- Vein recognition: The vein pattern of a finger or hand can be used for biometric identification.
- Voice: A speaker’s voice can be used for biometric identification and authentication.
- Signature recognition: While signatures of different sorts have been used with varying success for thousands of years, now the way a person signs (from the pressure on the pen to the speed and acceleration of pen strokes) can now be used for more accurate identity verification.
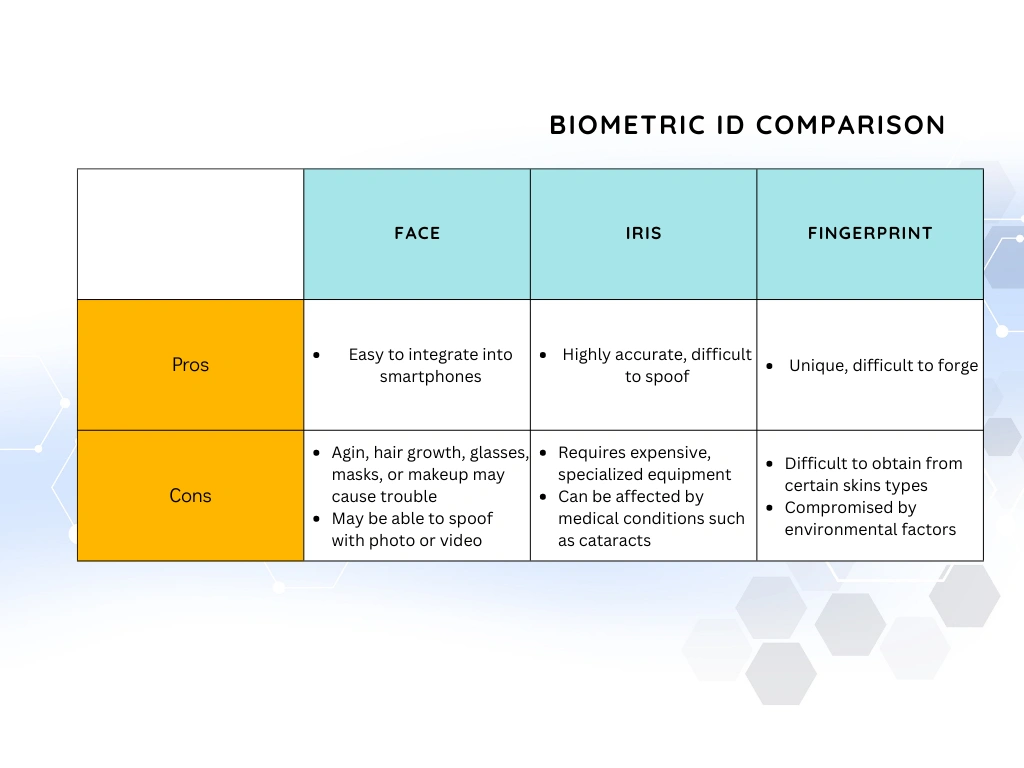
Pros and Cons of Common Biometric Identifiers:
Different types of biometric identification have different advantages and disadvantages. Some of the most commonly used biometric modalities include fingerprints, facial recognition, iris recognition, voice recognition, and hand geometry.
Fingerprints
- Pros: Fingerprints are unique to each individual and are difficult to forge. They are also widely accepted and have been used in forensic investigations for many years.
- Cons: Fingerprints can be difficult to obtain from certain individuals, such as those with dry or rough skin. They can also be compromised by environmental factors, such as dirt or moisture.
Facial recognition
- Pros: Facial recognition is non-intrusive and easy to use. It can be used to identify individuals from a distance and can be integrated into devices such as smartphones and cameras.
- Cons: Facial recognition can be affected by changes in an individual's appearance, such as aging, hair growth, or wearing glasses. It can also be compromised by the use of masks or makeup, or by the use of photographs or videos to spoof the system.
Iris recognition
- Pros: Iris recognition is highly accurate and difficult to spoof. It is also non-intrusive and can be used to identify individuals from a distance.
