What to Do if You've Been Pwned: A Complete Guide
That sinking feeling in your stomach when you hear about another massive data breach is all too common. You immediately wonder: "Was my information stolen? Is my email address floating around the dark web?"
In the past, it was nearly impossible for the average person to know. But now, you have a powerful tool in your corner: Have I Been Pwned? (HIBP). This guide will not only show you how to use this essential service but will also provide a clear, step-by-step action plan for what to do if you discover your data has been compromised.
Table of Contents
What is "Have I Been Pwned" (HIBP)?
Imagine a massive, searchable library of information stolen in data breaches. That’s exactly what Have I Been Pwned? is. Founded by renowned Australian security expert Troy Hunt in 2013 after the colossal Adobe breach, HIBP is a free service that aggregates and indexes billions of leaked accounts.
The term "pwned"—a gamer slang term derived from a misspelling of "owned"—means to be utterly defeated or controlled. When your account is "pwned," it means your login information has been exposed in a data breach and is likely in the hands of malicious actors.
HIBP allows you to quickly check if your email addresses or phone numbers have appeared in any of the compromised websites and accounts in its database.
How to Check if You've Been Pwned (A Step-by-Step Guide)
Finding out if your information has been exposed is simple and takes less than a minute.
- Visit the Website
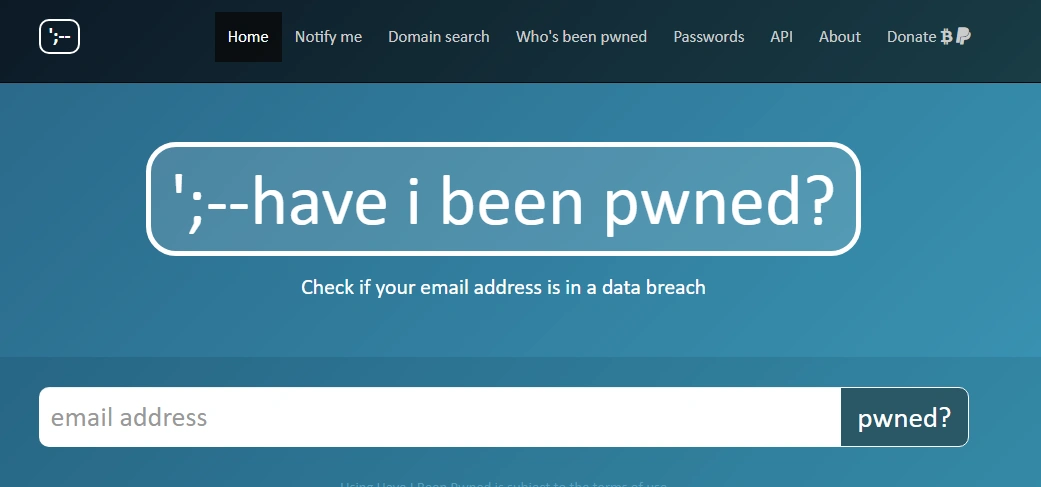
Navigate to the official Have I Been Pwned? website: https://haveibeenpwned.com/ - Enter Your Email Address
In the search bar, type in an email address you want to check and click the "pwned?" button.
The main search bar on the Have I Been Pwned? homepage. - Analyze Your Results
You will see one of two results:- "Good news — no pwnage found!" This means your email was not found in any of the breaches in HIBP’s database.
- "Oh no — pwned!" This means your email was found in one or more data breaches. The site will list exactly which breaches your data was a part of, what type of data was compromised (e.g., passwords, geographic locations), and the date of the breach.
I've Been Pwned! Now What? (Your 5-Step Action Plan)
If you saw the "Oh no — pwned!" message, don't panic. Discovering a breach is the first step to securing your digital life. Follow this action plan immediately.
Step 1: Change Your Passwords Immediately
This is your top priority. For every site listed in the breach results, change your password right away. If you reused that same password on other websites (a common mistake), you must change those as well. Your new passwords should be strong, unique, and at least 16 characters long.
Step 2: Enable Two-Factor Authentication (2FA)
Two-factor authentication is your single most effective defense after a password has been stolen. It requires a second form of verification (like a code from an app or a text message) before granting access. This means that even if a hacker has your password, they can't get into your account. Enable it on every critical account, especially email, banking, and social media.
Step 3: Scrutinize Your Emails for Phishing Attempts
Once your email is public, you become a prime target for phishing scams. These are fraudulent emails designed to look like they’re from legitimate companies (e.g., your bank, Netflix, or Slack) to trick you into revealing more information. Be hyper-vigilant. Never click on links or download attachments from unsolicited emails. Instead, go directly to the website or app in your browser.
Step 4: Consider a New Email for High-Stakes Accounts
For your most sensitive accounts (like banking, finance, or government services), consider changing the associated email address to one that you keep private and never use for general sign-ups. This isolates your most critical assets from the noise and risk of a publicly breached email.
Step 5: Monitor Your Financial Accounts
Keep a close eye on your bank and credit card statements for any unusual activity. If a breach included financial information, consider placing a fraud alert or credit freeze with the major credit bureaus (Equifax, Experian, TransUnion) as an extra precaution.
Proactive Protection: How to Avoid Being Pwned in the Future
- Use Strong, Unique Passwords for Every Account: The golden rule of cybersecurity. Never reuse passwords. If one site is breached, the damage is contained and hackers can't use that same password to access your other accounts.
- Leverage a Secure Password Manager: Manually creating and remembering dozens of unique, complex passwords is not humanly possible. A password manager is the solution. It generates, stores, and fills in your credentials securely, making perfect password hygiene effortless.
- Be Smart About the Services You Use: Before signing up for a new service, consider if you truly need it. The fewer places your data exists, the smaller your digital footprint and the lower your risk of exposure.
How TeamPassword Prevents Breaches for Your Business
For individuals, password security is a challenge. For a business sharing credentials across teams, clients, and contractors, it's a critical vulnerability. Emailing passwords or using spreadsheets is an open invitation for a breach.
TeamPassword is an affordable, robust password management solution designed for businesses.
- Safe & Easy Sharing: Securely share access without ever exposing the raw password.
- Built-in Password Generator: Instantly create and deploy strong, unique passwords across your organization.
- Enforceable Two-Factor Authentication (2FA): Ensure every member of your team has 2FA enabled, preventing unauthorized account access.
- Activity Logging & Notifications: Monitor who is accessing what and get instant alerts on sensitive accounts.
Don't let hackers pwn your company.
Frequently Asked Questions (FAQ)
1. Is "Have I Been Pwned" safe to use?
Yes, it is a highly respected and trusted security resource used by governments and Fortune 500 companies. It does not store the email addresses you search for.
2. If my email is found, does that mean my computer has a virus?
Not necessarily. A data breach happens on a company's servers (e.g., LinkedIn, Adobe). It means your data was stolen from them, not directly from your device. However, a breach can lead to phishing emails that could try to install malware on your computer.
3. Can a password manager be hacked?
Reputable password managers like TeamPassword use state-of-the-art, end-to-end encryption (often called zero-knowledge), meaning the company itself cannot see your passwords. A breach of their servers would only reveal encrypted gibberish. The biggest risk is a weak master password, which is why using a strong one and enabling 2FA is crucial.