- Cons: Iris recognition requires specialized equipment, such as infrared cameras, which can be expensive. It can also be affected by certain medical conditions, such as cataracts.
Voice recognition
- Pros: Voice recognition is easy to use and can be integrated into a wide range of devices. It is also non-intrusive and can be used to identify individuals from a distance.
- Cons: Voice recognition can be affected by changes in an individual's voice, such as a cold or hoarseness. It can also be compromised by the use of recordings or synthetic speech to spoof the system.
Hand geometry
- Pros: Hand geometry is non-intrusive and easy to use. It can be used to identify individuals from a distance and can be integrated into a wide range of devices.
- Cons: Hand geometry can be affected by changes in an individual's hand shape, such as injuries or weight gain/loss. It can also be compromised by the use of fake hands or gloves to spoof the system.
No biometric system is foolproof, and all have some level of error rate. The choice of the biometric system depends on the use case, the security level required, and the cost-benefit analysis.
Advantages of biometric identification
The following are only some of the advantages of biometric identification. Biometrics are:
- Universal: We all have them.
- Unique: We all have different ones.
- Permanent: The ones we have (usually *) don’t change.
- Recordable: You can record them (but hopefully you ask us first).
- Measurable: You can turn them into numbers for future comparison.
- Forgery-proof: We keep them with us and you can’t take them (usually **).
* There is the possibility that, e.g., your face is damaged in an accident and then you cannot use it for facial recognition. This is an example of one of the ongoing controversies with biometric identification.
** There was a Malaysian car thief who cut off a victim’s finger to steal their Mercedes. This is an example of another of the ongoing controversies with biometrics.
Why is biometric identification controversial?
Biometrics have many advantages, but no technology is without disadvantages and those of biometrics are particularly unsettling.
Surveillance humanitarianism in times of crisis: While humanitarian efforts are noble in their motivations, i.e., helping those in times of need, different groups may have different specific goals and segmenting people through biometrics could lead to questionable distributions of aid.
Human dignity: The use of biometrics has been a boon to authoritarian regimes and led to the dehumanizing processing of individuals as they can become a set of values.
Privacy and discrimination: Any data obtained during biometric enrollment could be used nefariously without consent. Many of the traits measured could disclose physical or neurological disorders that could lead to discrimination.
Danger to owners of secured items: As mentioned above, if a finger or iris is needed as part of a larger crime, it could put someone at bodily harm.
What are some effective attacks on biometric identification?
The primary attacks performed against biometric identification fall under the category of Presentation Attacks (also known as "spoofing attacks"). These are attempts to bypass biometric authentication systems by presenting a fake or manipulated biometric sample and can take many forms, depending on the type of biometric being used.
Presentation Attacks
The most advanced attacks now incorporate multiple layers of deception:
Fingerprint Attacks
- Advanced Material Synthesis
- 3D-printed fingerprint replicas using nano-level precision
- Biocompatible synthetic skin with precise ridge and valley replication
- Electrically conductive artificial skin that mimics human skin's electrical properties
- Deepfake Fingerprint Generation
- AI-generated fingerprint patterns that can fool even advanced sensors
- Machine learning algorithms that create statistically plausible fingerprint variations
Facial Recognition Attacks
- Hyper-Realistic Digital Manipulation
- AI-generated deepfake videos with near-perfect facial movements
- Volumetric capture technologies that create three-dimensional facial replicas
- Synthetic facial models that adapt in real-time to liveness detection challenges
- Computational Synthesis Techniques
- Generative adversarial networks (GANs) that create undetectable facial variations
- Machine learning models that can predict and simulate micro-expressions
Voice Recognition Vulnerabilities
- Voice Synthesis Attacks
- Real-time voice cloning with emotional nuance and background noise simulation
- Artificial intelligence that can generate voices indistinguishable from human speakers
- Contextual voice synthesis that understands and mimics conversational patterns
- Advanced Voice Replay Techniques
- Sophisticated audio processing that eliminates detection markers
- Multi-channel voice reconstruction that defeats traditional anti-spoofing mechanisms
Emerging Attack Vectors
Behavioral Biometric Exploitation
- Machine Learning Pattern Prediction
- AI algorithms that can simulate typing patterns, walking gaits, and mouse movement characteristics
- Sophisticated statistical modeling of individual behavioral signatures
- Cross-Platform Behavioral Synthesis
- Attacks that combine multiple behavioral biometric data points
- Contextual adaptation of synthetic behavioral profiles
The Future of Biometric Identification in Technology
The future of biometric identification in technology is expected to bring advancements in areas such as accuracy, convenience, privacy, and security. Some of the key trends and developments in the field include:
-
Increased use of multi-modal biometrics: Combining multiple types of biometrics, such as fingerprints, facial recognition, and iris recognition, can increase security and provide a more robust form of authentication.
-
Advancements in liveness detection: Liveness detection is a technique used to ensure that a biometric sample is from a live person and not a spoof. Advancements in this area will help to prevent spoofing attacks and increase the security of biometric systems.
-
Greater use of biometrics in the cloud: Cloud-based biometric systems can provide more scalable and efficient biometric authentication and identification.
-
Development of biometric-based payment systems: Biometric authentication could be used for online and in-store payments, replacing traditional methods such as cards and cash.
-
Greater use of biometrics in IoT and smart homes: Biometrics can be used to authenticate users and control access to smart devices and appliances in the context of IoT.
-
Advancements in deep learning and Artificial Intelligence: These technologies are expected to help improve the accuracy and speed of biometric systems, as well as making it more difficult to bypass the systems with spoofing attacks.
-
Biometrics becoming more privacy-sensitive: Biometric data is sensitive and its collection, storage, and use must be done with the highest security and privacy standards. Biometrics providers and users will have to adapt to regulations, such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA), to ensure data privacy and security.
Overall, the future of biometric identification in technology is expected to bring more convenient, secure, and accurate forms of authentication and identification, which will be increasingly integrated into our daily lives.
Will Biometrics Replace Passwords?
The digital authentication landscape has undergone a remarkable transformation in recent years, with passkeys and advanced biometric technologies fundamentally reshaping how we secure our digital identities.
Passkeys, which leverage public key cryptography and are deeply integrated with device-based biometric authentication, have become a game-changing technology. Unlike traditional passwords, passkeys provide a more robust and seamless authentication method that combines the strengths of cryptographic security with the convenience of biometric verification.
It is expected that biometric identification will play a larger role in the future of authentication and may eventually replace the use of passwords and other traditional forms of authentication in some cases. Biometrics offer several advantages over passwords, such as:
- They are unique to each individual and cannot be easily forgotten or lost like a password can.
- They are difficult to steal or imitate, making them more secure than a password that can be guessed or hacked.
- They provide a convenient and user-friendly way to authenticate, as users do not have to remember or enter a password.
However, it is unlikely that biometrics will completely replace passwords in all cases. Passwords still have some advantages, such as being more private, and can be used in situations where biometrics cannot, such as when the user is in an environment where capturing a biometric sample is not possible, or when the user is concerned about privacy. Additionally, biometrics, as any technology, can have errors and can be compromised. Therefore, it is likely that a multi-factor authentication approach, which combines biometrics with other forms of authentication such as passwords, security questions, or tokens, will become the norm.
Summary
Biometrics are useful security tools, but like all tools they are not immune to their own threats or controversies. In the never-ending hunt for stronger and simpler security—and, indeed, simpler often means stronger—biometrics will almost certainly continue playing a role.
From iris, face, or thumbprint recognition on your smartphone, to the futuristic biometrics identification showcased in the latest spy thrillers, biometrics are here to stay as part of the security ecosystem. However, the disadvantages are significant enough that we don't see passwords disappearing anytime soon.
Regardless of how ready you are to adopt biometric authentication methods, the technology is a ways from being ubiquitous. A strong password manager should be part of your security protocol.
If you need to share passwords with teammates or family, do so securely with TeamPassword.
When you save a new password, the data is hashed, salted, and encrypted locally on your computer before being uploaded to TeamPassword via an encrypted connection.
If you’re unsure where to begin, sign up for a TeamPassword free trial to secure your shared passwords once and for all.